1. Introduction
The need for cybersecurity is widely accepted, both by countries, companies or organizations, regardless of their size. In the aviation industry, the issue takes effect with Resolution A39-19, Direction of Cybersecurity in Civil Aviation [1] recognizing that the global aviation system is a highly complex and integrated system with critical information and technologies that depend on the availability, integrity and confidentiality of the data. In view of compliance with the ICAO established improvement plan until 2030 [2] and the implementation of the Global Aeronautical Information Management System (SWIM) [3], where it will be exchanged with global stakeholders such as airlines, aircraft, civil and military controllers, etc.
Block 1: Establish a solid Cybersecurity device to support information management.
Block 2: Manage the security, integrity, confidentiality and availability of the information that will allow mitigating the risks of intentional interruption and modification of air traffic management information that is critical to operational safety.
The increase in capabilities using cyber-attacks against information and communications systems and the concern of states regarding the possibility of attacks on the air traffic management system are recognized. Agreeing on the creation of groups of experts, the development of capacities to protect critical information, data technology and increase the resilience of the infrastructure, guaranteeing its maintainability and development. To this end, in 2020, CANSO published the standard of excellence in cybersecurity for air navigation services, supported by the practices proposed in NIST CSF, endorsed by the experience of its implementation in the European Union [5-7]. This presents a strategy for the continuous improvement of ANSP cybersecurity based on criteria of capacity and maturity (excellence).
This article is organized as follows: section II presents the results of the systematic review; section III presents the framework proposal for excellence in aeronautical cybersecurity that integrates the specific objectives of aeronautical cybersecurity with capabilities and requirements, contributing to raising the management of maturity in aeronautical cybersecurity. 13 objectives with 120 capabilities and 5 maturity levels are exposed to obtain 600 requirements broken down by maturity stages; in section IV the conclusions are presented.
2. Review of the state of the art
During the systematic review, the following terms that identify the research areas were considered: information security management system maturity, maturity cybersecurity and capability maturity cybersecurity. Among the selected sources are specialized databases such as IEEE, Science Direct, SpringerLink and Wiley Online Library. As a result, 28,138 publications regarding maturity in cybersecurity between 2018 and 2022 were analyzed. Of these, a group of 352 articles were considered relevant, identifying 23 primary articles within them. These articles, according to the Petersen criteria, were classified as: Solution proposals (Kour, Karim, Thaduri, & Transit, 2020), Evaluation searches (Kour et al., 2020), Opinion articles (Kour et al., 2020), Experience articles (Kour et al., 2020) and Philosophical articles (Kour et al., 2020). From their analysis, the following observations are made:
The non-standardization of the terms is maintained since each author uses different vocabularies for the same meaning.
The supremacy of the COBIT model for IT governance issues [29]. A tendency to use it in conjunction with other standards associated with cybersecurity such as ISO 27000 or NIST CSF was identified.
Although it is still a developing area, a moderate increase has been identified in the creation of models or frameworks more adapted to their realities, be in industries, institutions or countries. Mainly adapting existing models or creating new models and frameworks. Such is the case of airports, health, banking, the cloud or SCADA systems.
The concept of frameworks for maturity in cybersecurity has appeared in the literature. These are practical implementations of existing maturity models or concrete applications on specific areas. Although the use of the framework or model nomenclature is more conditioned to the area where it is developed since in its structure they do not present differences.
Both the models and the frameworks present objectives that are traceable to cybersecurity standards. Those, in turn, can be divided into capabilities that establish metrics, controls, or requirements.
It is observed that security controls when related to maturity levels only influence the way the process or control is carried out (depending on the characteristics of the level). Without establishing new cybersecurity requirements. Although there are models [10,20] where the complexity of the security requirements increases as a function of level maturity.
A small improvement is identified in the tools used to implement the models or frameworks. Where the main tools for its implementation and easy management are developed in MS-Excel files [20,21] although there are others that do it through applications for specific domains [8].
Several models [30-33] link organizational resilience to cybersecurity and define that cybersecurity requirements must be supported by good practices and standards associated with the area of competence.
3. Aeronautic cybersecurity framework
For the development of the proposal, the implementation of a framework is considered, seen as a broad overview or scheme of interconnected elements, which defines a standardized set of concepts, practices and criteria to focus on a particular type of problem [30,31]. They provide a base structure to organize the components of a process [34], including capabilities, rules and methods applicable to any scenario regardless of its size or complexity [35]. They define three levels of application from three perspectives: the executive, business process managers, and operations managers [36,37]. This will maintain the structure proposed in the standard for excellence in cybersecurity proposed by Canso, to which the capabilities layer was added and, consequently, the requirements layer was expanded.
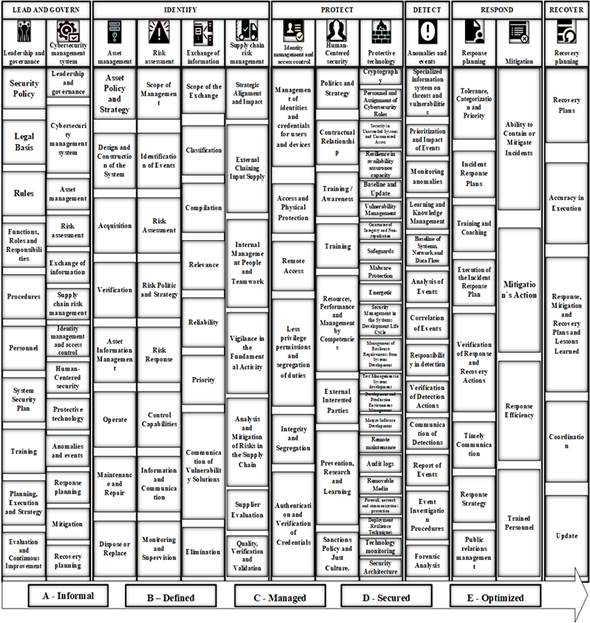
Fig. 1 exposes the simplified structure of the framework and the traceability between COBIT, NIST CSF, the standard for excellence in aviation cybersecurity [38], proposed by CANSO. It exposes 13 objectives, 120 capabilities and 5 maturity levels to obtain 600 maturity requirements.
3.1 Standard ratio and tired goals
Regarding the cybersecurity standards that the framework respects, those recommended by CANSO, that is, COBIT and NIST CSF will be maintained. COBIT for its results in the management of IT governance will be traceable with the Objectives:
Leadership and Governance: Where senior management demonstrates leadership and commitment to cybersecurity. Policies necessary to manage and monitor regulatory, legal, risk, environmental, and operational requirements related to cybersecurity are approved and help ensure that cybersecurity supports business objectives, optimizes business investment, and appropriately manages risks and opportunities related to cybersecurity.
Cybersecurity Management System: Where the elements that establish security policies, processes and objectives are related. Through a culture of security, it fosters cooperation between stakeholders, manages threat and risk assessment, and acts as an independent party to provide advice, audit systems and processes without having a direct role in the operation.
NIST CSF for its part will be traceable to the objectives:
Asset Management: Where the data, personnel, devices, systems and facilities that allow the organization to achieve its business objectives are managed according to their relative importance and their risk strategy.
Risk Assessment: Where the cybersecurity risk for operations is understood, including the mission, functions, image or reputation, assets and people. It includes managing threats and vulnerabilities and identifying control gaps for areas and managing the assessed risks.
Levels and stages of maturity and capability
Regarding the levels of maturity or capacity used in the framework, the following concepts will be added:
Stage: Period of fulfillment of requirements between one level and another.
Level 0) Incomplete: Where the requirements that allow cybersecurity to be considered at level A - Informal are not met.
Maintaining the levels proposed by fatigue as follows:
Level 1) A - Informal: Where the requirements are met to a large extent by the expertise of its members.
Level 2) B - Defined: Where compliance with the requirements is indicated and organized with an organizational vision.
Level 3) C - Managed: Where the organization documents the procedures, rules and responsibilities of its actors and establishes mechanisms to meet its goals.
Level 4) D - Secured: Where the cybersecurity results are interpreted through metrics, all the previous stages are consolidated through the automation of processes and formally involve the interested parties.
Level 5) E - Optimized: Where the organization seeks the continuous improvement of its cybersecurity through international practices. The system is able to quickly adapt to changes in terms of threats, vulnerabilities, risks, economic strategy or organizational needs.
4. Identification and validation by experts of the capacities and requirements by level
The foundations for building excellence are obtained by consolidating the requirements based on the level of maturity of the capability. These capabilities are grouped by their objectives, which have been established according to the characteristics of the maturity levels, while increasing their completeness and compliance, strengthened with specific standards, in organizational resilience and good practices identified in the literature. Therefore, knowing the objectives and levels, it was imperative to determine the security and resilience requirements to be implemented, as well as in what capacity to contain it and at what level of maturity.
To determine the requirements, the systematic review of the bibliography, the Delphi method and the focus group were applied as scientific methods The systematic review of the bibliography: Identifies, evaluates and combines the evidence of the primary research studies through an explicit and rigorous method. Being useful to evaluate and interpret relevant information available associated with an investigation [39].
The Delphi method: It is used internationally in several areas of knowledge; its purpose is to socialize, externalize and combine the knowledge of experts under anonymity, enabling the participation of geographically dispersed experts [40].
The focus group: it is a type of group interview to collect opinions and knowledge on a specific topic. Its application stimulates the members to emit ideas about the object under investigation and the interaction between them allows to consider additional aspects or identify common problems [41].
For the identification of requirements, a bibliographic review of standards, models, frameworks and articles on the subject was carried out. This information was enriched by particularizing it to the aeronautical environment with the help of experts, making use of the Delphi method in its first round. The results obtained were submitted to the focus group where the proposal was enriched with real experiences, proposing the capacities, the development of a software for the management of the framework, the Fig. 1. representing the stages and levels of maturity and the extension of the scope to others. standards not directly involved with cybersecurity but implementing them would provide good practices for the resilience of the organization. Finally, the second round of Delphi was applied with the proposal refined in the previous step.
For the systematic review, the one previously carried out in 1.3 was expanded by adding the requirements established in multiple standards and consolidated capacity and maturity models, such is the case of the ISO 27000 family [41], the NIST SP 800 series standards related to NIST Cybersecurity Framework (NIST CSF) Version 2.0 [42] or NIST SP 800-53 rev.5 [43], Cybersecurity Maturity Model Certification (CMMC) Version 2.0 [44], Cybersecurity Capacity Maturity Model for Nations (CMM) [45], Cybersecurity Capability Maturity Model (C2M2) Version 2.1 [46] and the Cybersecurity Framework Version 4.2 [47] implemented in Uruguay [48]. The relevance of the requirements found was validated by identifying recent scientific publications (5 years) that developed the topic.
There were 783 basic cybersecurity practices were determined, which were located at the corresponding maturity level and were developed observing the characteristics of the levels towards which they mature or the data necessary to guarantee their assurance at previous levels. Allowing the emergence and specification of new requirements, supported by the increase in complexity and completeness of said specifications for implementation.
These practices, once the framework has been adopted, are considered requirements for its implementation depending on the level to be reached. The capabilities arose from the accumulation of requirements on a specific capability within each objective. As the existence of few publications that issued clear criteria on requirements, capacities and objectives was identified, it was decided to submit the proposal to the first round of experts.
To apply Delphi and the focus group, it is necessary to identify experts in aeronautical cybersecurity. To this end, the following expert selection criteria were considered [49]:
Having performed roles related to cybersecurity.
More than five years of experience in cybersecurity and more than three years linked to aeronautical cybersecurity.
Having successfully managed improvements in cybersecurity in organizations related to aeronautics or other similar critical infrastructures.
Possess knowledge in the branches of engineering related to critical infrastructures, CNS/ATM, quality management, process improvement, methodologies, models and cybersecurity maturity standards.
Possess publications and industry recognition for their contributions to aeronautical cybersecurity.
For this reason, 27 candidates for experts from both the national industry and other service providers, aeronautical technique producers or international regulatory bodies were contacted. Twenty-one of them agreed to participate and had their curricular synthesis reviewed. Representing 9 organizations (5 Cuban and 8 foreign), with nationality from Cuba (14), Argentina, Chile, Mexico, the Dominican Republic, the Netherlands, the United States and Germany. Of the 21 experts, 6 whose competence indices were less than 0.5 were dismissed. Out the selected 15 experts, 12 obtained a high competence coefficient and 3 of them medium. Which were characterized to guarantee their quality for research.
Based on the correlation proposal between objectives, capabilities, requirements and levels, the first round of Delphi was carried out to adapt the proposal to the aeronautical context. Carried out through a virtual discussion group, supported by video conference, where the moderator informed that the purpose of the meeting is to identify the cybersecurity capabilities and requirements by level to be implemented in the organizations that ensure aeronautical services. The anonymity and confidentiality of the responses to the survey or criteria that will be obtained at the meeting was guaranteed.
To ensure the understanding of the experts, the moderator explains each objective and the maturity requirements by level, for each capability. In parallel, for each capacity explained, each expert receives a survey in which to assess, according to the Likert scale, their degree of agreement or disagreement, the relevance or otherwise of each capacity or its requirements by level. In addition, it allows you to propose changes for each question. In the first round, the experts proposed a total of 56 changes, which can be summarized in the following items:
They proposed 52 adaptations of requirements that were ahead of the characteristics of the level of maturity. Incorporating specialized standard practices in other capacities that are not exactly cybersecurity, these approaches are supported under the hypothesis that implementing standardized good practices in key capacities will contribute to increasing organizational resilience. And considering the complexity of implementation of the framework, the use of tools for its management.
Considering the results obtained through the expert method, they were submitted to an exploratory focus group, to which industry executives and other interested parties were added, which enriched the proposal with real experiences, also proposing the following recommendations for execution.
Use the ISO 55000 standard in the case of asset management, CMMi for software project development, ISO 28000 for supply chain security management and ISO 22301 for business continuity.
Develop a tool that allows the control of the complete management cycle of the improvements projected by the system of excellence in cybersecurity, which is compatible with the quality management systems and the operational safety management system and which can cover several organizations.
Once the proposal was updated considering the established recommendations, the second round of the survey was carried out. The experts once again gave their consideration on the practices, evidencing a higher level of consensus than in the first round and a greater acceptance of the proposal. The experts valued the use of the recommendations for the implementation of the framework, observing a high concordance with the proposals issued in the focus group (in all cases above 85%). To demonstrate the reliability of the answers given by the experts in the questionnaires, it was necessary to calculate the coefficient of agreement between them.
For the processing of the results of the survey, a method was used that consists of identifying the frequency in each category of the Likert scale defined in the survey and the percentages of concordance of each category are calculated according to the characteristics proposed by the author, then it is calculated in a percentage index, which integrates in a single value the acceptance of the group of evaluators on the characteristics of the model. The percentage index of the experts in each of the questions exceeds the value of 85. Therefore, the processing carried out through the Likert scale shows the acceptance by the community of experts of the objectives, capacities, levels and their requirements, as well as the software presented in support of the management of the framework for excellence in aeronautical cybersecurity.
From these analyses, it was possible to define the correlation between the cybersecurity and resilience requirements based on the level of maturity, for each capacity that makes up each of the objectives proposed in the standard of excellence for air navigation. Functional recommendations were determined that facilitate the management of the complete cycle associated with the necessary improvements to implement the framework and its interrelation with consolidated processes in the industry, such as Quality Management or Operational Safety Management [50].
5. List of objectives, capabilities and specification of requirements by level
Expanding on the results reached in the previous section, the correlation obtained between the objectives, capacities and requirements by level is presented, and references are made to articles found that validate the topicality of the topic.
Within the Leadership and Governance objective, the practices associated with ISO 38500 [51], GCSCC [52], CMM, ITIL and COBIT5 [53] are followed. The proposed capabilities to mature are: 1) Security Policy [54]; 2) Legal Basis [55]; 3) Rules [56]; 4) Functions, Roles and Responsibilities [57]; 5) Procedures [58]; 6) Personnel [59]; 7) System Security Plan [60]; 8) Training [61]; 9) Planning, Execution and Strategy [62] and 10) Evaluation [63] and Continuous Improvement [64].
In the Information Security Management System objective, the practices associated with ISO 27000, 27001, 27003 and 27004 [65] and the Standard of Excellence in Cybersecurity established by CANSO are adapted. As the purpose of this objective is to direct the management, it is proposed to maintain the following capacities 11) Leadership and Governance; 12) Information Security Management System; 13) Asset Management; 14) Risk assessment; 15) Exchange of information; 16) Supply chain risk management; 17) Identity management and access control; 18) Human-Centered Security; 19) Protective technology; 20) Anomalies and events; 21) Response planning; 22) Mitigation and 23) Recovery Planning.
In the Asset Management objective, the practices recommended in ISO 55000, 55001 and 55002 [66] are adapted, proposing the following capabilities: 24) Management Diagnosis [67]; 25) Asset Policy and Strategy [68]; 26) Design and Construction of the System [69]; 27) Acquisition [70]; 28) Verification [71]; 29) Asset Information Management [72]; 30) Operate [73]; 31) Maintenance and Repair [74] and 32) Dispose or Replace [75].
The Risk Assessment objective responds to the recommended practices in the ISO 31000 family, ISO 27005, NIST SP 800-30 [76] and Cyber Security and Risk Assessment Guide, proposing the following capacities: 33) Scope of Management [77]; 34) Identification of Events [78]; 35) Risk Assessment [79]; 36) Risk Response [80]; 37) Control Capabilities [81]; 38) Information and Communication [82] and 39) Monitoring and Supervision [83].
The Information Exchange objective provides the practices suggested by NIST SP 800-47 and ISO 20614 and ISO 27032 proposing as capabilities: 40) Scope of the Exchange [84]; 41) Classification [85]; 42) Compilation [86]; 43) Relevance [87]; 44) Reliability [88]; 45) Priority [89]; 46) Communication of Vulnerability Solutions [90]; and 47) Elimination [91].
In the Risk Management objective in the supply chain, the practices of ISO 28000 and 28001 are adapted, proposing the capacities: 48) Strategic Alignment and Impact [92]; 49) External Chaining Input Supply [93]; 50) Internal People Management and Teamwork [94]; 51) Surveillance in Fundamental Capacity [95]; 52) Analysis and Mitigation of Risks in the Supply Chain [96]; 53) Evaluation of Suppliers [97] and 54) Quality, Verification and Validation [98].
The Identity Management and Access Control objective complements the practices declared in ISO 29146, NIST SP 800-205 and the ISO 24760 family, for which reason it proposes the following capabilities: 55) Management of identities and credentials for users and devices [99]; 56) Access and Physical Protection [100]; 57) Remote Access [101]; 58) Permits with less privilege and segregation of duties [102]; 59) Integrity and Segregation [103] and 60) Authentication and Verification of Credentials.
The Human-Centered Security objective uses the success factors declared in ISO 27501, ISO 30408, NIST SP 800-181, ICAO Manual 9859 and 10057 and the CANSO Human Resources Management Excellence Model, at the same time that proposes as capacities: 61) Politics and Strategy; 62) Contractual Relationship; 63) Training / Awareness [104]; 64) Training; 65) Resources, Performance and Management by Competencies [105]; 66) External Interested Parties; 67) Prevention, Investigation and Learning [106] and 68) Sanctions Policy and Just Culture.
In the Protective Technology objective, recommended practices are included in NIST SP 800-160, NIST SP 800-40, NIST SP 800-86, CMMi, ISO 62443 data protection [106], the maturity model for web applications against cyber-attacks based on in OSWAP [107], and the Action Plan for the implementation of an ICAO Cybersecurity Strategy, the proposed capabilities are: 69) Cryptography [108]; 70) Personnel and Assignment of Cybersecurity Roles [109]; 71) Security in Unattended Systems and Unconnected Assets [110]; 72) Resilience in capacity to ensure availability [111]; 73) Baseline and Update [112]; 74) Vulnerability Management [113]; 75) Guarantee of Integrity and Non-repudiation [114]; 76) Safeguards [115]; 77) Antivirus Protection [116]; 78) energetic; 79) Security Management in the Systems Development Life Cycle; 80) Management of Resilience Requirements from Systems Development; 81) Test Management in Systems development; 82) Development and Production Environment Management; 83) Mature Software Development; 84) Remote maintenance; 85) Audit logs ; 86) Removable Media [117]; 87) Firewall, protection of networks and communications [59]; 88) Deployment Resilience Techniques [118]; 89) Technology Monitoring [119] and 90) Security Architecture [120].
The Anomalies and Events objective uses the success factors declared in NIST SP 800-92, NIST SP 800-94 and NIST SP 800-137 and the maturity-oriented model in forensic analysis [121] to propose the capabilities: 91 ) Specialized information system on threats and vulnerabilities; 92) Prioritization and Impact of Events; 93) Monitoring of anomalies [122]; 94) Learning and Knowledge Management [123]; 95) Baseline of Systems, Network and Data Flow; 96) Analysis of Events; 97) Correlation of Events; 98) Responsibility in detection; 99) Verification of Detection Actions; 100) Communication of Detections; 101) Report of Events; 102) Event Investigation Procedures and 103) Forensic Analysis.
The Response Planning objective includes success factors declared in CSFPC, NIST 800-61, ISO 27035, ICAO Doc. 9756 and the CANSO Emergency Response Plan, to present the capabilities: 104) Tolerance, Categorization and Priority; 105) Incident Response Plans [124]; 106) Training and Training [104]; 107) Execution of the Incident Response Plan; 108) Verification of Response and Recovery Actions; 109) Timely Communication; 110) Response Strategy and 111) Public relations management.
The Mitigation objective bases its capabilities on the success factors declared in ISO 22316, ISO 22317 and BSI 65000 proposing: 112) Ability to Contain or Mitigate Incidents; 113) Mitigation Actions; 114) Response Efficiency and 115) Trained Personnel [104].
Finally, the Recovery Planning objective is supported by the ISO 22301, ISO 22313 and ISO 24762 standards, it presents the following capabilities: 116) Recovery Plans; 117) Accuracy in Execution; 118) Response, Mitigation and Recovery Plans and Lessons Learned [125]; 119) Coordination and 120) Update.
Each capacity will present requirements that will gain in completeness and complexity depending on the level of maturity that is intended to be obtained. The levels to be used were those previously explained. Therefore, the framework will have 600 requirements, 120 for each defined level except for the Stage or Incomplete Level where all the minimum requirements have not yet been met to reach level A - Informal.
Each requirement is correlated with a level and with a capacity, these may have 3 states: 1) Pending: When all the requirements proposed for a stage are not met, the organization is not able to provide evidence of compliance and its implementation is not projected. compliance. 2) In process: When the organization has projected its compliance through actions, tasks and the necessary assurance for its compliance. 3) Fulfilled: when the institution is capable of providing evidence of compliance with all the requirements stipulated in the stage and the level of maturity evaluated. Evidence of compliance will serve as the basis for determining the state of maturity of the organization and a source of comparison between entities. To use the framework, the following constraint is used:
Restriction 1: It is only possible to declare a requirement fulfilled when all the requirements of previous stages are fulfilled.
6. Conclusions
In conclusion, this article has presented a framework for the management of aeronautical cybersecurity maturity, based on a systematic review of publications and enriched with good practices provided by executives and experts in the industry. The framework includes 13 objectives, 120 capabilities, and 5 functional levels of maturity, with a total of 600 requirements that can be used to achieve maturity levels in a certifiable and gradual manner. The framework not only contributes to improving the resilience of aeronautical infrastructures, but also enhances their integration with other management systems such as security, quality, or safety. This framework represents an important step forward in the development and implementation of effective cybersecurity management practices in the aeronautical industry.