Introduction
The penetration of virtual spaces into the daily lives of adolescents provides opportunities for communication, entertainment, education and new forms of socialization, but also entails potential risks. One of these risks is gender cyber-violence. This phenomenon has increased in recent years, according to various organizations (EIGE, 2017; EVAW, 2013; INE, 2014).
There is no consensus on the definition of gender cyber-violence (EIGE, 2017). One way of understanding the phenomenon is as the extension of violence against women into virtual space, defined by the United Nations, in its Declaration on the Elimination of Violence against Women (1993), as any act of gender-based violence that results in, or is likely to result in, physical, sexual or psychological harm or suffering to women, including threats of such acts, coercion or arbitrary deprivation of liberty, whether occurring in public or in private life. The internet provides the opportunity to repeat existing patterns of gender violence, acquiring new forms derived from its immediacy, accessibility, anonymity, and lack of contextual information.
From another perspective, gender cyber-violence can be understood as a particular form of cyber-aggression (Alvarez et al., 2017; Reyes et al., 2018; Torres, 2013) related to the use of virtual communication to damage, disturb or intentionally harm people or groups. The other side of cyber-aggression is cyber-victimization. Usually the terms “cyber-aggression” and “cyber-victimization” are used to refer to situations in which someone perpetrates or suffers, respectively, aggression through electronic communication devices (Corcoran et al., 2015). Thus, under this view, gender cyber-victimization is associated with the many forms of violence suffered by women in virtual spaces (EIGE, 2017; EVAW, 2013). This can manifest itself in the shape of cyber-bullying, cyber-dating violence (behaviors including the use of digital media to monitor, control, threaten, harass, pressure, or coerce a dating partner), pornographic revenge, gender insults, sexting without consent (sending, receiving and forwarding sexually suggestive or explicit images, videos or text messages), threats of sexual extortion, or doxing (public online dissemination of someone’s private data). Martínez and Ortigosa (2010), and more recently Gini et al. (2019), identify a long list of behaviors that seek to isolate and track the cyber victim. Sanjuán (2019), in Save the Children, shows the relationships between the different forms of cyber-violence. A definitive list is difficult to draw up, however, since constant technological development means that new forms of online harassment are continually appearing.
We see cyber-victimization as a specific type of victimization that should be treated as a separate construct, although there is a strong correlation between this form of violence and traditional victimization (Núñez et al., 2021). Cyber-victimization is the fact of suffering prolonged, repeated aggression perpetrated by means of electronic devices. Further, victims cannot easily defend themselves and the aggression persists without needing to be repeated due to the characteristics of the virtual medium.
Some effects of cyber-victimization are: symptoms of depression, lack of concentration, problems in academic performance (Semenza, 2019), prolonged anxiety, suicidal thoughts, somatization (Alvarez et al., 2017; Penado & Rodicio, 2018), loss of control, fear, low self-esteem, self-harm (Eckert & Metzger, 2020), and social isolation (Espin et al., 2017). In addition, Sanjuán (2019) identifies a long list of the possible consequences of cyber-violence.
Prevalence of cyber-violence
Research and data on gender cyber-violence and gender cyber-victimization are scarce and, consequently, very little is known about the actual percentage of victims and the prevalence of the harm caused (Dimond et al., 2011; EIGE, 2017). Most of the literature focuses on cyberbullying among adolescents (Backe et al., 2018). Also, as in cyberbullying studies, the results are inconsistent and often not easily comparable, as researchers have used different parameters to measure the phenomenon (Rivers, 2013), which makes it difficult to establish the real prevalence rates of gender cyber-violence (Backe et al., 2018). Particularly, most studies have focused on two aspects: the type of cyber-violence suffered and the gender of the victim (Alvarez et al., 2017).
Types of cyber-violence
Díaz (2014) identified the following types of gender cyber-violence: intimidation by mobile phone, tracking on WhatsApp, identity theft using passwords given in confidence, and publishing images on the internet without consent. In a study by Mindrila (2019), 28% of US students aged 12 to 18 reported being victimized, while 9% reported being cyber-victimized. In Spain, a systematic review of 21 studies showed that the average prevalence of cyber-victimization was 26.65% (Zych et al., 2016).
Zapor et al. (2017) found that 73% of males and 77% of females had committed at least one act of online psychological aggression against their partner during their relationship. Similarly, Rodríguez-Castro et al. (2018) found that both males and females tracked their affective partners using their electronic devices, although there was a higher prevalence among women. Jealousy and distrust towards sentimental partners seem to be the main reasons for exercising such cyber-monitoring. In a study carried out by Martínez-Pecino and Durán (2019), 48.4% of participants reported having cyberbullied their partners during the previous year via mobile phone and 37.5% via Internet. Males reported cyberbullying their girlfriends to a greater extent by both means.
An international meta-analysis (Madigan et al., 2018) found a prevalence rate of sexting between 14 and 27% among individuals aged 12-17. In Spain, Villacampa (2017) reported a prevalence of 7.9% in young people between 14 and 18 years, while Gámez-Guadix et al. (2017) observed a prevalence of 13.5% in young people aged 12 to 17. Rodríguez-Castro et al. (2018) found that sexting is a common practice among adolescents of both genders and also in the context of a relationship. Boys’ main reasons for sexting were to achieve a sexual relationship, whereas girls’ motivations were to have or maintain an emotional relationship.
Gruyter (2013) showed that what they termed “popular controversial” adolescents were significantly more likely to make or send threatening or insulting voice calls or text messages than others. In addition, a significant interaction effect with gender was found for mobile phone gossiping; popular controversial girls were more involved in gossiping than popular controversial boys. Fierro et al. (2013), in their study of young people aged 13 to 18, reported that 12.3% of the sample received calls or messages from peers with insults or threats via mobile phone or computer, while 14.2% stated that they had sent such messages.
As for doxing-related violence, the study by Chen et al. (2019) reported that 53.2% of adolescents admitted doxing people they were attracted to. In the case of Spain, according to Amnesty International (cited by Pantallas Amigas, 2021), 26% of Spanish women who had suffered abuse on the internet affirmed that they had been victims of doxing.
Gender-related differences in cyber-violence
From a gender perspective, existing studies depict certain contradictions. Working for Halt Online Abuse (WHOA, 2012), Elipe et al. (2012) and Calvete et al. (2010) found that most internet harassment victims were women, especially in cases of tracking. For their part, Staude-Müller et al. (2012) observed that the likelihood of women being victims of online sexual harassment and stalking was significantly higher. In line with this, the Pew Research Center (2014) found that men had a higher probability of suffering “light” forms of online harassment, such as insults or embarrassment, while women (especially those aged 18 to 24) faced severe forms of cyber-harassment and were particularly prone to online stalking and sexual harassment. Additionally, Strassberg et al. (2017) identified that men were more involved in sending, receiving and forwarding messages of a sexual nature to third parties, while Chen et al. (2019) reported that more men than women were shown to diffuse personal identification and physical location information and other types of private and sensitive data. Moreover, Citron (2014) concluded that women were more likely to experience other sexualized forms of online harassment such as revenge porn. Supporting these findings, Estébanez and Vázquez (2013) found that girls on the internet were more vulnerable and at greater risk of harassment than boys. In their online profiles, girls tended to speak about more personal and private situations, they exposed themselves more than boys and received more friend requests, more approaches from strangers and more sexual propositions, and they were aware of competitions where their bodies were assigned scores. Apart from this greater exposure, there were differences in situations of violence, since male individuals minimized the aggressions they inflicted, while females minimized those they received.
In conclusion, although these forms of cyber-violence can be suffered both by men and women, women are at greater risk (Sanjuán, 2019). The findings of these studies show the limitations of adopting an approach that does not take gender issues into account when dealing with cyber-violence (EIGE, 2017). Based on this, EIGE affirms that more research is required in different areas of gender cyber-violence, especially in identifying and analyzing risk factors, since this may help prevent harm and “re-victimization.”
The present study
The study presented here sees gender cyber-violence as a specific form of cyber-aggression or cyber-victimization and takes a gender perspective that particularly stresses variables related to the transgression of patriarchal norms, which also extend violence to men (Arisó & Mérida, 2010). Our goal was to identify technological, cognitive and behavioral factors associated with gender cyber-victimization among adolescents aged 12 to 14. This is a little-studied age range in gender cyber-violence, although it has been the subject of numerous studies on cyberbullying (Kowalski et al., 2014; Ortega et al., 2016; Torres, 2013).
Technological factors (the use of virtual spaces and digital skills for cyber-security)
Young people spend large amounts of time in digital spaces (Buckingham & Martínez-Rodríguez, 2013). Also, they use a large number of media and platforms. According to recent studies on the use of social media in Spain (AIMC, 2019) the most frequently used are WhatsApp, YouTube, Instagram, Facebook, Twitter, and Snapchat. This habitual presence in cyberspace, opening up private areas and making abundant use of the internet, can be identified as key risk factor for suffering cyber-victimization (Cohen & Felson, 1979; Kowalski et al., 2014; Reyns, 2010). In this setting, cyber-security has been identified as one of the key digital competences by the European Union (Ala-Mutka, 2011; Ferrari, 2012). This competence involves the safe and critical use of information technologies and the protection of devices, personal data, health and the environment. One of these areas, the protection of personal data, is particularly relevant to cyber-violence. It involves knowing how your information can be shared, how to manage privacy options in networks, how to disable your smartphone geolocation to avoid tracking and how to manage passwords, among other practices (Castillejos et al., 2016; Lee, 2014). Despite the common idea that “digital natives” have numerous digital skills, this group is not homogeneous (Akçayır et al., 2016), since many young people have deficits in these skills and thus may be exposed to threats and cyberbullying.
Cognitive factors (perception of risk in social networks activities and beliefs around gender cyber-violence)
Teenagers upload selfies and videos to the social networks and publish their profiles to achieve more views and followers. They also consent to chatting with other young people they have never met (Estébanez, 2018). In such cases, adolescents have difficulties establishing clear limits between the public and the private when identifying which data, comments and photos should be accessible only to their closest friends (Echeburúa & Requesens, 2012; De-Ridder & Van-Bauwel, 2015; Sánchez et al., 2015). Adolescence is a period of life in quest of identity and models, in which belonging to a specific group and being appreciated by one’s peers are crucial to self-esteem; and these factors carry greater weight than the perception of risk in digital spaces. Accordingly, Díaz (2014) and Martínez et al. (2013) found that half of young people did not see as dangerous actions such as giving names and surnames, accepting unknown people as friends, or even uploading personal images. Catalina et al. (2014) found that people with a higher awareness of risk on the internet tended to protect themselves from online dangers, while those with low-risk awareness did not. As Morduchowicz (2010) remarks, young people have located their private lives in society’s most public space, and there is no unequivocal relationship between knowledge of risk and actual behavior (Martínez et al., 2013).
Adolescents’ concept of what constitutes gender violence can make them vulnerable. Not being aware of what violent behavior actually comprises predisposes an individual towards suffering from it; as some studies report (Fass et al., 2008; Fundación ANAR, 2014), many adolescents who experience gender violence do not see themselves as victims. Díaz (2014) found that 76% of young people thought that tracking their partner did not constitute gender violence. Also, Centro Reina Sofía sobre Adolescencia y Juventud (2017) found that many behaviors, such as checking the partner’s mobile phone or tracking what they were doing, were very common. Estébanez (2018) suggests that idealizations of love could make relationships between teenagers leans towards dependency and normalize the monitoring of their partners as displays of love. Besides, according to the same author, not conforming to models of beauty or hypersexualized stereotypes conveyed by the social media may be a risk factor in suffering victimization.
Behavioral factors (responses to cyber-violence)
In studies on bullying and cyberbullying, various researchers (Elipe et al., 2012; Estévez et al., 2010) have found cyber-victimization and cyberbullying combined the same person as both victim and aggressor. Consequently, studies on bullying in traditional contexts have revealed a relationship between being a victim of bullying and becoming an aggressor (Avilés et al., 2011; Rodkin & Berger, 2008). In offline harassment the roles are more differentiated: one is the person perpetrating the violence and the other is the sufferer. In contrast, these roles are not so clearly differentiated in online interactions (Law & Hymel, 2012). The possibility of reacting to harassing messages received in social networks by publishing similar comments on the aggressor’s profile enables cyber-violence to become interpersonal, thus turning it into reciprocal cyber-aggression. Other studies (ANAR, 2017) have highlighted the passivity of cyber victims, which is linked to low self-esteem, depression, apathy, fear and mistrust in an educational system that has proven to be ineffective in the fight against violence and cyber-violence, factors that may explain such lack of reaction.
Based on the literature cited above, we expect to find:
An effect on gender cyber-victimization when there is greater use of social networks and when subjects have fewer digital competences for protecting themselves online (hypothesis 1).
An effect on gender cyber-victimization when subjects have a restricted concept of what constitutes gender violence (particularly in terms of partner tracking) and when they have a lower perception of risk in their social network activities (hypothesis 2).
An effect related to the victim’s behavior, which will be similar to that of the aggressor (hypothesis 3).
Method
The study consisted of a survey using an online questionnaire titled Gender Violence 2.0 Questionnaire (Donoso et al., 2014). This was administered to the adolescents selected for the study, who were grouped by classroom and answered the questionnaire online on their school computers, with a member of the research team present to provide help, if needed. Informed consent forms were requested for each participant. The average time spent to answer the questionnaire was 30 minutes. All methodological decisions were taken in accordance with the guidelines of University of Barcelona Good Research Practice Code (2010).
Instrument
The questionnaire applied to participants was made up of two scales, 6 questions with different response options, and sample description data.
Scales
Two scales were designed for this study: one that measures young people’s concepts about gender-related cyber-violence (Concept of Gender Cyber-Violence Scale) and another to measure the degree to which gender cyber-violence has been suffered (Gender Cyber-Victimization Scale). The variables of both scales put special attention to variables associated with the transgression of patriarchal norms, a system that assigns social roles and behavioral rules to genders (Arisó & Mérida, 2010; Cantera, 2007; Mullender, 2000). These variables are: deviating from the norms of female sexuality (being provocative, having various partners, lacking inclination to have a relationship); going against compulsory heterosexual norms (homosexuality, transsexuality); imposed the heteronormative model of beauty (deviating from feminine/masculine norms of beauty or hyper-sexualization); sexual violence (direct and indirect sexual harassment); and violence associated with the myths of romantic love (faithfulness, jealousy, possessiveness).
The metric characteristics and the items of both scales are presented below.
Concept of Gender Cyber-Violence Scale: This is a Likert-type scale with five response levels, comprising 5 dimensions previously exposed and 15 items, with a high level of internal consistency (Cronbach’s alpha of 0.931) and content validity, detailed in Donoso et al. (2015). The scale has items such as “gender cyber-violence is harassing a girl on the internet for having more than one partner,” “gender cyber-violence is ridiculing someone on the internet because of their sexual orientation,” “gender cyber-violence is sending images with sexual content about a person without their consent,” “gender cyber-violence is posting humiliating photos or videos of obese or ugly girls in internet or by mobile,” and “gender cyber-violence is repeatedly checking by internet or mobile where the partner is and what they are doing.”
Gender Cyber-Victimization Scale: This is also a Likert-type scale with response five levels, comprising 5 dimensions previously exposed and 15 items, again with a high level of internal consistency as measured by Cronbach’s alpha (0.912). The scale uses the same items as the previous scale. For example: “I have been harassed on the internet for having several sentimental partners.” >
Questions
The following types of questions relating to the object of study were included:
Use of digital environments by young people: seven three-point scale questions showing different social networks which the sample habitually used.
Digital competencies for protection against cyber-violence: dichotomous question made up of 6 dichotomous items in which the perception of mastery of aspects of online security, such as “knowing how to block people” or “knowing how to change privacy settings in social networks,” are shown. The dichotomous responses were converted into a score representing the degree of competence.
Perception of risk in online environments: scale of eight five-point items showing behaviors such as “uploading personal photos” or “chatting with strangers.” Internal consistency measured by Cronbach’s alpha yielded a score of 0.772.
Perception of features of one’s own vulnerability: dichotomous question made up of nine items and a dichotomous response in which the perception of having some feature of vulnerability and specific characteristics, such as “body type” or “skin color,” are shown. The dichotomous responses were converted into a score representing the degree of perceived vulnerability.
Having undergone cyber-victimization through the internet or mobile phone: dichotomous question.
Victims’ reactions to cyber-violence: dichotomous question with various levels including passive and active responses, for example, “I didn’t do anything,” “I did the same to him,” “I asked him to stop,” or “I blocked him.” The dichotomous answers were recoded into a variable representing the degree of activity/passivity of the reactions.
Sample description variables
Information about the variables sex, age, school year, sexual orientation, and whether or not the respondent had a partner were included.
Sample
The sample comprised 4,536 adolescents from six Spanish regions: the Balearic Islands (16.9%), Catalonia (21.5%), Galicia (13.9%), Andalusia (29.3%), Aragon (9.8%), and the Canary Islands (8.5%). The sample selection process took place in two stages. First, high schools in each of the regions were chosen through random sampling. Afterwards, students from the third and fourth years at each school were selected. Access was obtained by contacting the management of each school. The margin of error was ± 0.014 for a confidence level of 95.5% for infinite populations, where p and q = 0.5.
51.2% of the sample corresponded to female students and 48.8% to male students. All of them were attending their third or fourth year of high school (49.6% and 50.4%, respectively) and had an average age of 15. Most participants stated that they were heterosexual (90%) and 26% of the sample reported having a partner.
Data analysis
The SPSS (v18) statistical package was used to analyze the data. Descriptive and inferential statistics was used to perform a descriptive analysis of the responses obtained and to identify and explore the tendencies of the variables linked to cyber-victimization.
Additionally, the following two techniques were applied in order to identify factors associated with cyber-victimization:
A multiple linear regression analysis, whose aim was to find the best model to explain the relationship between a dependent variable, the degree to which the young people had been cyber-victimized —measured by the Gender Cyber-Victimization Scale—, and a set of explanatory variables or covariables (use of the internet, digital self-protection skills, concept of gender cyber-violence, number of perceived vulnerability features, reactions to cyber-victimization).
A two-step cluster analysis (Pérez, 2011), aimed at finding the best model to classify and characterize the young people victimized based on six variables obtained from the Gender Cyber-Victimization Scale, consisting of the five dimensions of the scale (deviating from the norms of female sexuality; going against the norms of compulsory heterosexuality; imposed heteronormative models of beauty; sexual violence; and violence associated with myths of romantic love) plus the scale total.
Results
Descriptive analysis
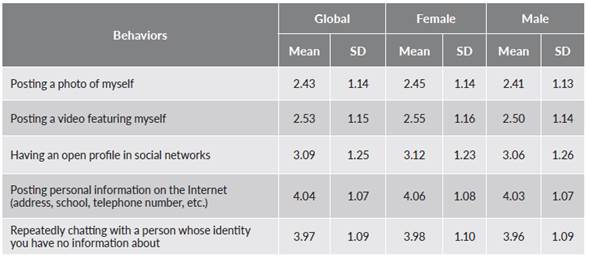
Regarding the adolescents’ technological profiles, the virtual environments they most used were generally WhatsApp, YouTube and Instagram. 90.3% of the participants said they used WhatsApp every day, 61.4% YouTube, and 58% Instagram. Apart from these social networks, the most frequently used was Facebook, with 34% every day. The specific online behaviors which participants saw as dangerous were, in the first place, posting personal information on the internet, followed by repeatedly chatting with an unknown person. The lowest risk was associated with posting photos or videos online (table 1). These results are not statistically significant when comparing male and female responses (t = 1.404; p = 0.160, respectively).
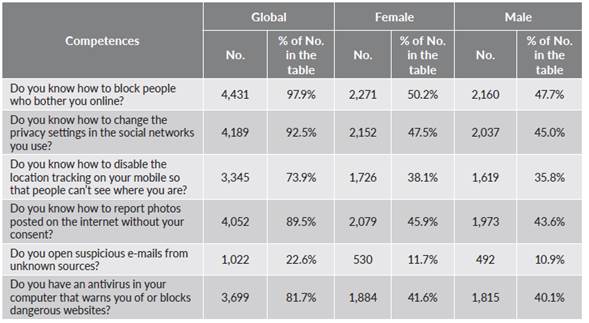
Turning to digital competences for internet security, it is of note that a large percentage of the sample considered that they possessed such skills, as shown in table 2. The best-known functions were blocking people and configuring social network privacy settings. The least-known was disabling the location feature on their mobile phone, although it should be noted that most stated that they knew how to do this. In short, the average number of security competences that the participants saw themselves as having was five out of the six mentioned in the survey. These results are not statistically significant when comparing male and female responses in the scales of scores representing the degree of competence (t = 0.500; p = 0.617, respectively).
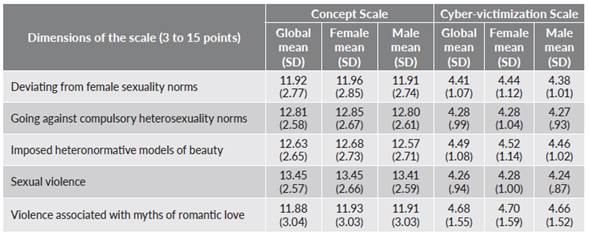
Participants had a strong awareness of what online gender violence is, therefore, they were able to identify violent behaviors (table 3). The behavior seen as least violent was that around deviance from the norms of female sexuality, such as a girl alleged to have more than one partner, a ‘provocative’ girl, or one not inclined to have a relationship. Lastly, online tracking of partners was also not seen as violence. The types of violence that victims endured were mostly related to the same situations, i.e., the teenagers in the sample suffered gender cyber-violence mostly relating to myths of romantic love in the partner and with the imposition of heteronormative models of beauty (table 3); in other words, girls whose physical appearance did not fit in with the culture of hyper-sexualization or who were treated as sexual objects, suffered the most cyber-violence.
These results are not statistically significant when comparing male and female responses, both in the concept scale (t = 0.801; p = 0.423) and in that of cyber-victimization (t = 1.578; p = 0.115). This is a finding that, surprisingly, obliges us to downplay gender as a factor in cyber-victimization.
The adolescents acted in different ways when confronted with situations of gender cyber- violence. Most, when they were victims, reacted passively. A minority showed more active responses, asking the aggressor to stop, or taking on the role of aggressor and returning the action.
Factors associated with gender cyber-victimization
Multiple linear regression analysis
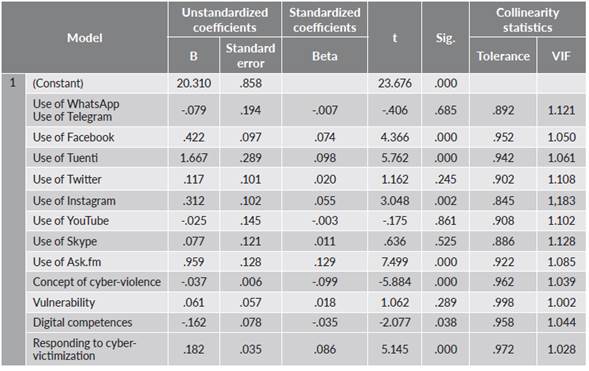
A multiple linear regression analysis was made in order to identify the factors involved, taking the total of the cyber-victimization scale as the dependent variable. A model with 7% variance was identified, a figure indicating that there is a wide variety of situations of cyber-victimization and that, therefore, this is a phenomenon whose high level of complexity largely hinders the identification of stable patterns enabling its prediction. Criteria for normality, linearity, homoscedasticity, independence and non-collinearity of residues (table 4) were taken into account. The model of regression identified as significant (F = 21.772; p = 0.000) has cyber-victimization as its dependent variable (metric score obtained from the Gender Cyber-Victimization Scale 2.0) and 12 independent variables. The resulting model is set out in table 4, which shows that all the independent variables are included in the model, although only 7 of these are significant. Thus, the following cyber-victimization factors were identified, arranged in descending order of weight in the model:
Using Tuenti
Using Ask.fm
Using Facebook
Using Instagram
Responding to cyber-victimization more proactively
Having few digital competences
Having a restricted concept of gender cyber-violence: identifying fewer behaviors as violent.
According to the model obtained, the factors that favored suffering gender cyber-victimization were firstly being a frequent user of platforms such as Tuenti, Ask.fm, Facebook and Instagram. Secondly, cyber-victimization was more likely when more proactive responses were given, such as “I asked him/her to stop” or “I did the same to him/her.” These more aggressive responses can create a cyber-violence feedback loop. Finally, other factors favoring cyber-victimization were having few digital skills and having a concept of cyber-violence restricted to only very obvious behavior, thus seeing some forms of violence as natural and normal.
Two-stage cluster analysis
To identify the cyber-victimization profiles we made a two-stage cluster analysis, which enabled a first exploratory approach to the phenomenon. Given the wide variety of gender cyber-violence, being able to identify a range of profiles was essential. For the two-step algorithm, six variables obtained from the Gender Cyber-victimization Scale were included in the analysis, consisting of the five dimensions of the scale plus the scale total. This algorithm generated two clusters with a good quality index (silhouette measure of cohesion and separation = 0.5), as presented below:
Cluster 1, titled Other profile. Size: 92.7% (4.204)
Cluster 2, titled Cyber-victim profile. Size: 7.3% (332).
The differences between the two profiles in the cyber-victimization scale and its dimensions are statistically significant (t = -28.57, p = 0.000;
t = -22.44, p = 0.000; t = -17.61, p = 0.000;
t = -21.85, p = 0.000; t = -17.02, p = 0.000;
t = -25.08 p = 0.000, respectively).
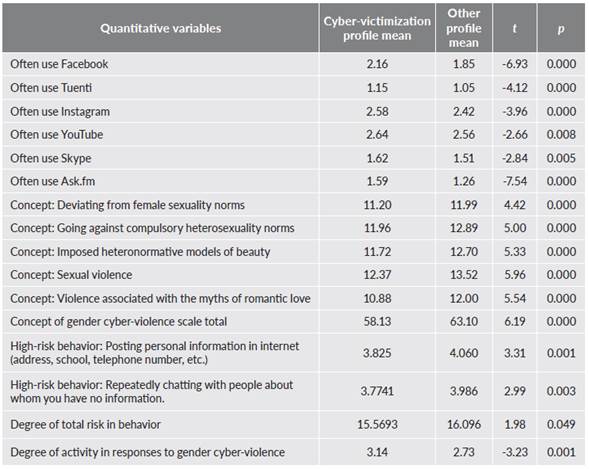
Compared with the other young people, the profile which scored highest on the cyber-victimization scale, and which thus showed the most frequent experiences of gender cyber-violence, also showed a different profile in other scale variables. Although the cyber-victimization profile contained more girls than boys (56 % and 44 %, respectively), the differences were not statistically significant (X2 = 3.32; p = 0.068). Tables 5 and 6 summarize the variables with statistically significant differences between the two groups. The data are presented separately for qualitative and quantitative variables according to the statistical test used. Specifically, the profile of people seeing themselves as victims of gender cyber-violence had the following features, compared with other participants:
They made more frequent use of resources such as Facebook, Tuenti, Instagram, YouTube, Skype, and Ask.fm
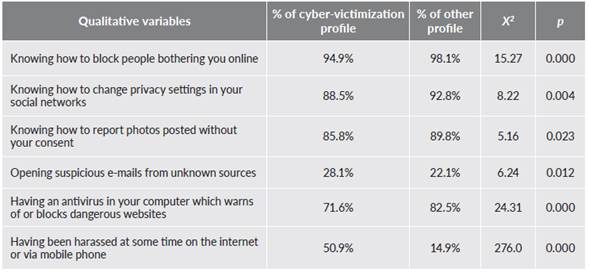
They had fewer digital competences in general; hence, they knew less about blocking people who bothered them online, changing privacy settings in their social networks and reporting photos posted without consent. Also they more often opened e-mails of suspicious provenance, and had fewer antiviruses in their computers to warn of or block dangerous websites.
In general, they were less aware that some of their online conduct might be risky, and they particularly believed that there was little risk in posting personal information on the internet (address, school, telephone number, etc.) and repeatedly chatting with people about whom you have no information.
They stated that they had been harassed on the internet or mobile phone much more frequently.
They had a much more restricted concept of online gender violence in general, in addition to each of the specific dimensions measured, i.e., they perceived a lower number of violent behaviors to be so.
Their response to cyber-victimization was much more active, doing the same to the cyber-aggressor or asking him/her to stop.
Table 5. Features of the two profiles: cyber-victim and other (quantitative variables)
Source: authors.
Table 6. Features of the two profiles: cyber-victim and other (qualitative variables)
Source: authors.
Once again, gender does not seem to appear as an important variable characterizing the groups. Although there was a slightly higher proportion of females in the cyber-victimization cluster, this was not statistically significant compared to males (X2 = 3.115; p = 0.078).
Discussion
This study has contributed to the research and literature on gender cyber-violence among adolescents from the perspective of victimization and using a gender approach. The results show that participants saw most of the actions included in the survey as violent, although less so when related to tracking the sentimental partner and deviating from established female sexuality norms, findings that are consistent with those of other studies (Blanco, 2014; Díaz, 2014; De-Miguel, 2015; Estébanez, 2018). The prevailing cultural models in the domain of love still convey the idea of the possession and control of the partner, especially among the youngest. The media can exert an influence in this area through films, advertisements and video games, portraying affective relationships in terms of the myth of romantic love (Bosch et al., 2013).
The adolescents in the sample who were victimized also suffered in factors mainly related to attempts to control their partners and with the imposition of heteronormative models of beauty. The existing literature also shows the prevalence of cyber-violence in attempts to control the partner. A study by Durán and Martínez (2015) found that 57.2% of participants (young university students) had been victimized by their partner on their mobiles (through ridicule, insults or spreading false rumors). In a study of young people between 14 and 21, Sánchez (2014) identified that the most repeated acts were tracking the time that the partner was online and monitoring the speed with which messages were answered, at 32% and 44%, respectively. In none of these studies, nor in ours, differences according to gender were found, thereby demonstrating the two-way nature of such attempts to control the partner, which is consistent with the literature on the subject (Burke et al., 2011). Despite the limited number of studies, the main conclusion regarding this variable is that although there are more men among the harassers, the victims are not exclusively female individuals (Reyns, 2010). This, however, does not imply that the effect of cyber-harassment on females and males is the same, since females experience cyber-harassment as more traumatic (Alexy et al., 2005; Borrajo et al., 2015; Estébanez & Vázquez, 2013; Torres, 2013).
Behavior is also different according to sex. In the cyber-violence of control, women more often check their boyfriends’ mobiles, while men more often spread messages and images without their partners’ consent, also sending more frightening or offensive messages and recording and taking more photos without their partners’ permission (Rodríguez & Megías, 2015). Respondents’ reactions to cyber-violence were diverse, although in general they reacted passively. For this reason, ANAR (2017) has highlighted the silence and passivity of cyber-victims, which is linked to low self-esteem, depression, apathy, fear, and mistrust of an education system that has proven ineffective in the struggle against violence and cyber-violence, factors that may explain such low-level reactions.
Regarding the factors associated with gender-based cyber-victimization among young people, our three initial hypotheses were confirmed (the incidence of technological, cognitive and behavioral factors), and the youth gender-based cyber-victimization profile was confirmed. The coincidences between the two are high. The results show that certain variables are sensitive when establishing factors and profiles of cyber-victimization: more varied and intensive use of virtual environments, more proactive responses to cyber-aggression, fewer self-protective digital competences, a more restricted concept of gender cyber-violence, and lower awareness of danger in the subject’s online behavior.
First, the very fact of indulging in more activity in cyberspace involves greater exposure and therefore a greater potential risk of being victimized. Young people are residents of the hyperspace (White & Le-Conu, 2011), where users’ day-to-day online behavior strongly influences the likelihood of becoming a victim, thus making the youth population vulnerable to cyber-victimization of any type (including the gender type). The second factor linked to cyber-victimization is the strength of reactions to cyber-violence. Our study shows that cyber-victims are at the same time cyber-aggressors, which agrees with other studies showing that cyber-victimization is linked to participation in cyber-harassment as an aggressor (Elipe et al., 2012; Estévez et al., 2010). A third factor found by this study was linked to cyber-victimization is having fewer self-protective digital competences. The most victimized adolescents in the sample were those who knew less about how to block the aggressor or how to change the privacy settings in their social networks, among other factors. Although there are numerous studies on digital literacy, we lack models that analyze to what extent digital skills are a key factor in experiencing cyber-harassment; yet there is no lack of calls to train young people in internet security as a way of preventing online violence (Flores, 2015; Moreno, 2012).
The concept one individual has of what comprises gender cyber-violence is also a factor that predicts and characterizes victims. In our study, victims had a much more restricted concept both in general and in each of the specific dimensions measured; that is, they saw fewer violent behaviors to be so. Similarly, there are a number of studies that have shown that psychological violence exercised by dominating men is only perceived as such by a minority of women, while tolerance to this type of violence is high among most women (Estébanez, 2010). Here, sexist stereotypes also have an explanatory role to play.
Another variable characterizing the victims of gender violence in our study is their lower awareness that some online behavior can be dangerous, such as posting personal information and repeatedly chatting with an unknown person. Similar data on young people’s potentially dangerous online behavior has been found in other studies (Fernández et al., 2015; Jiménez & Piqueras, 2012). The naturalness with which young people use the internet makes them see this medium as just one more social arena, giving little importance to the consequences of acts such as exchanging private information and images, which are seen as evidence of trust towards their friend or partner (Torres, 2013).
Conclusions
Overall, this study provides evidence that coincides with some previous research and, furthermore, has implications for youth education (in schools, the family, and society at large). Social networks are places where young people construct and project their identity and act as a mediating element of their everyday activities, forms of body language, behavior and peer relationships. The networks have become new “technologies of the self.” While we cannot change this situation, what we can do is to educate youth in the rational and critical use of social networks, in a true digital literacy. This education should favor the safe use of social networks and attempt to make young people aware that overexposure of personal information online can easily attract other users with negative intentions.
Digital literacy should also promote a critical gender perspective with the objective of countering the social media ideology of “the sexier the better,” which encourages reification of the body, derived from sexist patriarchal structures and attitudes. Moreover, it is also important to educate young people in gender equality in order to deconstruct stereotypes of female and male bodies and behaviors, thereby endeavoring to achieve mutual respect and more harmonious relationships. Along with education in school and upbringing in the family, this study should warn society and the social media that the transmission of values such as romantic love and other gender stereotypes helps perpetuate violence and the cyber-violence involved in tracking the partner. Adolescents’ faith in romantic myths may cause them to believe that certain abusive, controlling and jealous behaviors are signs of love and normal in a romantic relationship; these beliefs are particularly prevalent among girls (Cava & Buelga, 2020). Although boys and girls suffer the impact of cyber-victimization, the effects on young women are more damaging due to their greater overall social vulnerability.
Finally, it is also necessary to break the cycle of cyber-violence. Seeking help from the family or from professionals is preferable to doing nothing or taking revenge by turning the tables on the aggressor.
Study limitations
Although this study yielded interesting findings concerning the factors associated with gender cyber-victimization, it also has some limitations. We could highlight first the difficulty of comparing our results with other studies, given their scarcity and the differences between the instruments used. Another limitation is the specific age range of the sample. Moreover, the transversal nature of the study does not allow us to make definitive judgements regarding the causes of gender cyber-victimization, nor ensure that the specific time of the data collection was representative. Therefore, future studies should take into account other ages, address the phenomenon from a longitudinal approach, and include a qualitative and comprehensive perspective.