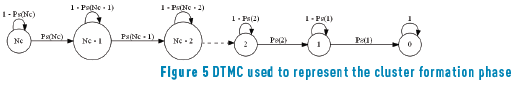Serviços Personalizados
Journal
Artigo
Indicadores
-
 Citado por SciELO
Citado por SciELO -
 Acessos
Acessos
Links relacionados
-
 Citado por Google
Citado por Google -
 Similares em
SciELO
Similares em
SciELO -
 Similares em Google
Similares em Google
Compartilhar
Revista Facultad de Ingeniería Universidad de Antioquia
versão impressa ISSN 0120-6230
Rev.fac.ing.univ. Antioquia no.79 Medellín abr./jun. 2016
https://doi.org/10.17533/udea.redin.n79a07
ARTÍCULO ORIGINAL
DOI: 10.17533/udea.redin.n79a07
Impact of the error sensing probability in wide coverage areas of clustered-based wireless sensor networks
Impacto de la probabilidad de sensado erróneo en redes de sensores inalámbricas basadas en clusters con amplias áreas de cobertura
Edgar Romo-Montiel1, Mario Eduardo Rivero-Ángeles1*, Iclia Villordo-Jimenez2, Herón Molina-Lozano3
1Laboratorio de Redes y Ciencias de Datos, Instituto Politécnico Nacional. Av. Juan de Dios Bátiz, Esq. Miguel Othón de Mendizábal, Col. Nueva Industrial Vallejo, Delegación Gustavo A. Madero.C. P. 07738. Ciudad de México, México.
2Unidad Profesional Interdisciplinaria en Ingeniería y Tecnologías Avanzadas, Instituto Politécnico Nacional. Av. Instituto Politécnico Nacional 2580, Col. Barrio la Laguna Ticomán, Gustavo A. Madero. C. P. 07340. Ciudad de México, México.
3Laboratorio de Microtecnología y Sistemas Embebidos, Instituto Politécnico Nacional. Av. Juan de Dios Bátiz, Esq. Miguel Othón de Mendizábal, Col. Nueva Industrial Vallejo, Delegación Gustavo A. Madero.C. P. 07738. Ciudad de México, México.
* Corresponding author: Mario Eduardo Rivero Ángeles, e-mail: mriveroa@ipn.mx
DOI: 10.17533/udea.redin.n79a07
(Received December 05, 2014; accepted January 29, 2016)
ABSTRACT
Wireless sensor networks are composed by a big number of autonomous nodes surveying a certain environmental parameter, such as temperature, humidity or even mobile targets. In this work, we focus on mobile target detection in wide area systems such as tracking animals in a forest or vehicle detection in security missions. Specifically, a low energy consumption clustering protocol is proposed, analyzed and studied. To this end, two communication schemes, based on the well-known LEACH protocol are proposed. The performance of the system is studied by means of a mathematical model that describes the behavior of the network under the most relevant parameters such as coverage radius, transmission radius, and number of nodes inside the network. Additionally, the transmission probability in the cluster formation phase is studied under realistic considerations of a wireless channel, where signal detection errors occur due to interference and noise in the access channel.
Keywords: Wide area wireless sensor network, clustering, adaptive transmission, Markov chain
RESUMEN
Las redes inalámbricas de sensores están compuestas por un gran número de nodos autónomos que vigilan algún parámetro del ambiente de interés, como puede ser la temperatura, la humedad o incluso objetivos móviles. Este trabajo se enfoca en la detección de móviles en áreas amplias como puede ser la vigilancia de animales en un bosque o la detección de vehículos en misiones de seguridad. Específicamente, se propone, analiza y estudia un protocolo de agrupación de bajo consumo de energía. Para ello, se presentan dos esquemas de comunicaciones basados en el bien conocido protocolo LEACH. El desempeño del sistema se estudia por medio de un modelo matemático que describe el comportamiento de la red bajo los parámetros más relevantes, como son: radio de cobertura, radio de transmisión y número de nodos en la red. Adicionalmente, se estudia la probabilidad de transmisión en la fase de formación de grupos bajo consideraciones realistas de un canal inalámbrico, en donde la detección de la señal tiene errores debido a la interferencia y ruido en el canal de acceso.
Palabras clave: Red inalámbrica de sensores de área amplia, agrupamiento, transmisión adaptativa, cadenas de Markov
1. Introduction
The increasing interest on the control, knowledge and monitoring our surroundings has produced the need to find and develop new technologies. To perform these tasks that range from human supervision to advanced technologies such as closed circuit video, process automation or the use of sensor networks.
Building on this, wireless sensors networks (WSNs) open the possibility of collecting different information about the environment and offer a constant monitoring adapted to a specific application. WSNs are composed by a high number of autonomous nodes located inside the area of interest [1] . Each node is responsible to collect the sensed information and to transmit it to a sink node or base station [2, 3]. Nodes in the network have to cooperate in order to efficiently gather the relevant information at the end point of the system. Typically, these nodes have a small size and their power supply comes from a small battery. Therefore, when a node drains its battery, it will no longer operate causing system degeneration in terms of information losses, reduced coverage area, and disconnection among nodes. As such, it is of paramount importance to have efficient energy consumption throughout the operation of the system. Clustering has been proposed in order to reduce such energy consumption, for example, the LEACH protocol [4, 5].
In the particular case where the surveyed area is wide, transmissions to the sink node are very costly due to the required energy to cover long-range communications. In this sense, the LEACH protocol is no longer efficient since it requires transmissions to cover the complete surveyed area.
Based on this observation, this work develops two clustering protocols based on the LEACH protocol. Both proposals increase the system's lifetime in wide coverage areas. Specifically, the LEACH MOD strategy is proposed to select the node's role inside each cluster while the Local LEACH is proposed in order to reduce the communication range among nodes in the network. In a previous work [6] , the issue of high coverage areas in WSNs was studied. However, results were obtained through numerical simulations only. Conversely, in this paper, we present a mathematical model to consider different system's conditions. Also, the mentioned previous work considered the particular case of a vehicular environment, whereas we now extend the work to consider a more general movement pattern of the surveyed target.
Furthermore, the issue of selecting an adequate value of the transmission probability at the cluster formation phase has been studied before [7] . However, to the best of our knowledge, the effect of the erroneous detection in a wireless environment has not been considered before.
In summary, the major improvement and significant advancement of this study in contrast to original LEACH are a) the selection of the cluster heads: The proposed LEACH MOD strategy consumes less energy in certain cases, since it requires less processing in the nodes; b) the extension of LEACH, called Local LEACH, to be used in big monitoring areas where long range transmissions are highly expensive in terms of energy consumption from the nodes; c) the use of an adaptive transmission scheme in the cluster formation phase is considered and mathematically modeled and; d) the study of the performance of the system when a noisy channel is considered. Indeed, the system's lifetime can be greatly reduced when channel errors are assumed. As such, this paper aims at providing more accurate guidelines for the practical implementation of WSNs by taking into consideration a non-ideal wireless channel. Indeed, the assumption of an ideal channel can overestimate the systems' lifetime.
The remaining of the paper is organized as follows: First, the conventional LEACH protocol is described. Then, the two modifications proposed to the LEACH protocol are presented, namely: LEACH MOD and Local LEACH. The latter is specifically designed to work in big open areas by reducing the transmission radius of nodes while the former is designed to reduce the complexity of the cluster head selection process. Following this, we noted that a fixed transmission probability is not suited for the cluster formation phase. Hence, an adaptive transmission probability is proposed. Then, the possible errors that can occur in the wireless channel are described. After this, the mathematical model used to obtain the main performance parameters is presented. The paper ends with some relevant numerical results and conclusions.
2. LEACH
LEACH is a protocol that organizes the nodes inside a network in clusters in order to distribute the energy load of each node. All nodes organize themselves to take part of a unique cluster as cluster head (CH) or as cluster member (CM). CHs have the function of gathering the sensed data of each CM that belongs to the cluster. When the CH has gathered all the cluster information, it then sends the data to the sink or base station [8] .
It is easy to see that CHs consume more energy since they have to be constantly receiving data from the CMs, and performing high-energy transmissions to the sink or base station. Hence, CHs drain their energy much faster than CMs. For that reason, LEACH rotates the function of CHs among all nodes in the network in order to balance the energy consumption equitably. This rotation occurs periodically. The LEACH protocol considers 20-second TDMA periods. After this period the clusters are broken and the cluster formation phase starts again selecting new CHs.
2.1. Clustering phase
This protocol (LEACH) is composed by two phases: The cluster formation phase and the steady state phase. In the former, nodes are selected either as CHs or CMs. As such, a random access protocol is used. As described in [8] , the slotted NP-CSMA scheme entails the best performance compared to other random access protocols. As such, nodes transmit in each time slot with probability t. In the latter, clusters are already formed and nodes can transmit their information to their respective CHs. In this phase, a TDMA based scheme is preferred since the CH already knows the number of nodes that will report data in each cluster [9] . Hence, transmissions can be done in an orderly fashion.
In the cluster formation phase, nodes choose to become cluster heads according to the Eq. (1) [10]:
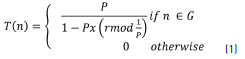
Where P is the percentage of cluster heads into the network, r is the number of current cluster heads and G is the group of nodes that had not been cluster head in a previous time. In this way, the protocol allows an adequate distribution of energy consumption in each node.
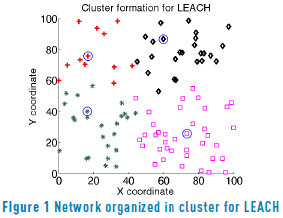
Figure 1 shows how the network is organized in clusters, where nodes with a circle are the cluster heads. The main disadvantage of this protocol is that the selection of the transmission probability is energy consuming and nodes have to keep track of different parameters such as rand G. Additionally to the energy consumption, there is an inherent delay in the processing of T(n). In view of this, two modifications to the LEACH protocol, called LEACH MOD and Local LEACH, are proposed and described in the next section.
LEACH MOD
The LEACH MOD protocol works as follows:
· In the cluster formation phase, the remaining nodes attempting to transmit their control packet in each time slot do it according to a geometric process with probability t.
· Nodes are chosen to be cluster heads or cluster members only based on the transmission order of arrival of nodes, i.e., if the number of clusters in the network is set to be Nch, then the first Nch nodes that successfully transmit their control packets are designated as CHs, while the rest N-Nch become cluster members. In any given time slot, if there are two or more transmissions, a collision occurs and none of the transmitted packets will be received successfully, hence they have to be retransmitted. On the other hand, if only one packet is transmitted in a time slot, it is considered as a successful transmission and all the nodes in the network recognize and decode such transmission.
The effect of the number of CHs on the performance of the system is investigated in a subsequent section. Note the LEACH MOD strategy does not require the calculation of the transmission probability since this value can be established at the beginning of the system's operation.
It is important to mention that the LEACH protocol ensures that no node can become CH in successive rounds. This cannot be guaranteed by our proposed protocol. However, since nodes transmit according to a geometric process with parameter t, the probability that a node will be elected as a CH in consecutive rounds is very low. Also, note that neither LEACH nor LEACH MOD protocols ensure a uniform distribution of clusters in the system area. In order to better distribute the CHs in the system, the Local LEACH protocol is proposed and it is described in the following.
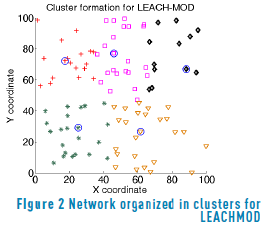
Figure 2 shows how the network is organized in clusters, where the nodes with circle are the cluster heads.
Local LEACH
In the LEACH MOD, additional to the fact that CHs are not evenly distributed in the surveyed area, it entails high-energy consumption due to the fact that all nodes transmit with enough power to cover the total area of the network. In big surveyed areas, this is a major issue that quickly drains the battery of each node, independently if it is a CH or a CM.
Building on this, a scheme that limits the transmission radius of each node to reduce the coverage area and at the same time reduce the energy consumption through the use of short transmissions is proposed, namely Local LEACH and works as follows:
· Nodes transmit in a reduced area where only the nodes in the immediate neighborhood receive the control packets to form the clusters.
· The cluster formation process is like LEACH MOD, where the nodes are chosen to be cluster heads or cluster members only based on the order of arrival of node's transmissions.
The NP-CSMA scheme is used. However, the slotted channel now is divided in two different time slots as is shown in Figure 3.
· The Tx time slot is used by each node in order to become a cluster head.
· The ACK time slot is used by the nodes that have received a previous transmission from a specific cluster head to transmit a confirmation packet in order to be aggregated to that specific cluster.
We now describe the Local LEACH operation in detail. Each node transmits a packet in each Tx time slot with a limited radius according to a geometric process with probability t. By each successful transmission, the node that transmitted will be defined as CH and the nodes that receive a single packet will be conjoint to the CH associated to the received packet. If a node receives two or more transmissions, then a collision is assumed to occur and it disregards the collided packets. It is also assumed that the nodes that receive a single transmission can successfully decode it and respond to the corresponding CH in the following ACK time slots. As such, the nodes that receive a single packet form a CH desist to become CHs and they become CMs by default. Note that in Local LEACH, nodes do not know the exact number of nodes that detect their transmissions. In fact, according to the transmission range, nodes can have no neighbors at all, or they can have many nodes in the vicinity. Unlike LEACH, where all nodes receive every transmission, in the Local LEACH a response from the nodes that actually receive a successful transmission is required. Also, nodes that receive multiple transmissions (i.e., a packet collision) cannot transmit an ACK packet.
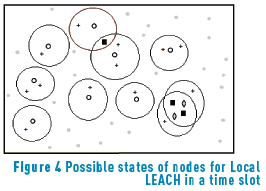
Figure 4 shows the behavior of the Local LEACH scheme in a given time slot.
Nodes represented by a circle have had a successful transmission, i.e., at least a neighbor node inside its transmission range successfully received the packet. The nodes represented by plus signs have received a successful transmission from a certain CH and are associated to it. Hence, they need to transmit an ACK packet in the following ACK time slots. The gray nodes have not transmitted any packet yet and have not received a transmission from any other node. Hence, they are available to become cluster heads or cluster members in a future time slot. The squared black nodes are nodes that receive multiple packets in a time slot. Hence, a collision occurred. As such, they are not associated to any cluster head and can become cluster heads or cluster members in a future time slot. Finally, the nodes represented by a gray rhombus are nodes that transmitted a control packet that collided with other packets in a given neighbor node. Hence, they can also become cluster heads or cluster members in a future time slot. It is important to note that more than one node can transmit without generating a collision. In this scheme, it is possible to have a high number of nodes inside the cluster or even cluster composed of a unique node. In this last case, that node is a CH with no associated CMs.
On a more detailed study on the effect of the transmission probability and the total number of nodes inside the network, note that when the number of nodes with a pending transmission is relatively high, the use of a high value of t causes a high amount of collisions inside the cluster formation process, entailing a quick energy drain from all nodes in the system. On the other hand, the use of a low transmission probability in the same scenario entails a lower number of collisions but could generate empty time slots. However, as nodes successfully transmit their control packets, the number of pending transmissions decreases accordingly. Hence, the low value of t is no longer adequate when only a few nodes remain to transmit their packets since a high idle transmission period occurs. Building on this observation, it is clear that the value of the transmission probability has to vary according to the number of remaining nodes in the cluster formation procedure. As such, the adaptive transmission strategy is proposed and it is studied next.
2.2. Adaptive transmission probability
In the adaptive transmission probability strategy, the value of t varies according to the number of nodes with a pending transmission. Hence, the transmission probability of each node depends on the inverse of the number of neighbor nodes. In this way, with a high number of contending nodes, the transmission probability is low, and vice versa. Then, each node computes the value of t in every time slot as Eq. (2) indicates:

Where i is the number of remaining nodes in the cluster formation phase. As it can be seen, in order to calculate the value of t, it is required that each node estimates the number of nodes with a pending transmission or the number of nodes that have successfully transmitted their control packets. Also, in the case of the LEACH MOD, the sink node, which does not have energy restriction issues, can perform this estimation and broadcast it to the rest of the nodes in the system. Note that this is not possible in the Local LEACH strategy where nodes have to compute the value of t.
This estimation can be done by detecting each successful transmission and assuming that the number of nodes in the system has not changed, i.e., that all initial nodes are still correctly functioning. However, the successful transmission detection is not error-free in a wireless environment due mainly to fading, interference and noise. In the following, the effect of a noisy channel is investigated.
Errors in a noisy channel
In order to consider the effect of a wireless channel, two estimation errors are considered: false positive and false negative estimation. The later corresponds to the case when the sink node does not detect a successful transmission that actually happened, while the former corresponds to the case when the sink node detects a successful transmission but in reality no such transmission occurred. As such, the estimation of t can have a higher (in case of false negative estimation) or lower value (in case of false positive estimation) than the real value i. In this work, we first assume that either false positive and false negative estimation errors are equally probable to happen and this consideration is relaxed latter in the paper.
a) Uniform estimation error: For the first case, a uniformly distributed error in the range of (-e,e) is considered. Specifically, when there are i nodes remaining to transmit their control packet, this uniform assumption implies that the sink or base station can wrongly consider that there are i+1, i+2, i+3, …,i+e, i-1, i-2, i-3, …, or i-e remaining nodes with probability 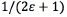 for each possibility. Also, it is assumed that the correct value of remaining nodes is estimated with the same probability
for each possibility. Also, it is assumed that the correct value of remaining nodes is estimated with the same probability 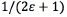 . Note that this assumption may not be accurate, since the error can have different distribution or false negative and positive estimation may not be equally probable. Indeed, this is a strong assumption. The rationale behind this is that in a wireless channel, we assumed that the effects of fading due to obstacles and long-range transmissions have a comparable impact on the system as noise and interference. Note that long-range transmissions and fading causes many false negative errors in the estimation of nodes. On the other hand, noise and interference may cause many false positive errors in the estimation of nodes. However, this may not be the case.
. Note that this assumption may not be accurate, since the error can have different distribution or false negative and positive estimation may not be equally probable. Indeed, this is a strong assumption. The rationale behind this is that in a wireless channel, we assumed that the effects of fading due to obstacles and long-range transmissions have a comparable impact on the system as noise and interference. Note that long-range transmissions and fading causes many false negative errors in the estimation of nodes. On the other hand, noise and interference may cause many false positive errors in the estimation of nodes. However, this may not be the case.
Building on this, it is considered that the transmission probability in the cluster formation phase is now calculated as Eq. (3) :

As it occurs in (3), the transmission probability varies in each time slot according to the estimated outcome of the previous time slot. As a particular case, when the estimation error is such that 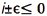 , the sink node broadcast the value of tA = 0.9 or each node adjust their value of tA = 0.9 in order to avoid any operation malfunctions.
, the sink node broadcast the value of tA = 0.9 or each node adjust their value of tA = 0.9 in order to avoid any operation malfunctions.
b) Non-uniform estimation error: In this scenario, we have considered the case where the estimation error is no longer uniformly distributed in the range 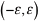 . As such, we extend the previous scenario to consider two possibilities: a) the case where a false positive is more likely to happen and b) the case where a false negative is more likely to happen. For the former case, the false positive case, it is considered that the sink node or base station wrongly estimates that the number of remaining nodes is i+1, i+2, i+3, …,i+e, with probability 3/4ε each case, while it wrongly assumes that there are i-1, i-2, i-3, …,i-e, or even i, with probability 1/4(ε + 1)each possibility. For the latter case, the false negative case, it is considered that the sink node or base station wrongly estimates that the number of remaining nodes is i+1, i+2, i+3, …,i+e, or even i, with probability 1/4(ε + 1) each case, while it wrongly assumes that there are i-1, i-2, i-3, …,i-e, with probability 3/4ε each possibility.
. As such, we extend the previous scenario to consider two possibilities: a) the case where a false positive is more likely to happen and b) the case where a false negative is more likely to happen. For the former case, the false positive case, it is considered that the sink node or base station wrongly estimates that the number of remaining nodes is i+1, i+2, i+3, …,i+e, with probability 3/4ε each case, while it wrongly assumes that there are i-1, i-2, i-3, …,i-e, or even i, with probability 1/4(ε + 1)each possibility. For the latter case, the false negative case, it is considered that the sink node or base station wrongly estimates that the number of remaining nodes is i+1, i+2, i+3, …,i+e, or even i, with probability 1/4(ε + 1) each case, while it wrongly assumes that there are i-1, i-2, i-3, …,i-e, with probability 3/4ε each possibility.
Note that these scenarios are meant to capture the different effects of a wireless channel. For instance, when the transmission range is high and/or there are many objects or obstacles in the transmission trajectory, there is a higher probability that the transmissions are not correctly decoded at the receptor mainly because of propagation losses and fading effects. As such, this scenario corresponds to the case where many false negative errors occur. On the other hand, when there is a lot of noise or interference in the system, the receptor may wrongly assume that a transmission occurs when in fact no node transmitted. As such, the false positive is more likely to happen.
3. Mathematical Model
In order to study the system behavior, a mathematical model that captures the main performance parameters in the cluster formation phase was proposed. This model reflects the fact that each node has to transmit a control packet to form the clusters, in order to enter the steady state phase where the gathered data is transmitted. The cluster formation phase finishes when all nodes have transmitted their respective control packets. In this way, each state of the model represents the pending nodes to transmit. To this end, a transitory Discrete Time Markov Chain (DTMC) is proposed as it is shown in Figure 5 .
It can be seen that the DTMC remains in the same state, either because a collision occurred or no transmission occurred in a given time slot. Hence, the state decreases only if a single transmission by either of the pending nodes is performed. The latter case occurs with probability Ps(i) when there are i nodes remaining to successfully transmit their control packets, while the probability to remain in the same state occurs with the complementary probability. Specifically as (4) :
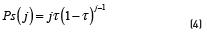
Building on this, the average time (in time slots) that the system remains in state j is given by Eq. (5) :
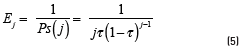
And the average time to form a cluster is given by Eq. (6) :
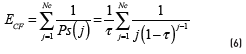
Note that the model considers an initial state Nc which is the total number of nodes in the cluster formation phase. In the case of LEACH MOD, it is the total number of nodes in the network. However, in the case of Local LEACH, Nc depends on: a) density of nodes in the system, b) coverage area and c) transmission radius. From this, it is possible to see that Nc can be calculated as Eq. (7) indicates:
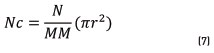
Where N is the number of nodes inside the network, M is a side of the coverage area and r is the transmission radius of each node. Finally, the complete equation of the total number of nodes in the cluster is given by (8) :
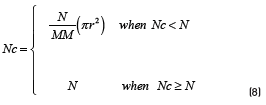
4. Numerical results
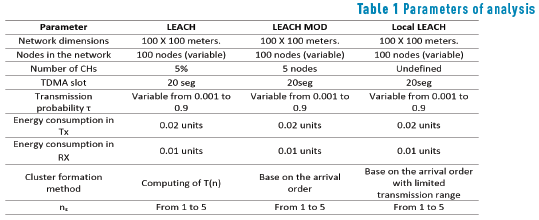
In the following, the main system parameters and assumptions are presented. A square coverage area of 100 squared meters with a variable number of nodes is considered in order to analyze the performance of the cluster formation process under different scenarios. Some of these parameters were taken from the literature [11, 12].
For the energy consumption model, normalized energy units are used in order to have a general energy consumption model that can be easily scaled to any commercial equipment. Specifically, it was assumed that: The energy required to transmit a packet in the cluster formation phase (CF) is 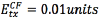 ; The energy required to receive a packet in the cluster formation phase is
; The energy required to receive a packet in the cluster formation phase is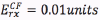 ; The energy required to transmit a packet from a cluster member to a cluster head in the steady state is
; The energy required to transmit a packet from a cluster member to a cluster head in the steady state is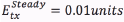 ; The energy consumed by the cluster head in order to receive a packet from a cluster member in the steady state is
; The energy consumed by the cluster head in order to receive a packet from a cluster member in the steady state is 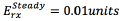 ; The energy consumed by the cluster head to transmit a packet to the sink node (CH→Sink) is
; The energy consumed by the cluster head to transmit a packet to the sink node (CH→Sink) is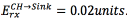 Note that the energy required to transmit a packet is always higher than the energy required to receive such packet. Also, the packet transmission from the cluster head to the sink node is the most energy consuming.
Note that the energy required to transmit a packet is always higher than the energy required to receive such packet. Also, the packet transmission from the cluster head to the sink node is the most energy consuming.
Finally, it was considered a percentage of nodes that act as cluster heads as follows: for LEACH, five percent of nodes in average act as cluster heads while in LEACH MOD, NCH nodes always become cluster heads. In Local LEACH the transmission radius to each node is variable as well as the number of nodes in order to analyze the network behavior. In the three cases, the value of t changes from a minimum value of 0.001 to a maximum value of 0.9 in order to study the system in different environments. Table 1 shows the main parameters used for the numerical results presented in this section.
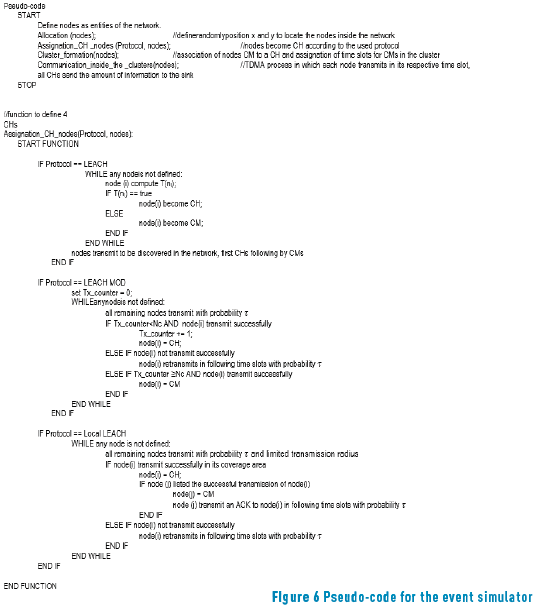
The following results were obtained using a discreet event simulation developed on C++ language as in [13-17], in which the previous mentioned parameters were considered along with a series of assumptions. In the following pseudo code ( Figure 6 ), we illustrate the basic discrete event simulator and the main assumptions:
4.1. Performance comparison results
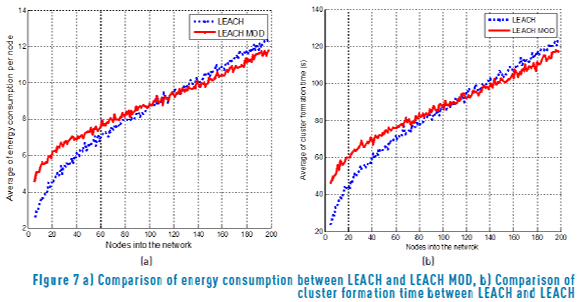
In Figure 7 (a), the proposed LEACH MOD scheme is compared to LEACH. As it can be seen, LEACH has better performance when the system is formed by a low value of nodes. However, LEACH MOD obtains better results when the number of nodes increases. In the case of LEACH, there are five percent of nodes as CHs and LEACH MOD is using five nodes as CHs. Also, both schemes have adopted a static transmission probability with a value of 0.2. Note that the critical point (where both schemes have a similar performance) is when the number of nodes is one hundred. This is because the number of CHs is the same for both schemes. A similar behavior is shown in the cluster formation time, as shown in Figure 7 (b), where the critical point is at the same value of one hundred of nodes.
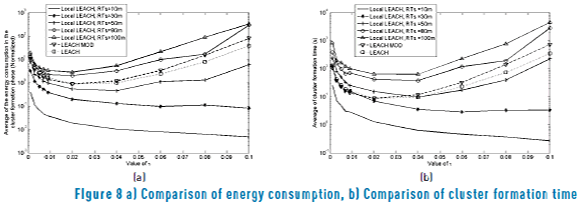
Now the effect of the transmission probability of nodes in the performance of the system is investigated. In the following results, the value of t was varied while a static value of nodes inside the network (one hundred) is considered. In these results, the value of t remains fixed and constant throughout the system operation. First the impact of t is studied for the LEACH protocol. Figure 8 (a) and Figure 8 (b) show that high and low values of t entail high levels of energy consumption and cluster formation time. In the latter case due to idle listening, while the former due to high number of packet collisions. However, it can be seen that an adequate value for t = 0.03 gives the lowest level of energy consumption and cluster formation time. Now, the behavior of the network for the LEACH MOD scheme for different values of tis investigated. At first view, it is observed that there is a similar tendency in the results as LEACH, obtaining a high level of energy consumption and cluster formation time for high values of t. However, in this scheme the performance of energy consumption and the cluster formation time is lower for a value of t = 0.02 showing the appropriate value of t. Now, the Local LEACH scheme is studied. In this scheme, additionally to variations of the value of t, the value of the transmission radius is also varied in order to analyze the behavior of the network in different scenarios (note that this parameter has no impact neither on LEACH nor on LEACH MOD).It can be seen that a low level of energy consumption and cluster formation time is obtained when the transmission radius is lower than 50 meters, and the value oft is lower than 0.06. It is important to note that unlike the LEACH and LEACH MOD schemes, the Local LEACH mechanism gives the possibility to have a low transmission radius and adopt high transmission probability values without degrading the performance of the system. This is because a low transmission radius entails a small number of nodes in the vicinity. This in turns generates a low collision probability even for high values of the transmission probability. Comparing the performance of the three studied schemes, it can be seen that the energy consumption and the cluster formation time have a similar behavior in the three schemes. Moreover, each scheme has a better performance than the rest in specific conditions of the network. Specifically, it can be seen that LEACH is better than the other schemes when the network adopts a transmission probability higher than 0.03, but when the transmission probability decrees, LEACH MOD shows a lower energy consumption. However it shows that Local LEACH has lower energy consumption for all the values of t when the transmission radius is lower than 50 meters. A similar result was obtained in the cluster formation time, where Local LEACH forms the clusters faster than LEACH and LEACH MOD when the transmission radius is lower than 50 meters, but for radius higher than 60 meters and t higher than 0.08, the Local LEACH has much higher cluster formation delay than LEACH and LEACH MOD which are organized in less time slots.
The previous results were obtained considering a fixed value of the transmission probability, i.e., all nodes use the same value throughout the system operation.
4.2. Error channel results
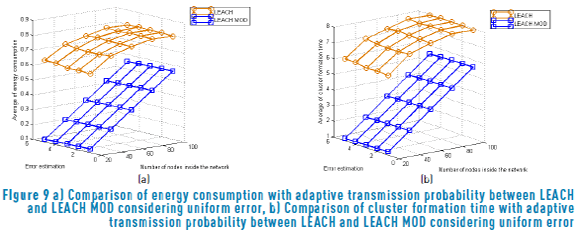
Now, the adaptive transmission probability scheme is studied considering a no free-error channel. Figure 9 (a) shows the average energy consumption in the system for different number of nodes in the network and different error estimation range ε. It can be seen that the use of the LEACH MOD scheme with an adaptive transmission probability achieves lower energy consumption than the LEACH protocol. This is because in the LEACH MOD scheme the number of collisions and idle listening periods are reduced compared to the LEACH protocol. Similarly, the average cluster formation time is lower in the LEACH MOD scheme compared with the LEACH protocol, as is shown in Figure 9 (b). As was expected, the energy consumption and cluster formation time increase as the number of nodes increases. Also, it can be seen that the effect of the error estimation is not high. This could be because a uniform distribution on the error estimation was considered. Hence, different estimation error scenarios are now considered.
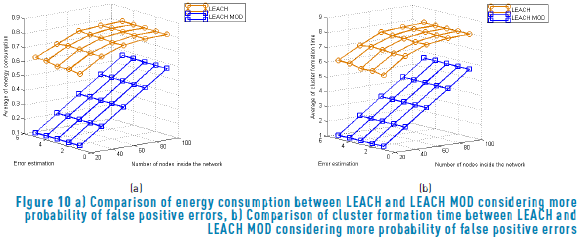
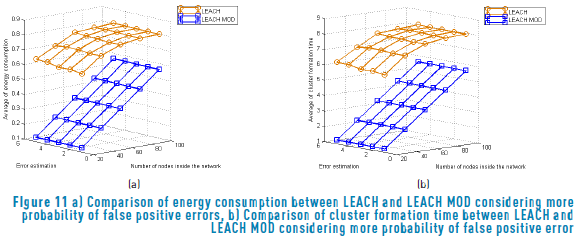
Now, the case where false positive and false negative errors do not have the same probability to occur, namely, distinct to a uniform distribution is now investigated. Through that assumption the results obtained are presented in Figure 10 and Figure 11 where the former represents the network behavior when errors of false positive have three times more probability to occur than false negative, while the last assume that false negatives occur three times more than false positives.
Comparing the three scenarios, it can be seen that the impact of error is not dependent on the distribution of the false negative probabilities and false positive probabilities. Note that there exists a wide diversity of possible distribution that can have a different behavior. However, this is a research topic for futures works.
4.3. Comparison of mathematical and simulation results
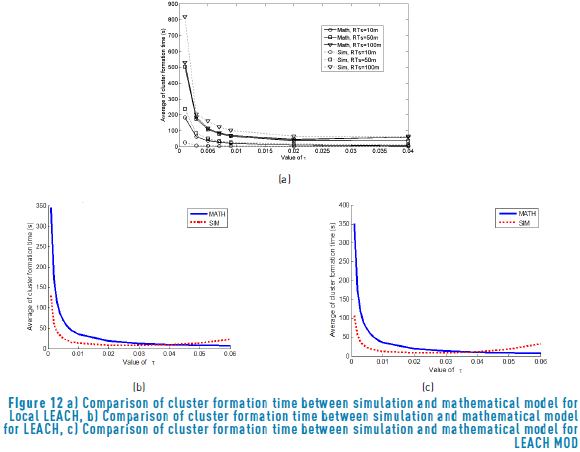
In order to validate the mathematical analysis, simulation results are compared to analytical values. Figure 11 (a) shows the comparison for Local LEACH in terms of the average cluster formation time. It can be seen that, in general, a good fit between simulation and analytical results is obtained. Note that the better fit occurs in values of t higher than 0.01 for all transmission radiuses. For the cases of LEACH and LEACH MOD, the comparison between the simulation and the mathematical model shows that a better fit is obtained for values of t between 0.01 and 0.06. These results are shown in the Figure 12 (b) and Figure 12 (c).
5. Conclusions
In this work, three schemes for the formation of clusters in a wireless sensor networks are studied under a fixed and adaptive transmission probabilities in different environments. Through the results, it can be observed that LEACH, LEACH MOD and Local LEACH, have their respective advantage against each other depending on the values and characteristics of the network. Specifically, when there are a high number of nodes in the network, it is convenient to adopt a limited transmission radius in order to use small areas inside the network to work with the clustering process and avoid collisions. In these cases, Local LEACH is the adequate protocol to implement because it limits the transmission radius of each node. It entails a lower energy consumption and cluster formation time when the transmission radius has a reduced value. Indeed, when transmission radiuses are lower than 50 meters and values of t higher than 0.01, the Local Leach outperforms the other schemes. On other hand, LEACH performs better for high transmission radiuses and transmission probabilities higher than 0.03. However, LEACH MOD shows better results when the transmission probability is lower than 0.03 considering that the transmission radius covers the total coverage area. Also, a mathematical model is presented to study the performance of these schemes. The analytical results show a good fit compared to simulation results. Finally, the benefits of introducing an adaptive transmission probability scheme as opposed to the fixed strategy is studied and analyzed. It can be seen that both the energy consumption and cluster formation delay are reduced considering such adaptive strategy. To this end, an estimation error is considered due to the effects of the wireless channel. Different values of this error are considered showing a small impact on the overall system performance. Additionally, such errors have minimum affection on our proposal of LEACH MOD comparing with LEACH, which presented higher energy consumption and cluster formation time, independently of the distribution of probability to occur those errors.
6. References
1. H. Lee, ''Towards a general wireless sensor network platform for outdoor environment monitoring'', in IEEE Sensors Conference, Taipei, China, 2012, pp. 1-5. [ Links ]
2. National Instruments Corporation, ¿Qué es una Red de Sensores Inalámbricos?, 2009. [Online]. Available: http://www.ni.com/white-paper/7142/es/. Accessed on: Dec. 15, 2013. [ Links ]
3. J. Querol, Estudio y evaluación de prestaciones de redes inalámbricas de sensores, 2011. [Online]. Available: https://riunet.upv.es/bitstream/handle/10251/10354/Proyecto_Querol.pdf. Accessed on: Nov. 07, 2013. [ Links ]
4. P. Mohapatra and K. Kredo, ''Medium access control in wireless sensor networks'', Computer Networks, vol. 51, no. 4, pp. 961-994, 2007. [ Links ]
5. M. Handy, M. Haase and D. Timmermann, ''Low energy adaptive clustering hierarchy with deterministic cluster-head selection'', in 4th International Workshop onMobile and Wireless Communications Network, Stockholm, Sweden, 2002, pp. 368-372. [ Links ]
6. M. Ramírez, M. Rivero and I. Villordo, ''Monitoreo de tráfico vehicular en sistemas V2I mediante el uso de una red inalámbrica de sensores'',Rev. Fac. Ing. Univ. Ant., no. 71, pp. 115-125, 2014. [ Links ]
7. M. Rivero and I. Orea, ''Tools for the selection of the transmission probability in the cluster formation phase for Event-Driven Wireless Sensor Networks'', Rev. Fac. Ing. Univ. Ant., no. 73, pp. 101-110, 2014. [ Links ]
8. D. Johnson and D. Maltz, ''Truly seamless wireless and mobile host networking. Protocols for adaptive wireless and mobile networking'', IEEE Personal Communications, vol. 3, no. 1, pp. 34-42,1996. [ Links ]
9. R. Rom and M. Sidi, Multiple access protocols. Performance and analysis. New York, USA: Springer-Verlag, 1990. [ Links ]
10. W. Heinzelman, A. Chandrakasan and H. Balakrishnan, ''Energy-efficient communication protocol for wireless microsensor networks'', in 33rd Annual Hawaii International Conference on System Sciences, Maui, USA, 2000. [ Links ]
11. S. Chaurasiya, J. Sen, S. Chaterjee and S. Bit, ''An energy-balanced lifetime enhancing clustering for WSN (EBLEC)'', in 14th International Conference on Advanced Communication Technology (ICACT),PyeongChang, South Korea, 2012, pp. 189-194. [ Links ]
12. A. Mehmood, S. Khan, B. Shams and J. Lloret, ''Energy-efficient multi-level and distance-aware clustering mechanism for WSNs'', International Journal of Communication Systems, vol. 28, no. 5, pp. 972-989, 2015. [ Links ]
13. A. Varga, ''The OMNeT++ discrete event simulation system'', in European Simulation Multiconference (ESM), 2001, pp. 65-71 [ Links ]
14. I. Leyva, ''Diseño y análisis de desempeño de un protocolo de acceso aleatorio para redes inalámbricas de sensores por eventos'', Undergraduate thesis (unpublished), Instituto Politécnico Nacional, México City, México, 2011. [ Links ]
15. M. Ramírez, ''Análisis del desempeño de una red Ad-Hoc vehicular para sistemas de información móvil'', Undergraduate thesis (unpublished), Instituto Politécnico Nacional, México City, México, 2012. [ Links ]
16. M. Rivero, G. Rubino, I. Torres and L. Martinez, ''Window-based streaming Video-on-Demand transmission on BitTorrent-like Peer-to-Peer networks'', in IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, USA, 2013, pp. 1-6. [ Links ]
17. M. Ismail, M.Shanudin and R. Saqour, ''Discrete-event simulation modeling tool for routing process in GPSR ad hoc network routing protocol'', in IEEE International Conference on Telecommunications and Malaysia International Conference on Communications (ICT-MICC), Penang, Malaysia, 2007, pp. 86-90. [ Links ]