Services on Demand
Journal
Article
Indicators
-
 Cited by SciELO
Cited by SciELO -
 Access statistics
Access statistics
Related links
-
 Cited by Google
Cited by Google -
 Similars in
SciELO
Similars in
SciELO -
 Similars in Google
Similars in Google
Share
Revista Facultad de Ingeniería Universidad de Antioquia
Print version ISSN 0120-6230
Rev.fac.ing.univ. Antioquia no.79 Medellín Apr./June 2016
https://doi.org/10.17533/udea.redin.n79a10
ARTÍCULO ORIGINAL
DOI: 10.17533/udea.redin.n79a10
Cross-layer designs for energy efficient wireless body area networks: a review
Diseños de capa cruzada para redes inalámbricas de área corporal energéticamente eficientes: una revisión
Juan Camilo Correa-Chica*, Juan Felipe Botero-Vega, Natalia Gaviria-Gómez
Departamento de Ingeniería Electrónica e Ingeniería de Telecomunicaciones, Facultad de Ingeniería, Universidad de Antioquia. Calle 67 # 53- 108. A. A. 1226. Medellín, Colombia.
* Corresponding author: Juan Camilo Correa Chica, e-mail: camilo.correa@udea.edu.co
DOI: 10.17533/udea.redin.n79a10
(Received July 31, 2015; accepted April 27, 2016)
ABSTRACT
Cross-layer design is considered a powerful alternative to solve the complexities of wireless communication in wireless body area networks (WBAN), where the classical communication model has been shown to be inaccurate. Regarding the energy consumption problem, we have prepared a current survey of the most relevant scientific publications on energy-efficient cross-layer design for WBAN. In this paper, we provide a comprehensive review of the advances in cross-layer approaches, protocols and optimizations aimed at increasing the network lifetime by saving energy in WBANs. Subsequently, we discuss the relevant aspects and shortcomings of these energy-efficient cross-layer techniques and point out the open research issues and challenges in WBAN cross-layer design. In this survey, we propose a taxonomy for cross-layer approaches to fit them into categories based on the protocols involved in the cross-layer scheme. A novel classification is included to clarify the theoretical concepts behind each cross-layer scheme; and to group similar approaches by establishing their differences from the other strategies reviewed. Our conclusion considers the aspects of mobility and channel modeling in WBAN scenarios as the directions of future cross-layer research for WBAN and telemedicine applications.
Keywords: Cross-Layer, energy efficiency, network lifetime, network protocols, wireless body area networks
RESUMEN
El diseño de capa cruzada se considera una poderosa alternativa para dar solución a las complejidades introducidas por las comunicaciones inalámbricas en redes de área corporal (WBAN), donde el modelo clásico de comunicaciones no ha exhibido un desempeño adecuado. Respecto al problema puntual de consumo de energía, hemos preparado la presente revisión de las publicaciones más relevantes que tratan la eficiencia energética para WBAN usando diseño de capa cruzada. En este artículo se proporciona una revisión exhaustiva de los avances en aproximaciones, protocolos y optimizaciones de capa cruzada cuyo objetivo es incrementar el tiempo de vida de las redes WBAN mediante el ahorro de energía. Luego, se discute los aspectos relevantes y deficiencias de las técnicas de capa cruzada energéticamente eficientes. Además, se introducen aspectos de investigación abiertos y retos en el diseño de capa cruzada para WBAN. En esta revisión proponemos una taxonomía de las aproximaciones de capa cruzada, de modo que las técnicas revisadas se ajustan en categorías de acuerdo a los protocolos involucrados en el diseño. Una clasificación novedosa se incluye para hacer claridad en los conceptos teóricos involucrados en cada esquema de capa cruzada y para luego agrupar aproximaciones similares evidenciando las diferencias con otras técnicas entre sí. Nuestras conclusiones consideran los aspectos de movilidad y modelamiento del canal en escenarios de WBAN como las direcciones para futura investigación en WBAN y en aplicaciones de telemedicina.
Palabras clave: Capa cruzada, eficiencia energética, tiempo de vida de la red, protocolos de red, redes inalámbricas de área corporal
1.Introduction
Recent advances in wireless sensor networks (WSN) and ubiquitous computing have revealed the wide field of application of these techniques in medical environments, particularly related to remote medical surveillance and disease treatment. The deployment of wireless sensors, in this context, lies in the human body, fostering the emergence of a new notion in this field: the WBAN that brings a myriad of possibilities for human health remote monitoring for the enhancement of a patient's quality of life. Although WBANs are in fact WSNs and share the same energy, processing and deployment constraints, they have special limitations due to their implantation on or inside the body. The main limitations are energy consumption and body channel effects. WBANs are supposed to last for long periods of time and, in the case of implanted sensors, periodic battery replacement is not possible. Regarding this issue, previous research has shown that the traditional open system interconnection (OSI) layered stack does not fit all of the energy consumption and QoS demands in WBANs, bringing about the emergence of new non-layered approaches and techniques like cross-layer design.
There are several challenges related to WBAN development, namely 1)the use of low power levels to avoid tissue heating and reduce levels of electromagnetic absorption, 2)the need for high levels of quality of service (QoS) for the management of critical information, such as the health condition of a patient, 3)the size of sensor node devices to avoid discomfort in the users, 4)the heterogeneity of the sensor nodes, 5)the mobility of the sensor nodes in the WBAN introduced by postural changes and 6)the scarce energy resources that depend on the battery life.
Energy consumption efficiency in WBANs is an open research issue that has been approached from different angles. Power-efficient protocols have been developed for individual layers of the OSI model, and novel protocol implementations have been published that aim to introduce new design paradigms. Particularly, at the MAC layer, there are plenty of proposals to reduce energy consumption in WBANs like MedMAC [1], BodyMAC [2], BSN-MAC [3], DQ- MAC [4], H-MAC [5], CA-MAC [6] and TaMAC [7]. All these protocols try to reduce energy consumption in basic medium access schemes like CSMA/CA (Carrier Sense Multiple Access Collision Avoidance) and TDMA (Time Division Multiple Access) due to factors such as collisions, overhearing, overhead, idle listening and lack of synchronization (cause of clock drifting). With regard to the network layer, energy aware routing and data load balancing are the main goals to extend the network lifetime. Some protocols devised for WBANs include TARA [8], ALTR [9], LTRT [10] and LR [11]. Most of these protocols were designed to avoid rise of temperature in the sensor nodes by relaying traffic routing to specific nodes and fusing data to reduce the number of packet transmissions. Regarding the transport layer, protocols have been designed to avoid energy waste resulting from congestions and bottlenecks that could impact the packet loss ratio (PLR) and the latency of communication [12]. In the application layer, the energy aware protocols focus on the compression of data, data fusion and data aggregation techniques to reduce the number of transmissions [13, 14].
Some of the protocols mentioned above present cross-layer schemes and save energy but are only focused on the energy consumption of the medium access mechanism. The others work under the stack layered model with independent layers that only communicate directly with upper and lower layers. Hence, the layers that are not optimized still waste resources and hence these approaches are inadequate for WBANs. To ameliorate this situation, the cross-layer design suggests a new model of information sharing between adjacent and non-adjacent layers, and research has shown that this type of approach enhances the performance of the WSNs and WBANs in scenarios where the traditional OSI model fails [15].
Many on-going studies focus on cross-layer designs for WBANs, all of them aimed at addressing the particular complexities introduced by WBANs. In this survey, our goal is to analyze some studies that propose to solve the problem of energy-efficiency in WBANs. To achieve this goal, we introduce a taxonomy that classifies the reviewed investigations by the communication layers involved in the cross-layer design presented in each of them. The remainder of the paper is organized as follows: in Section 2, we illustrate the main concepts of WBANs, cross-layer design and energy efficiency. In Section 3, we present the taxonomy for cross-layer approaches solving the problem of energy efficiency in WBANs. In Section 4, we classify the protocols reviewed by the cross-layer scheme used to develop the approach. In Section 5, we discuss the results of these approaches and note open challenges in this area and finally, in Section 6, we conclude this paper.
2. Energy constraints in WBAN and Cross-layer design
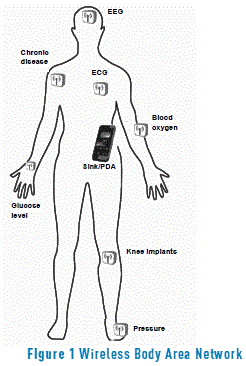
The notion of WBAN was introduced by T. G. Zimmerman in 1996. A WBAN can be thought of as a set of wirelessly connected sensor nodes that monitor vital signs and the process human body signals [16]. These nodes are designed in such a way that they can be deployed on the body, worn, or implanted inside the body. The WBAN basic architecture consists of nodes spread along or inside the body and a central node known as a ''sink'' that plays the role of an interface between the WBAN and external networks (Figure 1). WBANs have emerged as an interesting field for researchers focused on telemedicine and e-health applications such as remote ECG (electrocardiogram), remote EEG (electroencephalogram), the treatment of several chronic diseases based on glucose levels in the blood and any remote medical assistance application that aims to enhance the patients' conditions and reduce the costs of medical treatment and hospitalization.
The tasks performed by the nodes in a WBAN, and in general, in any WSN, including sensing, data processing and communications, incur energy consumption. The wireless communication process constitutes the major power consuming task [17]. As nodes implanted on or deployed around the body have a very small form factor in pursuit of user comfort, batteries to power these devices are kept small, and hence energy storage capacity becomes a relevant issue. Most applications of WBANs restrict nodes to not require replacement of the battery over long periods of time; for example, a pacemaker or a glucose monitor is supposed to last for at least 5 years. Thus, energy-aware strategies have to be devised to keep nodes working properly over the required time duration. The network lifetime is defined as the time between the moment the entire WBAN is turned ON and the moment that the first node runs out of power, so energy saving strategies should support uniform energy drain, focusing on balancing power consumption among all the nodes comprising the network [18].
Another important issue is the constraint related to RF power, namely the consequences of the body's reaction to electromagnetic radiation and the localized specific absorption rate (SAR) in the body. To show the magnitude of the situation, sensors in a WBAN are required to broadcast data at low power due to heating of the radio chips that transfer heat to the tissues that form the muscles and causes harm to the WBAN user (burning or even malignant cell degeneration) [19].
Besides the aforementioned issues, several causes of energy waste have been identified in WSNs, including collision, overhearing, idle listening, over-emitting, control packet overhead and traffic fluctuations. Collisions occur when two or more nodes try to access the communication channel simultaneously. Idle listening is when a node listens to a channel that lacks traffic. Overhearing occurs when nodes receive packets that are not intended for them. Control packet overhead happens when a node adds too many control headers to the payload, and over-emitting means that many retransmissions are required to make a packet reach its destination [20].
The seven-layer OSI model was originally designed for wired networks. Each separate layer has its own set of protocols, and communication only occurs between adjacent layers in a stack fashion [21]. Though layered architectures like the OSI model have been used in wireless networks, they are not the best choice for WSNs due to the constraints imposed by the scarce battery and processing resources in this type of network [22]. Many proposals have emerged to ameliorate this issue in WSNs; one approach that has been considered to optimize the management of the scarce resources by exploiting the interdependence between the different layers is cross-layer design [23].
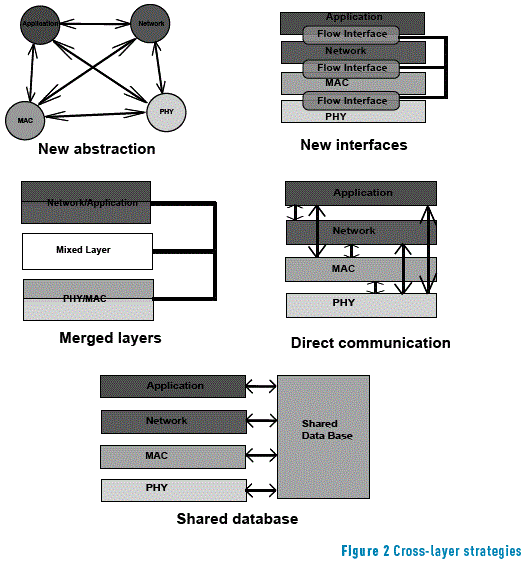
Cross-layer design basically performs a violation of the layered hierarchy by allowing protocols from different layers (adjacent and non-adjacent) to exchange information and relevant parameters. The cross-layer approach proposes various alternatives to the traditional layered model: The creation of new interfaces to manage the connection and the flow of information between layers; The merging of adjacent layers, where a new ''super-layer'' is created by merging services provided by two or more layers; vertical calibration across layers, setting a priori information obtained from layers or updating it based on parameters at runtime; new abstraction, which defines a non-layered architecture to have functions similar to those of the traditional protocol stack. Implementations of the cross-layer approaches have also been proposed based on direct communication between layers-(with exchanges of information between layers performed at runtime)-, a shared database across layers-(with a new layer-like scheme that performs the storage and retrieval of layer-related information), and a completely new abstraction (innovative implementations aimed at replacing the traditional stack like scheme) [15, 24] (see Figure 2).
An efficient cross-layer approach should provide schemes to avoid all the aforementioned sources of energy waste by promoting novel trade-offs between layers to enhance the wireless communication process and simultaneously extend the network lifetime.
3. Taxonomy: cross-layer approaches for WBANs
In this section, the different studies are classified by the communication layers involved in each cross-layer strategy. This survey details how each approach works (as described by the authors in the original paper), its main problems and shortcomings that represent open issues for future research, and a critical analysis of the performance results as originally presented by the authors.
3.1. PHY and link:
The aim behind a cross-layer strategy that involves the layers at the very bottom of the stack is to enhance the protocol performance by a synchronized management of the medium access strategies and the configuration of the devices used in the transmission and reception of data (transmission power levels, SNR, battery level, etc.). A priori knowledge obtained from one such layer helps improving parameters or procedures in the other layer. For example, in [25], the authors present an energy-efficient cross-layer optimization for wireless personal area networks (WPAN) that can be applied to WBANs. The authors propose that an SNR (signal to noise ratio) can be set for maximizing the energy efficiency and that this optimum SNR value depends on the ARQ (automatic repeat request) scheme on the MAC layer. This approach mitigates interference by multiple access (MAI) using multi carrier spread spectrum (MC-SS) modulation. On the MAC layer, nodes contend under a CSMA/CA scheme to request transmission. The network coordinator allocates the slots as a response to the requests, and every node is allowed to send data in its corresponding slot in a TDMA fashion, so it is assumed that the nodes use the ARQ scheme as an error recovery mechanism. The metric of energy efficiency is defined as the ratio between the efficiency of the transmission goodput of the ARQ scheme (calculated as the product of the efficiency of the throughput of the ARQ scheme and the residual frame error rate (FER)) and the average energy consumed in the transmission of a frame. This metric is used to calculate an optimum value of SNR because a low value of SNR increases energy consumption due to the number of retransmissions required, and a high value of SNR increases energy consumption because more energy is needed to transmit a single frame.
The authors executed an experiment to test the performance of SNR-ARQ cross-layer by running a simulation using an MC-SS link-level simulator employing the signal to noise ratio as the input parameter. The experiment showed that throughput and goodput metrics improved performance as the SNR increased for various ARQ schemes. As energy consumption increases for both low and high SNR values, due to increased retransmissions and higher transmission power for data frame respectively. The experiment revealed an SNR value that permits to achieve efficient energy consumption while improving throughput and goodput metrics for various ARQ schemes.
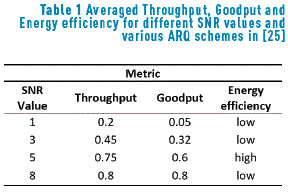
Table 1, shows the averaged performance of throughput, goodput and energy efficiency metrics regarding various ARQ schemes for different SNR values.
3.2. PHY and network
Information gathered at the physical layer can help make routing decisions.
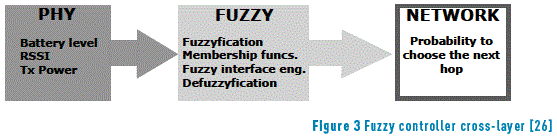
It should be obvious, for instance, that in a cross-layer approach aimed at saving network energy, the routes should not involve nodes close to battery depletion, so the information of the battery level should be available to a node to make its routing decisions; In [26], it is proposed a novel protocol based on fuzzylogic. According to the authors, taking the minimum number of hops as a rule to choose a node as the next hop is not efficient because, as a consequence, the nodes on that route will quickly run out of power if is repeatedly chosen and once that route is offline, the process will be repeated in the same fashion with the remaining routes. The proposed protocol runs an algorithm that uses two main components, a fuzzy controller and a cross-layer module that gathers parameters from the physical layer. The algorithm changes the router node dynamically using the fuzzy controller, and the node is aware of energy changes in the neighbors. Three parameters are collected by the cross-layer module: the neighbor's battery level, the received signal strength (RSSI) and the transmission power of the node. These parameters are fed as inputs to the fuzzy controller, and the output is the probability of choosing a node as the next hop (see Figure 3).
The algorithm consists of four steps. Fuzzification of the input variables maps the variables to the appropriate fuzzy set and passes them through a structure of fuzzy logic rules.
Triangular membership functions are used to obtain the magnitude of the participation of the energy level of a node in a fuzzy set. The fuzzy interface engine adds rule outputs and unifies them based on the rule weights and the max-min interference method. In defuzzification and fuzzy control, the output of the fuzzy controller is obtained and the nodes learn adaptively by making their own decisions while they send and receive packets.
Although this protocol does not take mobility into consideration, it achieves high rates of energy saving by consuming power uniformly through the network and checking the energy levels of nodes to make next hop decisions.
The fuzzy protocol was simulated using an AODV (ad hoc on-demand distance vector) algorithm modified to implement the proposed energy-efficient routing algorithm. Thus, a comparison was made between AODV and the AODV modified with the proposed approach.
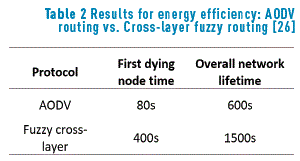
An experiment to test the performance of both protocols was conducted to evaluate energy efficiency. The experiment was a simulation of a network comprising 36 nodes, every node with inital battery load of 300J and simulation run time of 1000s. Two metrics were observed, the first one, the time of the first dying node; simulation results show that the residual energy in the first-dying node lasted over 5 times more in the fuzzy AODV than in the original AODV.
And the second one was the overall network lifetime, and the simulation shows that the network lifetime is prolonged when using cross-layer fuzzy-based routing, Table 2 refers the experiment results for the network using AODV routing protocol and the cross-layer fuzzy protocol. It is clear that the cross-layer fuzzy protocol outperforms the AODV protocol regarding energy consumption as it increases individual nodes lifetime and the overall network lifetime. Table 2:
3.3. Link and network
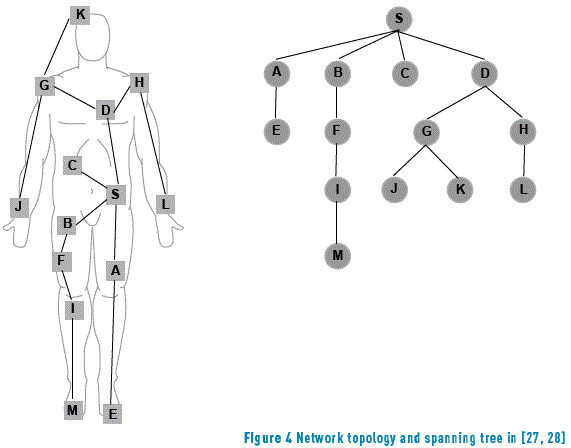
Taking advantage of the characteristics and parameters of a medium access strategy allows cross-layer protocol designers to implement energy saving routing approaches. It is of great help to avoid contention-based strategies by the inclusion of energy-efficient network procedures determined by a fair assignment of transmission slots at the link layer. In this aspect, the next two strategies based on TDMA and spanning tree topologies present energy efficient crosslayer schemes between link and network layers. In [27], the authors propose a cross-layer approach between the MAC and network layers, named the wireless autonomous spanning tree protocol (WASP) that uses a spanning tree (see Figure 4) for medium access control and routing. Each node in the tree tells its one-hop tree children the time slot they are allowed to send data; this process is done by sharing a special message called a WASP scheme. Each node sends a WASP scheme to its children to inform them when they are allowed to transmit, and the children respond by sending their own schemes in the corresponding time slots.
The entire process until when the farthest node sends a data package to the sink is called a cycle. The cycle begins when the sink node sends its scheme to its children in the first time slot. In the following slot, the sink's children, called the level 1 children, send their data to the sink and send their schemes to their children, the level 2 children. In the next slots, the sink keeps silent while level 2 children send their data and scheme and the level 1 children enter
A contention slot to allow new nodes to join the network. In the next slot, the parent nodes forward their children's data towards the sink, and the last slot is the contention slot of the sink. This approach contributes to energy saving because nodes can sleep during their silent slots, and nodes also save energy in routing as they only forward data to the parent node. Overhearing and collisions are avoided due to the slotted mechanism to access the medium. Three major shortcomings are identified for this approach: 1) it lacks an optimum calculation of time slot length, which can cause nodes to fall into idle listening and introduces delays in packet forwarding; 2) nodes that are parents to several nodes are prone to sleep less than other nodes and thus have a shorter lifetime; 3) the spanning tree does not support mobility, which is a constraint in WBANs.
The performance of WASP was compared against the results obtained using a combination of a CSMA scheme with a fixed routing protocol in a scenario composed of a sink and 13 nodes in a spanning tree topology (see Figure 4).
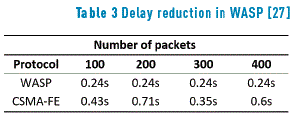
The latter scheme showed a packet loss close to 30%, and a few nodes could not succeed at transmitting any packet, while there was no packet loss using WASP.
Concerning the delay, WASP exhibited a maximum delay of 0.35 seconds, while in the other protocol there were nodes whose delay exceeded a limit of 0.8 seconds. Table 3, as shown in [27], presents a comparison of the end to end delay in the transmission of different numbers of packets for a node located at the lowest level in the tree hierarchy. The comparison was made between WASP and the combination of a CSMA scheme with a fixed routing strategy (CSMA-FE).
A drawback of WASP is that there is no mechanism to supply the coordinator absence in the case of coordinator energy depletion. In WBANs, the architecture cannot be tied to a central node organization if there is no way to replace the coordinator in a failure, so this approach should take into consideration concepts derived from opportunistic and mobility-aware schemes. WASP acceptably meets QoS requirements such as transmission throughput, high packet delivery ratio, fixed end to end delay and low energy consumption.
In [28], authors showed the design of a cross-layer protocol called CICADA (Cascading Information retrieval by Controlling Access with Distributed slot Assignment). This protocol arranges nodes in a spanning tree and divides the time into slots to avoid collisions and idle listening; the data are forwarded in cycles, and the time slots are assigned in each cycle. Each cycle is divided in a control subcycle and a data subcycle. In the control subcycle, parent nodes send the control and the data schemes (the slots allocation), and the children are assigned their transmission time slots. The control scheme directs the order in which the children send their own control schemes to their children and the data scheme points when the children can send their data in the data period of the data subcycle; every ending slot in the data subcycle is used for the contention of new nodes.
In the data period, the nodes receive data from their children and send it (along with their own data) to their parents. When a node sends a packet, it also sends additional information that consists of its own data period and a waiting period. In case a node has no data to send, it sends a HELLO packet with only the additional information. This HELLO packet helps parent nodes to determine whether their children are alive; if a parent has not received data or HELLO packets from a child node in two consecutive cycles, the parent assumes this child to be offline. If a child node has not received any schemes from its parent in two consecutive cycles, it begins to contend for another parent in the contention slot by sending a join request packet with the number of slots it needs to send data.
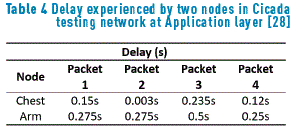
To evaluate the performance of CICADA, the authors set up two simulation scenarios composed of a sink and 13 children nodes disposed in a spanning tree topology (see Figure 4). In the first scenario, a node that belongs to the first level of children below the sink is moved for 10 seconds to join a new parent at the second level and moved to its original position again. Hence, all its children are affected because there was one extra hop to reach the sink; as a consequence, a delay of over 0.2 seconds is experienced by the lowest children in the branch due to the process of joining a new parent and joining the sink back again. In the second scenario, a node on the third level of the tree is moved nearby the sink to simulate the movement of an arm, and the consequence is the reduction of the delay in transmission for this particular node as it joins the sink as its new parent.
Table 4 shows the end to end delay performance for two nodes, one node located at the chest, a direct sink child node and less susceptible to disconnection due to mobility while the other one is located at one arm, two hops away from the sink and directly affected by body mobility.
CICADA constitutes an improvement over WASP, exhibiting the same energy saving benefits by avoiding idle listening, overhearing, and collisions and adding the possibility of a dynamic and mobile network because nodes can join new parents. CICADA is prone to network disconnection when a parent dies, as no method for a node to become a parent is mentioned and orphan children would reduce the lifetime of the remaining parents.
One major drawback identified in CICADA is due to the node joining (mobility) mechanism because it lacks a security strategy to prevent intruder nodes or nodes that belong to a coexistent CICADA network in a hospital scenario from joining the network in an unauthorized way. Another issue identified in CICADA is that the tree cannot have very deep branches because a node on the upper level just below the sink will incur high duty cycles, and the energy depletion of this node will happen sooner, while lower level nodes will undergo longer sleep times and are prone to suffer from packet loss, as CICADA does not implement any packet queuing mechanism; this can cause the reliability of the medical network to be compromised.
CICADA considers that one packet is generated for a single data cycle, so high load applications will make the nodes undergo long duty cycles, as more slots are needed for transmissions, and as a consequence, energy will be consumed faster.
Reliable medical data delivery from the sensor nodes to the sink requires a network layer aware of the channel variations and the state of the links binding the nodes in the network. A good example is the approach presented in [29], which proposes a cross-layer strategy aware of communication interferences and changes in network topology in a joint manner to fulfill the data reliability requirements of the WBAN. The strategy is conceived as an improvement of a previous one developed by the authors called CBAS (centralized body area network access scheme) [30]. The aforementioned improvement consists of the incorporation of a network layer strategy to enhance the packet delivery ratio (PDR), exploiting information gathered at the link layer about the quality of the links in the WBAN in such a way that the most reliable links can be identified in a distributed manner, adding an approach of an adaptive duty-cycle in the nodes to increase energy savings.
The use of CBAS as an underlying MAC layer alleviates service interruptions due to the coexistence of several wireless sources in the channel and thus reduces medium access latencies. The proposed network layer approach takes information from the link layer to take into account channel and link fluctuations, such that the trade-off between the PDR and delay is reduced in transmission scheduling.
There are two fundamental premises for the design development: 1) Although TDMA strategies are energy efficient, they are not aware of limited periodic access to the channel under the presence of coexistent wireless technologies (WiFi, Zigbee, Bluetooth, etc.) and 2) to face unpredictable changes in the topology, an online scheduling mechanism based on link quality is preferable.
Hence, to take advantage of TDMA energy saving characteristics and to solve the problem of high latency in contention-based WBAN access schemes, under high data rates and high transmission power, in CBAS, the sink tests the spectrum to find free slots. Once a free slot is found, a transmission orthogonal to the frequency and/or time begins. This strategy allows the WBAN to operate reliably under environments characterized by coexistent technologies and at the same time allows nodes to transmit in an interference-free time slot.
The authors point out that several previous studies indicated that WBANs can confidently benefit from free slots that occur along the spectrum, even in areas where coexistence with wireless signals is expected, because there are enough free slots and the transmission scheduling is successful most of the time. When the sink detects any free slot it sends an RTS (request to send) packet to inform other technologies' devices that a transmission will take place at the WBAN. Then, the sink sends a command in the control channel to inform that nodes in the WBAN are allowed to start a transmission. When the nodes receive such a command, they wake up and start the contention for the time slot; the contention winner is decided by a parameter called ''weight'', which is calculated based on the quality of the link between each node and the sink and by the number of transmissions that a node has made previously to guarantee a fair distribution of the transmission opportunities between all the nodes. The node with the highest ''weight'' is the one with the best chance to get the slot.
When a node wins the contention, it sends a ''win-packet'' to the sink informing it that it is ready to transmit, and then, to reduce the probability of collisions, the sink sends a high power packet to prevent transmissions from other nodes.
The design is not restricted to unicast transmissions, given that some nodes are located in far positions, such as the heel, so that the quality of the link with the sink is low, and hence other nodes have to forward the transmissions between such nodes and the sink. When a node sends a data packet, its neighbors save a copy of the packet and remain active until an ACK (Acknowledge) signal comes from the sink. In case of no ACK, a neighbor node forwards the copy, and once the ACK is received, all neighbors go into sleep mode.
It is of note that this cross-layer design provides a mechanism for adaptive duty-cycles through the application of policies or conditions for the management of the preferences of a node that control the amount of time a node should be in active mode.
For the cross-layer scheme in [31], the MAC proposal of CBAS [30], is modified to achieve a dynamic scheduling scheme in order to improve the Packet Delivery Ratio (PDR) observed in statically scheduled WBANs. The exploitation of flat fading and symmetric characteristics of the channel permits to derive the power needed to perform a successful transmission to the sink node. In this scheme, the sink broadcasts a command packet to indicate that the channel is available for the WBAN, using that command the nodes infer the minimum power needed to deal with the attenuation of the link towards the sink. If the link quality is very poor, nodes abandon the transmission. In the second stage, nodes review the history of their participation in transmissions, in order to calculate a backoff window for the dynamic scheduling and fair allocation. For this purpose, nodes calculate a weight metric that depends on the number of times that a node has responded to commands of the sink node and participated in transmissions, nodes with higher weights have shorter backoff windows.
When the node with the highest weight completes its backoff window, then it sends a ''win packet'' to inform that is ready to start a transmission, then the sink sends a high power packet to prevent other nodes in the network from starting transmissions. This scheme is extendable to multi-hop routing, when other nodes receive the ''win packet'' they keep listening to save a copy of the data packet and make a retransmission in case of no ACK from the sink. The scheme shows a significant improvement in the PDR, especially in multi-hop mode, with respect to statical scheduling mechanisms.
The IEEE 802.15.6 WBAN standard [32] suggests one-hop star and 2-hop extended star topologies for health monitoring applications and defines seven category levels for packet priorities. In [33], a cross-layer based data dissemination algorithm adopts a reverse tree routing mechanism that aims to reduce the number of hello beacons exchanged for establishment and maintenance of the network topology in 2-hop extended WBAN. The reverse tree has two build phases, a discovery phase for network coordinator ID broadcasting to all the nodes in a beacon message and a reverse tree route computation phase for next hop designation in the network.
In the discovery phase, the coordinator broadcasts its ID, and one-hop neighbors forward this ID to the 2-hop neighbors, which know not to forward the message any further by checking a hop counter in the message. To compute the reverse tree at the next phase, one-hop nodes choose the coordinator as their next hop while 2-hop nodes select as their next hop, the forwarder node whose beacon retransmission was the first received, that is, the hop with the least delay.
To support the IEEE 802.15.6 traffic differentiation, 3 levels of priority are defined (in order of priority) Emergency Mandatory (EM), Delay-Sensitive (DS) and General Monitoring (GM). The channel access schemes are CSMA/CA and Slotted Aloha. EM and DS packets are forwarded in the EAP1 (exclusive access period) and EAP2 periods of the super frame, while GM packets can be forwarded in the RAP1 (random access period), RAP2 and CAP (contention access period) periods. Although the reverse tree scheme proposes an efficient approach for route computation, it is not clear how the topology reacts in terms of energy efficiency in the case that a forwarder node performs as the next hop for multiple 2-hop nodes, and in the case of energy depletion of a forwarder node, there is no mechanism for a 2-hop node to detect whether it is still connected to the network or not. As a result, the packet loss rate could dramatically increase in such a situation.
An opportunistic multi-hop routing strategy, presented in [34], involving MAC and Network layers, exploits the remaining energy in the batteries and the proximity of relay nodes to the sink in order to improve the reliability of WBANs, represented in the Packet Delivery Ratio metric. The scheme considers the use of relay nodes for packet forwarding towards the sink node. This protocol is focused on making the right selection of the relay node with better energy resources and closer to the sink node, to guarantee a reliable data delivery and a fair distribution of data load among all nodes in the network.
Based on a traditional opportunistic mechanism, a source node broadcasts an RTS (Request to Send) packet and waits for a CTS (Clear to Send) response from a potential relay node. The idea is to choose the relay node whose CTS packet arrived first. Potential candidates for data forwarding calculate a time metric that defines the delay after which the relay node can access the channel for broadcasting its CTS packet. This time metric depends on available residual energy in the battery and the proximity to the sink node that is deduced from the RSSI value of the last beacon packet received from the sink. Relay nodes have to make sure that they are indeed closer to the sink than the source node itself, then a relay compares the RSSI of the beacon received from the sink and the RSSI of the RTS packet received from the source node.
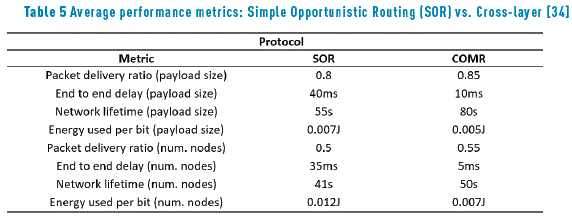
When a relay node broadcasts a CTS packet, all other nodes go to sleep mode and the source node sends the data packet and waits for the ACK. The protocol performance regarding Packet Delivery Ratio was tested against a Simple Opportunistic Routing strategy in scenarios with varying payload lengths (10 to 90 bytes range) and varying number of nodes in the network (4 to 12 nodes). The results showed that the opportunistic cross-layer protocol was more reliable in all the cases. Table 5 shows the results for average network lifetime, end to end delay, packet delivery ratio and energy consumed per bit, obtained by making the simulation and comparison between a simple opportunistic routing strategy and the opportunistic cross-layer scheme.
3.4. PHY, link and network
A cross-layer approach between the network, medium access and physical layers aims for energy saving at the nodes by managing energy-efficient routing schemes that try to balance the traffic load in the whole network and reduce the number of retransmissions, while being aware of the power levels to reach the hops in the routes. The strategy devised in [35] proposes to balance the traffic in the WSN and to limit the retransmissions over each wireless link. The traffic balance is achieved by determining a set of routes for the node to send the traffic through multiple paths instead of sending data over a recurring path. At the MAC layer, a retransmission control mechanism is proposed to determine a retry limit of each link so the probability of packet delivery exceeds a specified threshold called the ''target per-hop success probability''.
After obtaining the average energy consumed by each node per unit of time, an algorithm is run to obtain the set of optimal routes and the vector of retry limits that minimize the energy wasted by the greediest node in the network when this node sends a packet to the sink. Compared to basic routing schemes, energy savings of up to 15% were achieved by balancing routing and savings of up to 5% were achieved by the allocation of the retry limit for each link.
This approach does not consider the unreliability of routing paths due to wireless channel complexities, so the balance proposed with the retrials vector will be inconsequential. Because the mobility is not taken into consideration, a real network deployment running this approach will fail, as fixed sets of routing paths will change frequently due to new positions of nodes and ever-changing link quality.
3.5. PHY, link and application
Regarding these three layers, a cross-layer framework presented in [36] considers that the main sources of energy consumption in WBANs are the data transmission process on the PHY layer, the optimal bandwidth allocation on the MAC layer and the encoding phase on the application layer. The Energy-Rate-Distortion (E-R-D) problem is formulated as an optimization problem. The objective function is the minimization of the total energy consumed in the data transmission and data encoding phases, computed based on channel parameters such as the fading magnitude, the pathloss coefficient, and the energy dissipated at the modules for discrete wavelet transform and quantization.
The optimization model considers the following constraints: 1) The maximum delay allowed in the transmissions cannot be larger than the delay threshold; 2) the maximum distortion rate at the encoder and 3) the available bandwidth that can be allocated to the nodes in the network. The bandwidth allocation scheme proposes an adaptive-variable approach where timeslots are optimally assigned according to the requirements of the PHY and application layers.
The optimization aims for an optimal allocation of resources and to provide the best parameters to satisfy the data rate and distortion constraints and jointly minimize the energy consumption.
The E-R-D model proposed by the authors offers a delay and distortion constrained optimization framework that obtains the most accurate parameters on the involved layers to minimize the energy consumption, namely, the wavelet filter length, the optimal transmission rate, the compression ratio, the timeslot length and the bandwidth allocation.
Though the authors apply the model to a common scenario in WBANs as the transmission of an EEG (Electro Encephalon Graph) node, they lack accurate body channel characterization, adjusting the channel between the EEG node and the PDA (sink) to a flat channel model with free space loss, and do not take into account fading or shadowing due to human mobility. Hence, the obtained results could not accurately fit a real WBAN wireless channel behavior.
The capability of batteries to recover charge when they remain idle for a certain period depending on the state of the electrochemical components of the battery and the duration of the idle period is used by the authors of [37] to devise a battery-dynamic driven TDMA protocol for WBANs deployed in healthcare applications. This TDMA scheme takes into consideration the battery recovery dynamics, the state of the wireless channel and the QoS constraints regarding packet delay and packet loss.
To extend the lifetime of the batteries, the scheme is to maximize the idle periods, keeping a tradeoff between the packet delay and the packet loss introduced by the queuing mechanism of packets utilized to reduce the number of timeslots required in data transmission. On the MAC layer, the nodes decide to start a transmission only when the channel state, estimated using the signal strength of the beacon messages sent by the coordinator, is good enough and when the packet buffer size is large enough as well.
Although this approach prolongs the battery life span of the nodes, and the packets are reliably delivered in a timely fashion in the guaranteed time slots of the super frame, some drawbacks are identified as well. In cases where the nodes increment their idle state length to recover battery power, they are also prone to an increased packet drop rate and average delivery delay because some packets are held in the buffers for long periods. As seen in the results for the ECG sensor, the delay limits reached by this protocol are very close to the QoS edges for medical applications, so the protocol is more prone to failure in fulfilling such end to end delay requirements. The channel model used does not fit a real WBAN scenario, as the Nakagami distribution cannot reflect the loss and fading characteristics of the human body. Besides, network mobility is not taken into consideration.
In [38], the authors propose a cross-layer approach between the PHY, MAC and application layers. In the strategy presented in this approach, they set an energy consumption model that depends on the number of retransmissions and the length (in time) of the packet transmission process (transmission and reception). It is considered that the number of retransmissions depends on two probabilities, one a success probability on the PHY layer that differs for coded and uncoded packets because of their different lengths. The other success probability of channel access depends directly on the number of nodes forming the network and the probability of a node to access the channel that depends on the priority of the node in the network.
On the other hand, the packet transmission length comprises the time used in the transmission and reception frames. Then, the energy consumption is computed as a function of SNR and packet length that contains terms that consider the consumption in the RF modules and circuitry, the encoder and retransmissions.
The approach considers a star topology network as defined by the standard and does not take into consideration two-hop extension. The PHY layer is set in the IR-UWB band using a single pulse or burst of pulses waveform with OOK (on off keying) modulation and BCH (Bose Chaudhuri Hocquenghem) coding. The channel is modelled as AWGN (additive white Gaussian noise), and the reception scheme is a non-coherent energy detector that makes decisions based on the energy level of the signals in the symbol time. For the MAC layer, a beacon mode with superframes is used along with an S-Aloha access phase mechanism that allocates time slots according to node priority.
To verify the performance of the approach, an energy efficiency metric is set as the ratio between the payload length (information bits) and the energy used for successful payload transmission (information bits that reach the receiver). This metric allows observing the trade-off between the payload length and transmission SNR to achieve energy efficiency in both coded and uncoded frames. The results show that for uncoded frames, the maximum value of energy efficiency is reached when using a maximum value of both SNR and payload length, while in the coded case, the energy efficiency value increases as the payload length increases and the SNR value decreases.
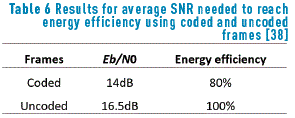
Table 6, shows the average SNR needed to achieve the maximum energy efficiency in coded and uncoded cases for payloads in the range of 5 to 255 octets, it can be seen that although the uncoded case reaches 100% of energy efficiency the nodes have to transmit at higher transmission power which can cause thermal and heating issues in the transceiver device.
It can be concluded that in the coded case, the error correction coding strongly helps reduce the energy needed for error-free transmission of long payloads, and hence the power needed for efficient transmission is less and the nodes save energy and avoid heating and thermal issues. The QoS requirements are satisfactorily fulfilled because the the IEEE802.15.6 provides the S-Aloha with various access phases for different node priorities, helping optimize the end-to-end delay, packet delivery ratio and reliability of the transmission.
3.6. PHY, network and application
In this particular cross-layer scheme, the physical layer configuration and routing strategies are strongly influenced by parameters and information that reside on the application layer and are defined by the characteristics of the data (amount, priority, utility, etc.). In [39], the authors propose a solution to the problem of efficient routing and present the allocation of bandwidth as a problem of linear optimization. They define a metric called network utility, with the goal of making a trade-off between the remaining energy in the nodes and the network throughput. This approach suggests forcing the packets to move across high energy nodes in a routing tree. The main problem is to increase the amount of nodes with a high probability of being accepted to join the routing tree, aiming at balancing the energy consumption and extending the network lifetime. The nodes are accepted into the routing tree by measuring their relative importance in the network context. The importance or utility of a node depends on the number of packets received or forwarded by that node and its level of available energy; once those measurements fall below a threshold, the node is put offline.
The protocol exhibits four phases: Topology Discovery, when nodes exchange HELLO messages to detect neighbor nodes and record them in a neighbors table; Energy aware routing, when a node selects a parent among nodes accepted for routing; this decision is based on the energy levels of the parent candidates and the energy of the entire routing path; Bandwidth allocation, in which the bandwidth is allocated in an efficient manner in the routing tree leaves, proportional to the priority of the data streams being routed through those leaves, the priority of a stream is defined by the variable a node is sensing; and at the Load Balancing Routing phase, in which nodes currently accepted in the tree switch their state to topology discovery and begin to save energy while allowing other nodes to perform routing duties in the tree.
This approach achieves energy savings and extends the network lifetime as a consequence of nodes switching periodically between routing duties and the offline state. Quality of service (QoS) is also achieved, as data streams are prioritized depending on the variable sensed. It is important to mention that the protocol was simulated under ideal channel conditions. It was shown that network performance has a strong dependence on the sink location in the body.
The authors compared the performance of the protocol with the results obtained by solving the formulation of an integer linear program (ILP) with the objective function of increasing the number of high priority nodes in the routing tree at the highest possible data rates while balancing energy consumption to extend the network lifetime. The evaluation was done under the following premises: i) 15 nodes network; ii) two test cases, one with 5 high priority nodes in the routing tree and the other one with 8; iii) two test cases for sink location, one with sink at the waist and the other one with the sink at the ankle; iv) a run simulation of 2000 seconds; v) initial battery load of 2 Joules.
The performance evaluation showed that the utility increases with the increase of high priority nodes, and, as a direct consequence, more nodes are accepted as traffic sources with the best data rate. In both evaluations (5 or 8 nodes, sink at waist or ankle), the gap between the ILP solution and the solution provided by the protocol is small and tends to remain constant as the number of high priority nodes increases. Regarding energy consumption, the protocol outperforms the ILP solution when the sink is located at the waist.
Table 7 shows the average remaining energy (percentage of initial load) in the nodes when the routing tree is composed of 5 or 8 nodes and the sink is located at the waist. The average result of the protocol is compared with the integer linear program solution obtained using mathematical optimization software after running the simulation for 2000 seconds.
3.7. All layers involved
A new concept different from the notion of a stack is introduced in this cross-layer approach, where all the layers in the communications model are supposed to share information and for instance, all routing decisions are endorsed by the parameters and information gathered on the other layers. Having that in mind, innovative mechanisms have to be designed to cope with this data sharing among layers, namely, shared data bases, shared memories and participation in the communication process oriented by parameters obtained on all layers simultaneously. In [40], the authors designed a protocol stack to solve problems caused by mobility, low reliability and time varying links in WBANs. The stack is based on multihop transmissions and avoids dependence on a network topology for routing duties. The protocol stack uses a MAC layer based on TDMA and a routing strategy called ''gossiping''. Both medium access and network strategies join to broadcast data in a reliable, robust and fast manner with little overhead.
The protocol assumes that all nodes have enough space in the cache to store a data item from every node in the network, so in each sending round, a node stores the last data item received from the other nodes. The sensor nodes send a packet that consists of data items, and a node sends at least its own data item and another from a neighboring node. Based on the fixed number of data items per transmission, the number of nodes in the network, the node's ID and the order number of the current sending round, a node divides its cache to choose the amount of data to be sent in the round. This choice is designed in such a way that different nodes avoid sending the same data items at the same time and a node avoids sending the same information in consecutive rounds.
Although the MAC layer is based on TDMA, there are no synchronization problems given the small size of the network and the presence of a sink node with better power and energy capabilities to broadcast packets along the entire network that allow the nodes to correct clock drifts. The protocol provides a transmit power adaptation mechanism based on two metrics, an outlink quality metric and a network connectivity metric. This mechanism aims at obtaining a quick reaction by increasing the transmission power when a postural change is perceived or a network disconnection occurs. Both metrics are calculated based on the history of the links and their state in the transmission of the last frame.
This protocol ensures efficiency in energy consumption as it prevents retransmissions. Data routing does not depend on topology because the nodes broadcast information without concern for the relative position of the intended receiver, and simultaneously, the latency is reduced because all nodes can reach the sink using the power adaptation mechanism. The protocol stack needs to optimize listening on active time slots to reduce the consumption caused by idle listening.
We observe the following issues regarding this strategy: Nodes with few neighbors or that are almost isolated from the entire network (say, a node in the ankle) are likely to suffer synchronization problems, as they are prone to lose connection with the sink node, and the power adaptation mechanism could help with high energy consumption by increasing the power level in this type of situation. This protocol lacks a traffic prioritization scheme, as all data items are treated equally, and such an assumption does not fit into the WBAN context.
This stack was tested against the performance results of WASP [27]. The authors mention that a major aspect that makes the protocol stack robust is the power adaptation mechanism that prevents network disconnections and reduces the variation in latency derived from postural changes, while in protocols like WASP, the WBAN is unreliable because of the time the network takes in the reconstruction process of the tree after a disconnection.
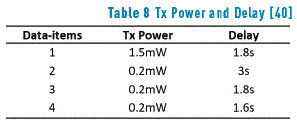
Table 8 shows the average delay and transmission power in network nodes for different amounts of data items. The protocol efficiency is confirmed in the table, as latency is reduced as the number of data items increases.
4. Classification
In this section, we summarize the investigations reviewed above by making a comprehensive classification based on the cross-layer schemes illustrated in Figure 2 (merging layers, new interfaces, new abstractions, etc.) that correspond to each approach.
4.1. Creation of new interfacesThis category can be subdivided in two subcategories, upward information flow and downward information flow. The upward flow occurs when a higher layer protocol needs run-time information from a lower layer, so the new interface layer is set from the lower to the higher layer. The opposite happens in downward flow and the new interface deploys a data stream from the higher to the lower one [15].
In [25], it is noticeable that the optimum value of the signal power needed at PHY to reach an SNR value capable of establishing a tradeoff between energy consumption and a reduction in retransmissions depends on the parameters provided by the ARQ error recovery scheme in the MAC sublayer of the Link layer.
In [26], the fuzzy controller works as a new interface between the PHY and network layers. The fuzzy logic is fed by parameters obtained on PHY, and the routing decisions at the network layer are taken based on the outputs of the fuzzy controller. Something similar is presented in [33], where the set-up of the tree for network routing is bound to the reverse process of beacon broadcasting in the medium access layer.
Almost every cross-layer MAC protocol is set on the basis of a new interface in the stack. A good example is the battery-aware MAC in [37], in which two processes on the MAC sublayer depend on the battery dynamics principle, the inactive period setting and the mechanism for queuing packets.
4.2. Vertical calibration across layersThis cross-layer scheme refers to a multi-parameter adjustment across layers having foundations at particular layer parameters. It is considered that from a joint parameters setting at several layers, more benefits can be obtained in the overall protocol performance than by just updating one single layer's parameters and leaving the remaining layer protocols untouched [15].
In this survey, we have included two examples of this cross-layer technique. It can be seen in [35] that by using the calculations of average energy consumed in the transmissions, the routes are arranged at the network layer and a vector of retrials is set on the MAC layer adjusting the power consumed in the transmissions to benefit the energy-aware performance on the PHY layer.
In [32], the amount of data (payload length), priority of sensed data and signal to noise ratio parameters are considered jointly to control the number of retransmissions and the duration of packet transmission to achieve the maximum energy consumption efficiency. The entire energy consumption model computations depend on how these parameters are adjusted in run-time.
4.3. Merged layersThis technique is only seen between adjacent layers, and it is considered that a new ''super-layer'' supplies the services of the fused layers, adding benefits to the energy consumption and the QoS requirements of both at the same time [15]. Three designs of this category presented on this survey have a mix between MAC and Network layers in [27-29]. It is a fact that the routing strategies are strongly supported by the medium access mechanism provided for timeslot allocation, and it can even be said that the routing scheme is somehow absent and the data forwarding duties are entirely conferred to the medium access scheme.
In [31, 34], besides the mix between MAC and Network layers, the PHY layer is involved as well because in the former the transmission power is adapted aiming to exceed the minimum boundary imposed by the attenuation of the channel. And in the later the RSSI is used to obtain the delay to send the CTS packet by the relay nodes.
4.4. Shared databaseIn general, a new layer to which all other layers have access and that can make queries and store information related to other layers to improve the performance of specific protocols or the entire stack performance is called a shared database [15]. The most common example of such a technique in cross-layer design is an optimization program. In both approaches presented in [36, 39] different parameters such as available bandwidth, battery energy, target data rate, allowable distortion rate, data amount and data priority are fed as variables (and depending on the situation, as constants) for objective functions and constraints in optimization programs that consider tradeoffs between energy efficiency and the fulfillment of QoS requirements.
4.5. New abstractionsThe term ''new abstractions'' in the cross-layer context refers to new schemes in the communication process away from the traditional stack model and the concept of independent layers with independent protocols and the boxing and un-boxing mechanism that the protocols in the stack fashion provide for passing information across layers [15]. We consider that the protocol stack [40] surveyed in this article fits into this category, as it presents a novel strategy such as ''gossiping routing with transmit power adaption'' that provides a new look at the protocol design and poses a good example of the violation of hierarchy between layers that is a major concept of cross-layer design.
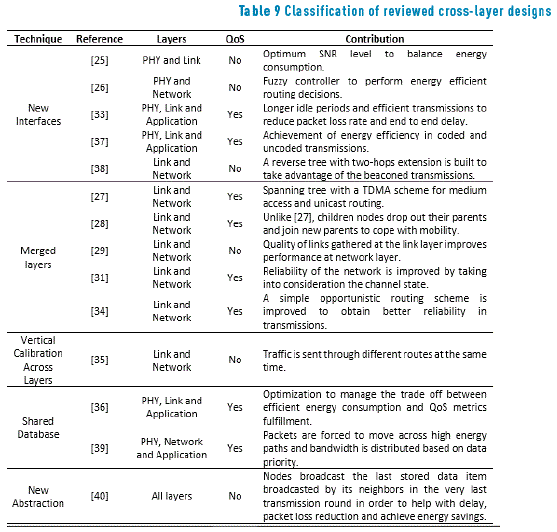
Table 9 summarizes the main characteristics of the cross-layer designs reviewed in this survey. All designs are classified by the layers involved in the cross-layer approach, the cross-layer design deployed and whether they support quality of service (QoS) and nodes mobility.
5. Open issues and future research
5.1. MobilityPostural changes of the human body induce alterations in wireless links, path loss increases as the distance between two connected nodes changes due to body movements. Generally, in wireless networks it is supposed that power gain is decreased by a factor dη, where d represents the distance between transmitter and receiver, and η is the path loss coefficient of the medium used for waves propagation, in the air (free space) η is considered to be η = 2, but regarding WBANs this is far from being true since in this kind of networks the transmission scheme is randomly inserted between LOS (Line of Sight) and NLOS (Non-Line of Sight) modes which introduces significant variations to the pathloss coefficient as waves not only propagate across free-space, waves have to spread across human tissues as well.
Electromagnetic waves get significantly attenuated when they propagate through human tissues given that these are mostly formed by water, and human flesh is not an adequate medium for waves spreading as well. Hence, NLOS transmissions in the human body are, in general, not possible given that waves do not traverse muscles and tissues but diffract in the body. Then, LOS and multi-hop transmissions are suggested for WBANs, taking on count that isolated nodes are prone to experience higher loss.
Another negative effect due to body movements is the rotation of nodes, specifically the antennas, which causes changes in the direction and polarization of the radiation pattern. Little space between the antenna and the body surface disarranges the impedance of the antenna and the radiation pattern.
One major issue regarding mobility of nodes in WBANs is the Non-stationarity of the channel, imposed by the movements of the human body, in [41] a design of experiments (hypothesis test) is conducted to corroborate that body channels are in fact non-stationary. A WBAN topology comprising 4 nodes, a transmitter located at the left hip and 3 receivers, in the right ankle, the chest and the right wrist were used to sample different body channels in a variety of body postures which are common in office, home and car environments. The channel gain is partitioned in equal length intervals and two consecutive intervals are compared to test the average probability of stationarity in a single time window.
Kolmogorov-Smirnov, ANOVA and Levene tests confirm that the average probability of stationarity decays quickly for all of the body channels in the different environments, it is even pointed that channels can only be considered stationary within the first 500ms of the time window. Even postures like sitting in the office exhibit non-stationary body channels. The most important conclusion derived from the experiment's results is that small scale and large scale fading statistics are not practical in WBAN channel modeling given the nonstationarity of the channel that ensures that the probability density function in different and consecutive intervals of the time window is different, then the behavior of the channel cannot be partitioned to be modeled by fixed fading and shadowing statistical distributions.
Almost every protocol reviewed in this survey lacks support for mobility, which is fundamental in WBAN deployment. Several mobility models for wireless and ad-hoc networks can be found in literature, just to name a few: Reference Point Group Mobility Model (RPGM) [42], Random Waypoint Mobility Model (RWPM) [43], Random Walk Mobility Model (RWMM) [44], Random Gauss Markov Model (RGMM), Random Direction Mobility Model (RDMM) [45], and most of them can be adapted to describe WBAN situations.
Good examples of such adaptations are shown in [46], where they model mobility scheme is from traces of real postural changes in humans, two phases are derived: a posture selection phase from postural change probabilities and a nodes movement phase based on the posture selected. Meanwhile in [47] the model is built upon RPGMM and RGMM models, and by observing some correlations present in human movement.
MoBAN (A configurable mobility model for wireless body area networks) [48], which is a mobility model for WBANs developed in OMNeT++ network simulator [49] and used in the implementation of the cross-layer protocol in [40], this mobility model for WBAN is based on a description of the body movement as two stages, one related to local movement of the nodes which is characterized using RWMM mobility model; and group mobility stage led by the sink node and devised using RPGM mobility model.
It is clear that an efficient cross-layer protocol provides a better experience for a WBAN user by extending the lifetime of the sensors, but this benefit can be negated if the user cannot move because it would result in network disconnection. Mobility implies that nodes can leave and join different parent nodes without affecting the inner functions of the WBAN and avoiding additional energetic resources consumption. Then, new cross-layer approaches should focus on developing MAC and routing mobility aware schemes.
CICADA [28], for example is a mobility aware scheme but not as robust as WBAN requires, in the case where several sensors disconnect from their parents, the protocol does not seem to nimbly attend to all reconnections, keeping the network in such a state that the whole WBAN could be considered useless. In [50, 51], was presented the first algorithm to support WBAN mobility while remaining energy efficient, the LIMB (Loose association Implicit reservation for Mobile Body Sensor Networks) protocol. They propose distributing the nodes in two sets, one set comprises the nodes prone to mobility, which run the LIMB protocol to support mobility, and the other set comprises nodes prone to keep static, which run the LIMB protocol and another backbone cross-layer protocol.
5.2. IEEE 802.15.6Although up to date applications and developments for WBAN have been implemented on existing low data rate and low power existing standards such as IEEE 802.15.4 and Bluetooth, there exists a new standard devised exclusively for WBANs, IEEE 802.15.6, then new developments and releases should focus on leverage the benefits that the new standard brings. Current WPAN technologies do not meet medical regulations for WBANs, and do not give support to typical WBANs tradeoffs regarding low power consumption, ultra low power adaptivity, reliability, QoS, security, data rate, efficient bandwidth utilization and co-existence with other WBANs.
As WBANs operate in the vicinity, on/or inside the human body special restrictions have to be taken on consideration regarding Specific Absorption Rate (SAR) and radiation power (less than 1mW or 0dBm) to avoid problems like body tissues damage and cell degeneration while maintaining transmissions in the short range. Besides, given the channel variations in the human body, WBANs would experience different phenomena like multipath, fading and shadowing, then a strong physical layer is mandatory. Different traffics are present in WBANs, emergency traffic, on-demand traffic and normal data traffic only for mentioning the most common types, then WBANs should have a strong structure to support traffic differentiation and prioritization while providing a guarantee and reliable service with the lowest latency close to real-time operation (125ms in medical applications and 250ms in non-medical applications).
IEEE 802.15.6 is a draft standard that defines the physical (PHY) and medium access layers (MAC) for WBAN communications. The standard provides three PHY layers, Ultra Wide Band (UWB), Narrow Band (NB) and Human Body Communications (HBC), whose selection depends on the type of application performed by the WBAN. UWB operates in two frequency bands of 499.2Mhz, one with 3 channels and centered at 3996.3Mhz, and the other one with 8 channels and centered at 7987.2Mhz. NB operates in MICS (Medical Implants Communication Service), WMTS (Wireless Medical Telemetry Services) and ISM (Industrial Scientific and Medical) bands. And HBC operates in two frequency bands centered at 16Mhz and 27Mhz with a bandwidth of 4Mhz. The standard supports three modulations schemes: Gaussian Minimum Shift Keying (GMSK), Differential Binary Phase Shift Keying (DBPSK) and Differential Quadrature Phase Shift Keying (DQPSK). The standard suggests WBANs to be deployed in one-hop or two-hops star topologies using a central node performing as hub for the sensor nodes.
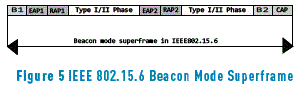
In IEEE 8012.15.6 the central node or hub divides the channel in superframe structures for the medium access and allocation of transmission slots. Each superframe is bounded by beacon slots and is divided in Exclusive Access Phase 1 and 2 (EAP), Random Access Phase 1 and 2 (RAP), Type I/II access phases and a Contention Access Phase (CAP) (see Figure 5). EAP1 and EAP2 access phases are used for emergency traffic, only packets with the highest priority are sent in this phases. RAP1, RAP2 and CAP phases are used for normal or regular traffic. Contention schemes like CSMA/CA and Slotted Aloha are used for medium access in the aforementioned phases. Type I/II phases are used for uplink, downlink and bilink allocation intervals. Type I access is conveyed in terms of frame time duration while Type II is conveyed in terms of frames count. Access mechanism used in TypeI/II phases are polled, unscheduled and improvised.
5.3. Access modes in IEEE 802.15.6
Beacon mode with beacon period superframe boundaries: In this access scheme the superframe is divided into EAP1, RAP1, TypeI/II, EAP2, RAP2, TypeI/II, Beacon 2 and CAP phases. The access in EAP, RAP and CAP phases is done using contention mechanism while in TypeI/II phases access is unscheduled, polled or improvised. The length of each division is managed by the central node depending on the application.
Non-beacon mode with superframe boundaries: Only TypeI/II phases are present in the superframe, the start of the superframe is indicated by a T-Poll timed frame.
Non-beacon mode without superframe boundaries: The access is provided by the central node in unscheduled TypeII polling [52-56].
In [57] an energy efficient scheme is based on two-hops transmissions using IEEE 802.15.6 standard. The main idea behind the strategy is to reduce the duty cycle of relay nodes and then help to reduce energy consumption. Relay nodes consume more energy as they have to transmit their data and other nodes data as well. They have to retransmit the downlink from the central node and the uplink from sensor nodes towards central node as well. To reduce the relay nodes duty cycle the central node is allowed to reach directly every node in the network so the downlink does not have to be relayed by intermediate nodes resulting in the reduction of energy consumption by retransmissions, over-hearing and over-heading at relay nodes. The downlink branch central node-relay node-sensor node is reduced to central node-sensor node while the uplink is kept in its original form. Network lifetime is extended as the relay nodes that were prone to an early exhaustion improve energy consumption by not taking part on the downlink as the standard originally proposes.
Basic cross-layer schemes built upon IEEE 802.15.6 were cited in the taxonomy and classification sections, in [33], an scheme with two phases, a discovery phase for central node broadcasting and a reverse tree calculation phase for nodes to establish the next hop as the node with the least delay for transmissions towards the central node. Three traffic levels are used for traffic differentiation, the highest levels of priority are allowed to access the medium in EAP1 and EAP2 phases, while packets tagged with the lowest level of priority are forwarded in RAP1, RAP2 and CAP phases.
In [38] another IEEE 802.15.6 strategy proposed a cross-layer between SNR at PHY layer and payload length at Application layer, and leveraging the benefits of IEEE 802.15.6 MAC for traffic prioritization purposes. This work showed that a compromise between SNR and payload length achieves energy saving in both coded and uncoded transmissions.
The aforementioned works show that IEEE 802.15.6 offers a wide field for cross-layer proposals. Although the standard specification only refers to PHY and MAC layers there is a myriad of possibilities of energy efficient designs starting out from the different PHY layers and access schemes described in the standard.
5.4. PHY and MAC layers in WBANThe design of new protocols and communication schemes for WBAN has to take into consideration issues regarding the physical and medium access layers in both medical and non-medical applications. The majority of cross-layer schemes reviewed in this paper lack of a clear understanding of the limitations and constraints inherent to these layers in WBAN, mainly induced by mobility, channel variations and medical regulations for communications near the human body.
In [58, 59], the investigators recommend to attend the following issues for adequate PHY and MAC protocols design for WBAN:
Interference: On-body interference within WBAN due to body movements; Off-body interference between nodes from co-existent WBANs and Interference with surrounding wireless technologies.
Tradeoff between data rate and low power: Current cross-layer designs for WBAN are built upon layers that belong to existing wireless technologies such as Bluetooth and Zigbee, these technologies achieve the data rates for WBAN (1Kbit/s to 10Mbit/s) but do not limit the power as the IEEE 802.15.6 suggests, at most 1mW.
Antenna design: Body composition and characteristics affect the impedance of the antennas. The human body experiences an electromagnetic interaction with the antenna. Regarding the antenna design, designers have to consider body shape, electrical characteristics, non-corrosive materials, radiation patterns and whether the antenna is implanted or not.
Aiming to achieve the best performance regarding the tradeoff between energy efficiency and reliability, the designers of MAC protocols for WBAN should take into consideration the mechanisms described in the draft of the IEEE 802.15.6 standard and besides exploit the knowledge of the behavior of the channel. Exploring two parameters, namely, the probability of the channel to stay in good state and the frequency of channel transitions between good state and outage, the designers can devise strategies that can improve the performance without incurring in additional energy consumption. For example, more efficient mechanisms for dynamic allocation of slots instead of statical or random allocations; adaptive scheduling of retransmissions; effective use of relay nodes in transmissions and schemes for an adaptive control of the transmission power.
5.5. Adaptive duty cyclesThe scheduling of active and inactive periods in the medium access control still introduces a significant waste of energy by idle listening and overhearing. Hence a future cross-layer approach should devise a scheme capable of predicting the appropriate length for the wake up and sleep times. Most designs deploy a fixed duty cycle for the sleep frames, and a bad duty cycle choice can result in higher end-to-end latency which could increase dramatically with retransmission which can also result in higher energy consumption to transmit the packets.
5.6. Context aware cross-layerAn open research issue in WBANs is the introduction of context aware protocols at MAC and application layers. The context refers to the environment and the patient conditions where the WBAN is deployed (humidity, environment temperature, luminosity, emotions, mental state, stress levels, age and any other extra-information that could help to better characterize the patients situation). In [60], the authors proposed that context-aware strategies should be implemented over energy-efficient cross-layer approaches between MAC and application layers; they claim that cross-layer in context aware scenarios is needed to address limitations like energy consumption, transmission errors and QoS constraints by an efficient communication of parameters between the MAC layer and the application layer. They also mention that little research has been done regarding this matter.
5.7. QoSUnlike regular WSN, WBAN exhibit specific QoS requirements at every single layer: data reliability, traffic segmentation (regular data or emergency data), data resolution, bandwidth, path latency, routing maintenance, congestion management, path cost, connectivity robustness, communication range, throughput and transmission reliability [61]. To fulfill all QoS requirements mentioned above, a regular stack-layered WBAN should increase processing at all layers, and in some cases, increase the transmit power, thus increasing energy consumption. Thus, a cross-layer scheme could help balance the trade-off between QoS and energy consumption. In almost all of the approaches reviewed, QoS is limited to data-reliability, and in some cases, ignoring that WBAN can manage to provide vital information about a patient's condition. Only in [26], where the bandwidth is proportionally assigned depending on the variable a sensor is monitoring, so an energy-efficient cross-layer approach should offer the possibility to communicate QoS requirements from one layer to another, especially in medical applications (i.e., the application layer should have the possibility to communicate its QoS needs due to, for example, an abrupt change in blood pressure measurements to the MAC layer to report this event immediately to the medical staff).
5.8. SecurityThe transmission of vital signs and private data of a patient require the use of mechanisms for data protection and data confidentiality, thus forcing the use of encryption or coding schemes that require extra data processing and hence more energy consumption, so an efficient cross-layer approach for WBAN should fulfill all security requirements and guarantee that the network lifetime will not be affected as well. It is of note mention that none of the papers reviewed in this survey addresses security issues in cross-layer design or in WBAN data management. In [62], the authors propose a security-aware cross-layer protocol with low impact on power consumption called CICADA-S based on CICADA [28]. The authors propose the management of encrypted keys and authentication codes to prevent security issues like packet sniffing or intrusive nodes joining the network, all of this without affecting the power consumption and throughput of the WBAN.
5.9. Channel modelingAlmost every approach in this survey has been devised under the assumption of an ideal body channel without fading or shadowing effects and the nonstationarity of the channel [41], and as seen in [63-66], on-body channels are hard to characterize, and the best-fit statistical models do not cover all the propagation effects due to diffraction, reflection, fading and absorption of waves in the body channel. We only found a cross-layer scheme taking into account a statistical characterization of body channel: in [67], an energy-efficient topology aware cross-layer is devised using a close approximation to realistic on-body channel but even this approach only considers LOS transmissions.
In [68], an stringent analysis of body channels propagation and channel characterization gives insight of various ''myths'' and misconceptions about proper channel modeling, for example, the use of distance based path loss models with fixed path loss exponents for channel characterization. The use of bad shaped distributions to fit both large scale and small scale statistics from data sets gathered in measuring campaigns of body channels and the typecasting of certain body channels as LOS or NLOS not taking into consideration that in most of the situations the body channels are fluctuating between both propagation modes due to body movements.
6. Conclusion
The goal of this paper is to present a comprehensive survey of the current research (works published in the last decade) in cross-layer design for energy efficiency in the specific context of wireless body area networks. We focus on recording the most relevant studies that try to solve power consumption issues and the extension of the lifetime of WBAN by the development of novel cross-layer approaches. From our point of view, most of the works focus on providing new protocols and abstractions to overcome the performance of the classical communication techniques and models. We observe that in nearly almost all the investigations, the authors are not taking mobility into account, and perhaps most of the results obtained in their simulations and implementations could dramatically change when testing their algorithms and protocols in a mobile scenario; we consider this topic to be widely open for future research and to work on it more thoroughly. We notice that novel cross-layer abstractions aim to replace the traditional stacked model at an early stage because most of the models are based on layer mixtures between adjacent layers or information sharing between pairs of adjacent or non-adjacent layers but still preserving stacked basis. We want to mention that though the existing research on enhancing power consumption in WSN is extensive, most of these approaches were not developed for any specific field (e.g. body applications like WBAN). Hence, there is still an open research issue in adapt results obtained in WSN cross-layer research into WBAN related research. We pretend to show the benefits of cross-layer design in the extension of the WBAN lifetime. Although we do not discuss the methods thoroughly, we present them in a very clear and simple way to inspire future research and novel developments. A major issue faced in the review process of cross-layer approaches is that research in this field lacks a ''benchmark'' for a thorough comparison and evaluation of the benefits and shortcomings of such approaches. Thus the evaluation results are not as objective as they should be. The difficulty in establishing a benchmark lies in the fact that most cross-layer approaches are built and tested under a specific scenario, which in turn, is defined based on the application of interest.
7. Acknowledgements
This work has been partially supported by the CODI sustainability strategy 2014-2015 of the University of Antioquia (Colombia) and the project ''Plataforma tecnológica para los servicios de teleasistencia, emergencias médicas, seguimiento y monitoreo permanente a los pacientes y apoyo a los programas de promoción y prevención'' of the ''Centro de Excelencia ARTICA (Alianza Regional En TICs Aplicadas)'' created by ''Colciencias and Ministerio de las Tecnologías de la Información y las Comunicaciones'' supported by ''Sistema Nacional de Regalías (Colombia)''.
8. References
1. O. Omeni, A. Wai, A. Burdett and C. Toumazou, ''Energy efficient medium access protocol for wireless medical body area sensor networks'', IEEE Trans. Biomed. Circuits and Systems, vol. 2, no. 4, pp. 251-259, 2008. [ Links ]
2. S. Marinkovic, C. Spagnol and E. Popovici, ''Energy-efficient tdma-based mac protocol for wireless body area networks'', in 3rd International Conference on Sensor Technologies and Applications (SENSORCOMM), Athens, Greece, 2009, pp. 604-609. [ Links ]
3. H. Li and J. Tan, ''An ultra-low-power medium access control protocol for body sensor network'', in 27th Annual Conference IEEE Engineering in Medicine and Biology, Shanghai, China, 2005, pp. 2451-2454. [ Links ]
4. B. Otal, L. Alonso and C. Verikoukis, ''Design and analysis of an energy-saving distributed MAC mechanism for wireless body sensor networks'', EURASIP J. Wireless Comm. and Networking, vol. 2010. [ Links ]
5. H. Li and J. Tan, ''Heartbeat-driven medium-access control for body sensor networks'', IEEE Transactions on Information Technology in Biomedicine, vol. 14, no. 1, pp. 44-51, 2010. [ Links ]
6. B. Liu, Z. Yan and C. Wen, ''Ca-mac: A hybrid context-aware mac protocol for wireless body area networks'', in 13th IEEE International Conference on e-Health Networking Applications and Services (Healthcom), Columbia, USA, 2011, pp. 213-216. [ Links ]
7. K. Kwak and S. Ullah, ''A traffic-adaptive mac protocol for wban'', in IEEE Globecom Workshops, Miami, USA, 2010, pp. 1286-1289. [ Links ]
8. Q. Tang, N. Tummala, S. Gupta and L. Schwiebert, ''TARA: thermal-aware routing algorithm for implanted sensor networks'', in 1st IEEE International Conference on Distributed Computing in Sensor Systems (DCOSS), Marina del Rey, USA, 2005, pp. 206-217. [ Links ]
9. A. Bag and M. Bassiouni, ''Energy efficient thermal aware routing algorithms for embedded biomedical sensor networks'', in IEEE International Conference on Mobile Ad Hoc and Sensor Systems, Vancouver, Canada, 2006, pp. 604-609. [ Links ]
10. D. Takahashi, Y. Xiao and F. Hu, ''LTRT: least total-route temperature routing for embedded biomedical sensor networks'', in IEEE Global Telecommunications Conference (GLOBECOM), Washington D.C., USA, 2007, pp. 641-645. [ Links ]
11. R. Kamal, M. Obaidur and C. Hong, ''A lightweight temperature scheduling routing algorithm for an implanted sensor network'', in International Conference on ICT Convergence (ICTC), Seoul, South Korea, 2011, pp. 396-400. [ Links ]
12. M. Kathuria and S. Gambhir, ''Quality of service provisioning transport layer protocol for wban system'', in International Conference on Optimization, Reliabilty, and Information Technology (ICROIT), Faridabad, India, 2014, pp. 222-228. [ Links ]
13. S. Rashid, ''Qos taxonomy towards wireless body area network solutions'', International Journal of Application or Innovation in Engineering & Management, vol. 2, no. 4, pp. 221-234, 2013. [ Links ]
14. Y. Wang, X. Liu and J. Yin, ''Requirements of quality of service in wireless sensor network'', in 5th International Conference on Networking, International Conference on Systems and International Conference on Mobile Communications and Learning Technologies (ICNICONSMCL), Morne, Mauritius, 2006, pp. 116-121. [ Links ]
15. V. Srivastava and M. Motani, ''Cross-layer design: a survey and the road ahead'', IEEE Communications Magazine, vol. 43, no. 12, pp. 112-119, 2005. [ Links ]
16. G. Crosby, T. Ghosh, R. Murimi and C. Chin, ''Wireless body area networks for healthcare: a survey'', IJASUC, vol. 3, no. 3, pp. 1-26, 2012. [ Links ]
17. S. Ullah et al., ''A comprehensive survey of wireless body area networks - on phy, mac, and network layers solutions'', J. Medical Systems, vol. 36, no. 3, pp. 1065-1094, 2012. [ Links ]
18. B. Latré, B. Braem, I. Moerman, C. Blondia and P. Demeester, ''A survey on wireless body area networks'', Wireless Networks, vol. 17, no. 1, pp. 1-18, 2011. [ Links ]
19. D. Arumugam, A. Gautham, G. Narayanaswamy and D. Engels, ''Impacts of RF radiation on the human body in a passive wireless healthcare environment'', in 2nd International Conference on Pervasive Computing Technologies for Healthcare, Tampere, Finland, 2008, pp. 181-182. [ Links ]
20. S. Gopalan and J. Park, ''Energy-efficient mac protocols for wireless body area networks: Survey'', in International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Moscow, Russia, 2010, pp. 739-744. [ Links ]
21. D. Bertsekas, R. Gallager and P. Humblet, Data networks, 2nd ed. New Jersey, USA: Prentice-Hall, 1992. [ Links ]
22. L. van Hoesel, T. Nieberg, J. Wu and P. Havinga, ''Prolonging the lifetime of wireless sensor networks by cross-layer interaction'', IEEE Wireless Communications, vol. 11, no. 6, pp. 78-86, 2004. [ Links ]
23. L. Hughes, X. Wang and T. Chen, ''A review of protocol implementations and energy efficient cross-layer design for wireless body area networks'', Sensors, vol. 12, no. 11, pp. 14730-14773, 2012. [ Links ]
24. S. Raghuwanshi, ''An energy efficient cross layer design scheme for wireless sensor networks'', Ph.D. dissertation, Virginia Polytechnic Institute and State University, Virginia, USA, 2003. [ Links ]
25. M. De Sanctis, E. Cianca, M. Ruggieri and R. Prasad, ''Energy efficient cross layer optimization for WPAN'', in The European Conference on Wireless Technology, Paris, France, 2005, pp. 561-564. [ Links ]
26. T. Jaradat, D. Benhaddou, M. Balakrishnan and A. Fuqaha, ''Energy efficient cross-layer routing protocol in wireless sensor networks based on fuzzy logic'', in 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 2013, pp. 177-182. [ Links ]
27. B. Braem, B. Latre, I. Moerman, C. Blondia and P. Demeester, ''The wireless autonomous spanning tree protocol for multihop wireless body area networks'', in 3rd Annual International Conference on Mobile and Ubiquitous Systems - Workshops, San Jose, USA, 2006, pp. 1-8. [ Links ]
28. B. Latré et al., ''A low-delay protocol for multihop wireless body area networks'', in 4th Annual International Conference on Mobile and Ubiquitous Systems: Networking & Services, MobiQuitous, Philadelphia, USA, 2007, pp. 1-8. [ Links ]
29. N. Torabi and V. Leung, ''Cross-layer design for prompt and reliable transmissions over body area networks'', IEEE J. Biomedical and Health Informatics, vol. 18, no. 4, pp. 1303-1316, 2014. [ Links ]
30. N. Torabi and V. Leung, ''Realization of public m-health service in license-free spectrum'', IEEE J. Biomedical and Health Informatics, vol. 17, no. 1, pp. 19-29, 2013. [ Links ]
31. N. Torabi, C. Kaur and V. Leung, ''Distributed dynamic scheduling for body area networks'', in IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 2012, pp. 3177-3182. [ Links ]
32. Institute of Electrical and Electronics Engineers (IEEE), IEEE standard for local and metropolitan area networks part 15.6: Wireless body area networks, IEEE Standard 802.15.6, 2012. [ Links ]
33. H. Elhadj, S. Boudjit and L. Chaari, ''A cross-layer based data dissemination algorithm for ieee 802.15.6 wbans'', in International Conference on Smart Communications in Network Technologies (SaCoNeT), Paris, France, 2013, pp. 1-6. [ Links ]
34. U. Abassi, A. Awang and N. Hamid, ''A cross-layer opportunistic mac/routing protocol to improve reliability in wban'', in 20th Asia-Pacific Conference on Communication (APCC), Pattaya, Thailand, 2014, pp. 36-41. [ Links ]
35. F. Bouabdallah, N. Bouabdallah and R. Boutaba, ''Cross-layer design for energy conservation in wireless sensor networks'', in IEEE International Conference on Communications, Dresden, Germany, 2009, pp. 1-6. [ Links ]
36. A. Awad, A. Mohamed and A. Sherif, ''Energy efficient cross-layer design for wireless body area monitoring networks in healthcare applications'', in IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), London, UK, 2013, pp. 1484-1489. [ Links ]
37. H. Su and X. Zhang, ''Battery-dynamics driven TDMA MAC protocols for wireless body-area monitoring networks in healthcare applications'', IEEE Journal on Selected Areas in Communications, vol. 27, no. 4, pp. 424-434, 2009. [ Links ]
38. H. Karvonen, J. Iinatti and M. Hämäläinen, ''Energy efficiency optimization for IR-UWB WBAN based on the IEEE 802.15.6 standard'', in 8th International Conference on Body Area Networks, Boston, USA, 2013, pp. 575-580. [ Links ]
39. N. Ababneh, N. Timmons and J. Morrison, ''Cross-layer optimization protocol for guaranteed data streaming over wireless body area networks'', in 8th International Wireless Communications and Mobile Computing Conference (IWCMC), Limassol, Cyprus, 2012, pp. 118-123. [ Links ]
40. M. Nabi, T. Basten, M. Geilen, M. Blagojevic and T. Hendriks, ''A robust protocol stack for multi-hop wireless body area networks with transmit power adaptation'', in 5th International Conference on Body Area Networks, Corfu Island, Greece, 2010, pp. 77-83. [ Links ]
41. V. Chaganti, L. Hanlen and D. Smith, ''Are narrowband wireless on-body networks wide-sense stationary?'', IEEE Transactions on Wireless Communications, vol. 13, no. 5, pp. 2432-2442, 2014. [ Links ]
42. X. Hong, M. Gerla, G. Pei and C. Chiang, ''A group mobility model for ad hoc wireless networks'', in 2nd ACM International Workshop on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Seattle, USA, 1999, pp. 53-60. [ Links ]
43. E. Hyytiä and J. Virtamo, ''Random waypoint mobility model in cellular networks'', Wireless Networks, vol. 13, no. 2, pp. 177-188, 2007. [ Links ]
44. M. Zonoozi and P. Dassanayake, ''User mobility modeling and characterization of mobility patterns'', IEEE Journal on Selected Areas in Communications, vol. 15, no. 7, pp. 1239-1252, 1997. [ Links ]
45. T. Camp, J. Boleng and V. Davies, ''A survey of mobility models for ad hoc network research'', Wireless Communications and Mobile Computing, vol. 2, no. 5, pp. 483-502, 2002. [ Links ]
46. M. Sandhu et al., ''Mobility model for WBANs'', in 9th International Conference on Broadband and Wireless Computing, Communication and Applications (BWCCA), Guangdong, China, 2014, pp. 155-160. [ Links ]
47. H. Ren and M. Meng, ''Understanding the mobility model of wireless sensor networks'', in IEEE International Conference on Information Acquisition, Weihai, China, 2006, pp. 306-310. [ Links ]
48. M. Nabi, M. Geilen and T. Basten, ''MoBAN: A configurable mobility model for wireless body area networks'', in 4th International ICST Conference on Simulation Tools and Techniques, Barcelona, Spain, 2011, pp. 168-177. [ Links ]
49. A. Varga, ''The OMNeT++ discrete event simulation system'', in European Simulation Multiconference (ESM), Prague, Czech Republic, 2001, pp. 65-71. [ Links ]
50. B. Braem, P. Cleyn and C. Blondia, ''Supporting mobility in body sensor networks'', in International Conference on Body Sensor Networks, Singapore, Singapore, 2010, pp. 52-55. [ Links ]
51. B. Braem and C. Blondia, ''Supporting mobility in wireless body area networks: An analysis'', in 18th IEEE Symposium on Communications and Vehicular Technology in the Benelux (SCVT), Ghent, Belgium, 2011, pp. 1-6. [ Links ]
52. K. Kwak, S. Ullah and N. Ullah, ''An overview of IEEE 802.15. 6 standard'', in 3rd International Symposium on Applied Sciences in Biomedical and Communication Technologies (ISABEL), Rome, Italia, 2010, pp. 1-6. [ Links ]
53. H. Bang, K. Takizawa and R. Kohno, ''Trends and standardization of body area network (BAN) for medical healthcare'', in European Conference on Wireless Technology (EuWiT), Amsterdam, Netherlands, 2008, pp. 1-4. [ Links ]
54. N. Bradai, S. Belhaj, L. Chaari and L. Kamoun, ''Study of medium access mechanisms under IEEE 802.15.6 standard'', in 4th Joint IFIP Wireless and Mobile Networking Conference (WMNC), Toulouse, France, 2011, pp. 1-6. [ Links ]
55. N. Timmons and W. Scanlon, ''Improving the ultra-low-power performance of ieee 802.15. 6 by adaptive synchronization'', IET Wireless Sensor Systems, vol. 1, no. 3, pp. 161-170, 2011. [ Links ]
56. K. Hur, W. Sohn, J. Kim and Y. Lee, ''Ieee 802.15.6 wban beaconing for wireless usb protocol adaptation'', International Journal of Software Engineering and Its Applications, vol. 7, no. 4, pp. 1-14, 2013. [ Links ]
57. C. Lin and P. Chuang, ''Energy-efficient two-hop extension protocol for wireless body area networks'', IET Wireless Sensor Systems, vol. 3, no. 1, pp. 37-56, 2013. [ Links ]
58. S. Movassaghi, M. Abolhasan, J. Lipman, D. Smith and A. Jamalipour, ''Wireless body area networks: a survey'', IEEE Communications Surveys and Tutorials, vol. 16, no. 3, pp. 1658-1686, 2014. [ Links ]
59. A. Boulis, D. Smith, D. Miniutti, L. Libman and Y. Tselishchev, ''Challenges in body area networks for healthcare: the mac'', IEEE Communications Magazine, vol. 50, no. 5, pp. 100-106, 2012. [ Links ]
60. D. Tobón, T. Falk and M. Maier, ''Context awareness in wbans: a survey on medical and non-medical applications'', IEEE Wireless Communications, vol. 20, no. 4, pp. 30-37,2013. [ Links ]
61. D. Barakah and M. Ammad, ''A survey of challenges and applications of wireless body area network (wban) and role of a virtual doctor server in existing architecture'', in 3rd International Conference on Intelligent Systems, Modelling and Simulation, Kota Kinabalu, Malaysia, 2012, pp. 214-219. [ Links ]
62. D. Singelée et al., ''A secure low-delay protocol for wireless body area networks'', Ad Hoc & Sensor Wireless Networks, vol. 9, pp. 53-72, 2009. [ Links ]
63. A. Fort, C. Desset, P. Doncker, P. Wambacq and L. Van, ''An ultra-wideband body area propagation channel model-from statistics to implementation'', IEEE Transactions on Microwave Theory and Techniques, vol. 54, no. 4, pp. 1820-1826, 2006. [ Links ]
64. Q. Wang, T. Tayamachi, I. Kimura and J. Wang, ''An on-body channel model for uwb body area communications for various postures'', IEEE Transactions on Antennas and Propagation, vol. 57, no. 4, pp. 991-998, 2009. [ Links ]
65. Z. Hu, Y. Nechayev, P. Hall, C. Constantinou and Y. Hao, ''Measurements and statistical analysis of on-body channel fading at 2.45 ghz'', IEEE Antennas and Wireless Propagation Letters, vol. 6, pp. 612-615, 2007. [ Links ]
66. M. Särestöniemi, T. Tuovinen, M. Hämäläinen, K. Yazdandoost and J. Iinatti, ''Channel modeling for UWB WBAN on-off body communication link with finite integration technique'', in 7th International Conference on Body Area Networks, Oslo, Norway, 2012, pp. 235-241. [ Links ]
67. E. Reusens et al., ''Characterization of on-body communication channel and energy efficient topology design for wireless body area networks'', IEEE Transactions on Information Technology in Biomedicine, vol. 13, no. 6, pp. 933-945, 2009. [ Links ]
68. D. Smith, D. Miniutti, T. Lamahewa and L. Hanlen, ''Propagation models for body-area networks: A survey and new outlook'', IEEE Antennas and Propagation Magazine, vol. 55, no. 5, pp. 97-117, 2013. [ Links ]