Introduction
Most critical systems are associated with the management of high-value resources for a company, industry, or state such as human lives, economic resources, or the infrastructure of public or vital services. Advances in computer sciences and communication technologies, based on the use of modeling and simulation (M&S) tools, integrate all available information from heterogeneous systems with the decision-makers' and operators' criteria in real-time using artificial intelligence (IA) techniques. This enables the system to recreate situations and scenarios that are likely to allow understanding the complex nature of many dimensions of reality. Those related to national security as described in [1], which address the need for a coordinated effort between government, industry, and academia to improve M&S technologies, generate increasingly realistic systems. It is then necessary to integrate different techniques of expert systems, using fuzzy logic, decision tree and genetic algorithm based on the digital characterization of entities, to recreate a real situation in real-time.
A combination of different communication protocols such as UDP, TCP, MQTT, distributed servers, and interaction between fuzzy technologies and decision trees were used for achieving the computer performance to recreate a complex DM scenario. This recreates a critical infrastructure with different assets in extreme conditions to evaluate a decision-maker role and preexisting plans. Indeed, using this software it is possible to evaluate how factors such as time, individuals and pressure affect the decision-making (DM) process and the effective training of decision-makers.
This paper is organized as follows: Section I presents the state of the art for this kind of system; Section II introduces the architecture of simulation systems and the method used for implementing the decision-making process in automatic entity development; Section III addresses the proposed architecture and case simulation results; and finally, Section IV closes with concluding remarks.
State of the art
Models and simulation of Critical Infrastructure and Key Resources (CIKR) are typically used for studying, understanding, and analyzing problems in critical systems, without the need to use resources aimed at controlling critical variables. One of the aspects that could not be recreated is the human factor because there are many possible variations for each situation integrated with the intrinsic complexity of CIKR. To reduce human errors and uncertainty, it is necessary to recreate situations, assets, time, and abnormal factors that could affect the decision-making process. In [2], a situation awareness (SA) is recreated to support the decision-making process and reduce errors using an abnormal situation modeling (ASM) method based on Bayesian networks and fuzzy logic systems. Also, the AI method is commonly used in this kind of simulation not only for recreating uncertainty but also for identifying patterns that could activate an autonomous response from a system using real or simulated inputs [3] in which a cognitive architecture system is present. This system uses an AI-based decision support model (AIDSM) embedded into an autonomous non-deterministic safety-critical system inside a simulation with an unmanned surface vehicle (USV) behavior.
Based on simulation and models, it is possible to recreate a negative situation for the system and to achieve a greater understanding of its interdependencies, vulnerabilities, response time and the impact of damage regarding any abnormal situation, or to evaluate decision-makers' SA. Then, the system could develop contingency plans for possible and predictable situations as described in [1] and [4]. There is also information that can serve as a baseline for model development that allows automating CIKR simulations for all types of applications, especially related to security, as described in [5] were using simulation could optimize police asset distribution. Another type of critical system is discussed in [6], in which these infrastructures are limited to those related to a nation's prosperity such as the national electricity network, fuel and mining systems, telecommunications, information, transport networks, water systems, banking, and public and private finances, among others that may affect governance. In this case, simulation and game theory could be used to find the vulnerabilities and consequences of an attack in a controlled scenario [7], [8]. Simulation and models can provide insight into the complexity of their behaviors, interactions, and operational characteristics such as maintenance, location, and time of supply chains [9]mission requirements, resource constraints, and aircraft statuses are considered to find an optimal strategy set. Given that the maintenance strategies for each aircraft are finite, fleet CBM can be treated as a combinatorial optimization problem. In this study, the process of making a decision on the CBM of military fleets is analyzed. The fleet CBM problem is treated as a two-stage dynamic decision-making problem. Aircraft are divided into dispatch and standby sets; thus, the problem scale is significantly reduced. A heuristic hybrid game (HHG).
Based on [10]-[14], it can be concluded that simulation systems are also used in training, performance measurement, conceptual design, alternative plan design, impact assessment, response planning, new system analysis, acquisition, conceptualization and evaluation, vulnerability analysis, response time measurement, possible courses of action, cause-effect diagram, economic impact and interdependency determination, the effect on external and prospective variables, among others. Also, M&S systems can contribute to understanding the social effect of the result of the simulation, after its development, such as changes in the social environment related to simulation, as described in [15]. Also, the simulation could recreate the human conflict resolution generated by complex social interaction in the real world [16].
Conflict resolution (or peace education, as it is currently called) in terms of its training processes allows the study of historical conflicts of different dimensions among stakeholders. According to the work carried out in [17], the use of computer games is a tool to improve learning about conflicts in global scenarios. This paper deals with the use of games and decision-making exercises to improve the learning process in these areas, becoming add-able to the training process. On the other hand, [18] provides a historical perspective of simulation and play as a teaching strategy, using simulation and role-playing as an integral part of the training process.
Based on the above, the application of simulation technologies to training processes, as well as their use in improving the performance of staff members involved in decision-making, is widely documented. As to security scenarios, simulation systems are known as Computer-Generated Forces (CGF) or as Semi-Automated Forces (SAF). According to the technology used, they are focused on the development of Military Simulators of Decision-Making (MS-DM), formerly known as war games, that have an important role in decision-making training for personnel related to operations and resource management (i.e. the military of a nation).
Some procedures are also established, and a simulated scenario may be used in different modes and at various levels, including single-dimension capabilities or enabling collective environments as described in [19]. In these architectures, multiple technologies have been used to automate processes and even measure the effect of the amount of information on the development of the exercise through Bayesian networks as described in [20], in which the effect of the uncertainty inherent in the operating situations is integrated into the DM process. The degree of automation in those processes depends on the type of information available or the personalization of the tool as detailed in [21]-[24].
As to security, critical systems can be summarized in terms of command and control systems, air traffic systems, the relationship of command lines and others such as media allocation that could affect national security [23] or national critical infrastructure. An approach for national scale security is described in [25]. Conflict simulation is an area that can be encompassed by M&S technologies potentialized by advances in fuzzy logic and fuzzy genetic systems, combined with a decision tree. One of the advantages of these technologies is that they could be used in real-time applications due to excellent computer performance and computational efficiency to recreate complex situations, simulating uncertainties and being efficient in the decision-making process. This technology is easy to use and adaptable to multiple scenarios. It has the advantage of recreating an operational doctrine for military simulations to find better strategies for any situation according to threats, assets, weather, geography, and other variables.
This kind of AI approach has also been used in logistics [28] to minimize the cost of the logistic cycle, using a metaheuristic procedure based on a modified genetic algorithm (MGA). Moreover, approaches such as Montecarlo tree search (MCTS) and heuristic search [29]-[32] have been considered in simulation games for the discretization of the action option space, which is necessary for acceptable computer efficiency and accuracy. Multi fusion data are included because the system should recreate the data that exist in real scenarios through sensor data simulation. In [33] the effort for improving human-computer interaction through reactive search optimization (RSO) using online machine learning techniques is described.
According to the degree of automation, training, experimentation, acquisition and prospective, some analyses can be performed. The analysis allows multiple possibilities that can be modeled within a simulation system that tries to represent a physical system or a real system. Then, it could be necessary to use methodologies to transform a typical one input-one output fuzzy inference into a hybrid system capable of evaluating the behavior of a physical system described in [34]. Simulation systems should be able to recreate critical scenarios based on the operational needs that may arise from training to the preparation of a large operational device. Systems also work emulating different scenarios or situations such as failure, sabotage, natural disasters, conflicts or threats, type of entity, training, environmental variables, displacement, geography, and geopolitics. The quantitative analyses of results allow to conclude and to make decisions about the time and resources needed to accomplish objectives and mitigate risks.
At the security level, someone could structure different situations and control scales, which can be organizational levels, human behaviors, types of threats, obstacles, response times, economic, geographical, human, political variables, etc. They are used to approach strategies and tactics to mitigate and prevent threats to the established social order or minimize the effects of natural disasters.
Different scenarios within simulation systems have been structured from joint or coalition strategic levels to tactical levels involving each branch and rank in the military hierarchy in accordance with [27], [35]. This article outlines the possibility that a system would allow for the joint or combined synchronization required and bring together different tactical or strategical situations. With the advancement of technology, other types of developments have been integrated into simulation such as intelligent systems and probabilistic systems applied to DM in critical situations. The work of [20] describes the application of automatic reasoning systems based on Bayesian networks as methodologies for evaluating patterns and success situations. In recent years, the application of AI has impacted manifold areas of science and engineering.
This is the reason AI plays a key role in the simulation of critical scenarios and the automatic detection of parameters. An example of this is the application of AI to M&S in highly stressful situations [36]-[38] that, with the support of decision-making systems, improve the reaction capacity to high impact situations. Another case of the use of AI [34] explains the development of different tools to simulate challenging events, having the possibility of interacting with autonomous systems, and testing the skills of personnel through a virtually trained automaton. These systems are "trained" every day with data through neural networks and different mathematical AI models. The possibility of having hybrid systems with AI models diversifies interoperability and application in simulation systems [35], which have some degree of integration with mathematical and probabilistic functions that allow evaluating decision-making.
Some simulation systems are based on High-Level Architectures (HLAs) and Distributed Interactive Simulation (DIS) architectures [39]-[40], linking with web services for interoperability. These use languages based on extended markup (XML) or Military Scenario Definition Language (MSDL) in the military field for data exchange between command and control (C2) and simulations. These systems provide common operational images generating a Battle Management Language (BML) or Coalition BML (C-BML), which allows recreating conflict situations in a distributed manner.
To implement this type of process there are multiple architectures, which depend on the approach in which the analysis is developed. According to [41], the universe of M&S technologies is broad and comes from technologies based on high-level architecture widely used in defense. For [10], [42]-[43], M&S permits and is composed of distributed systems, i.e. simulations in each system can interact with each other, regardless of computer platforms, allowing greater flexibility. Still, the standard has become little compatible with new technologies, as new distributions have changed the concept of vertical to horizontal architecture, focusing on technologies such as microservices and integrating different frameworks that shorten the time of assembly and production of new environments. Microservices and distributed architectures are growing for important large companies in the technology sector while providing a road-map for the ICT sector. Together with AI [36], [37], [44], they are offering great advances to make simulations increasingly real and faster in simulation environments [45].
Some of the simulation systems that have been analyzed for this work are, for example, Joint Semi-Automated Forces (JSAF), Joint Conflict and Tactical Simulation (JCATS), VR-Force, Aerial Warfare Simulation (AWSIM), Research, Evaluation and Systems Analysis (RESA), corps frame simulation model for officer training (GUPPIS/KORA OA), Joint Theater Level Simulation (JTLS), Sword Mass, among others. These types of systems are widely used both in the military and civilian field for training critical decision-makers involving heterogeneous and media resources from different entities; however, their licensing and maintenance costs are high and they generate great technological dependence.
System implementation method
DM in an exercise is defined in terms of interest, that is, which is considered the best option to meet a goal using different technologies or methods (DM process). In simulating a DM scenario, each trajectory would be optimized in terms of minimizing or maximizing a certain factor and bounded by the restrictions and specific state of variables and inputs. This approach applies to any area as described in [46] in which an optimal DM process is sought at the strategical level.
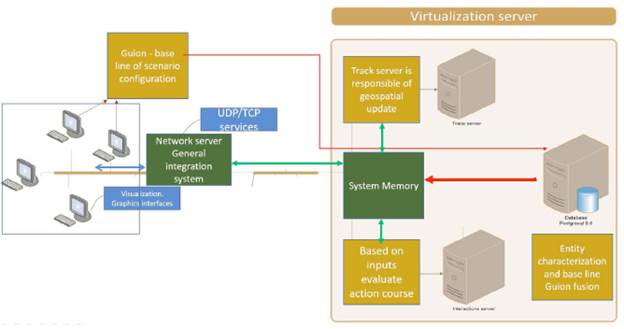
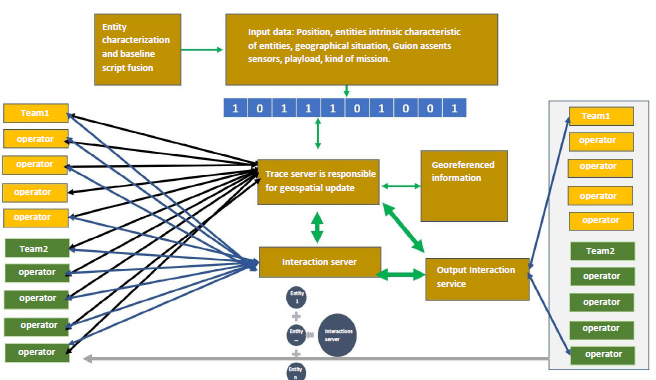
M&S using fuzzy logic variation is applied to manage high volumes of information in real-time allows the communication of various parameters with other systems and simulation subsystems, synchronizes data even with variable temporalities, and executes a procedure according to the state of the variables at the time. Fig. 1 describes the most important subsystems in the architecture proposal of these documents. Fig. 2 depicts the interaction between the main subitem and operators for each period.
In this simulation project, several variations could come from the database that has stored all entities with physical attributes. To create a scenario, it is necessary to make a step-tracking based script, a structure that using database information can create a scenario according to the situation. With this information, the system creates a vector that describes all characteristics that should be evaluated for other dependencies of the system and that could be shared with other system instances. Through communication protocols in a specific simulation, entities are modeled inside the memory, where interaction and trace server recreate a specific condition such as speed, position, restrictions. With all this information, each user will have a graphic scenario representation in a graphic interface.
Using the fuzzy logic hybrid method with varying levels of precedence in the relation among operators, trace server and interaction server, the system output could be the result of the interaction between two entities. This situation is evaluated by each entity in each period creating a Fuzzy Tree simultaneous evaluation process as described in [47] in which multiple cascading fuzzy systems are optimized by genetic methods. In this problem a team of UCAV's must traverse through a battle space and counter enemy threats, utilize imperfect systems, cope with uncertainty, and successfully destroy critical targets. Enemy threats take the form of Air Interceptors (AIs. The fuzzy tree is shaped by all data that should be considered at each stage in each scenario. This information has internal entity data such as speed, kind of entity, fuel, mission, state, and external entity data such as geographic location compared with other entities, operators, weather, resources, threats, among others. The value of each parameter could be defined by a deterministic equation system such as movement or a probabilistic equation system such as weather or even random.
The system classifies inputs and outputs using a physical equation in case of a physical model that could describe the behavior of entities such as movement, weights defined by entities, or probabilistic factors according to the actual characteristics of entities. This creates a unique output in combination with rules, allowing each period to give a weight to each sub-decision and reducing the number of operations to be classified.
Consequently, the system stores a lot of information to semi-automate the behavior of different entities. This large amount of stored data is commonly referred to as Big Data [37]. AI techniques are used again to effectively manage these volumes of information [36]. However, the methods or models (MOS) used in data science and business intelligence for AI processes enable the system to perform emulated processes, generate automation, and recreate entities that are combined to represent the results through forecasts that provide training benefits to users employing dashboards. This process will help to understand the dimension of the problem and to influence decision-making [48], [49].
In other words, when the simulation finishes, all the data generated is processed in an organized and efficient manner to issue rules, restrictions, destroyed objectives, and operator interactions. This kind of information aims at generating a feedback line among abnormal or risk situations, training, and the possibility of changing the scenario conditions without real effects. This produces highly dynamic changes in plans and strategies that reduce indetermination levels, especially in military scenarios.
Implementing real-time strategy games requires many skills to propose and carry out operational strategies such as tactics. This kind of simulation ranges from the construction of effective economies applied to the mission to the decision of how to build and distribute the resources resulting from exploration. This becomes a recurrent system that looks for needs and restrictions of concern.
For achieving a high-level planning capability and possibilities of rule-based human control, it was necessary to create a system restriction that controls behavior or entities using a hybrid fuzzy logic tree model so that in a complex situation operator interaction could recreate order missions and a random situation. It is possible to generate a smart report based on feedback that could be used by senior corporate decision-makers to improve action plans.
Proposed architecture
After analyzing the state of the art and the architectures used for simulation and evaluating some globally recognized systems, we proceeded to design the system, supported by the detected capacities and the described theory of these systems. Based on the bibliography on available simulation, interviews were conducted with expert personnel in the management of and response to critical situations to establish operational requirements that are appropriate to the needs. As a result, a system has been designed based on a high-level hybrid architecture that allows the integration of technologies such as Micro Services; MQTT, which is machine-to-machine (M2M) interface technology typically used as a connectivity protocol of mobile devices; and user datagram protocol (UDP). With this protocol, a new hybrid architecture was defined in which in a single system, some heterogeneous microservices, for example, could use different communication protocols according to their function and number of connections. With this structure, even real data from an external sensor could be integrated. This system intends to simulate critical scenarios to take timely action in situations in which human lives and critical assets are involved and to assess the procedures and effectiveness of process managers.
For this, and having as a requirement that the simulation system can be used in multiple situations, such as military training, reaction to natural disasters, response times, among others, modular architecture based on subsystems is proposed. This would allow vertical and horizontal growth of the project in the future. As a basis, the designed system has four main subsystems and a general integration system, which allows interconnection and asynchronously integrates data from other subsystems to simulate real scenarios and to make decisions as shown in Fig. 1.
Database
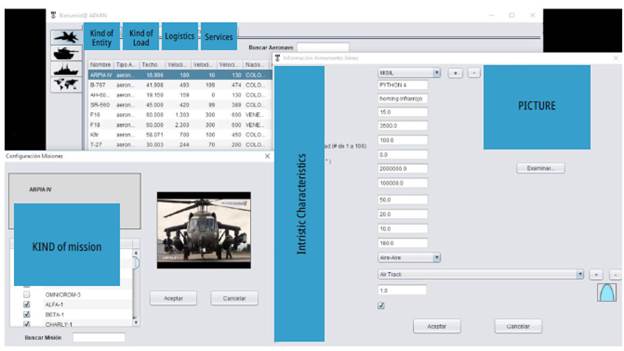
In a simulation system, success in the characterization of entities depends largely on data available to create them virtually and model them in a precise way, i.e. they emulate the behavior of the real entity. For this purpose, tables were implemented to describe the kinetic behavior of any entity. Characteristics such as horizontal speed, vertical speed, size, displacement, lifetime, transport capacity, and type of entity were defined. Later, a PostgreSQL database was defined in which all the records used by the simulation system are stored. This information was indexed, and the database keeps the data stored to allows a quick and organized search.
As shown in Figure 3, a data entry form was set to create and select any available entity.
Interaction server
Each entity described should be uploaded into the system at the time of the simulation and contain enough information to emulate their behavior independently. However, in the system, there are interactions among entities, for example, an avalanche over a vehicle or a town, two planes in one operation, terrestrial units fighting against each other or any possible relation thereof, as shown in Fig. 2.
To guarantee a simulation according to its planning, certain restrictions or conditions are set up for the system to adjust the behavior of entities or even to simulate the destruction of an entity by the effect of another. This results in a relationship or interaction if the conditions given by the system are met.
The server is responsible for modeling all the mathematical and physical equations that govern the different behaviors that are recorded during the simulation among entities. This application is developed in JAVA as a programming language and the address of integrated services is configured. The structure of the system is shown in Fig. 4.
Its main functions are to calculate and eliminate objects and events due to loss, catastrophe, or any other circumstance and to store scenarios based on different situations.
Visualizer
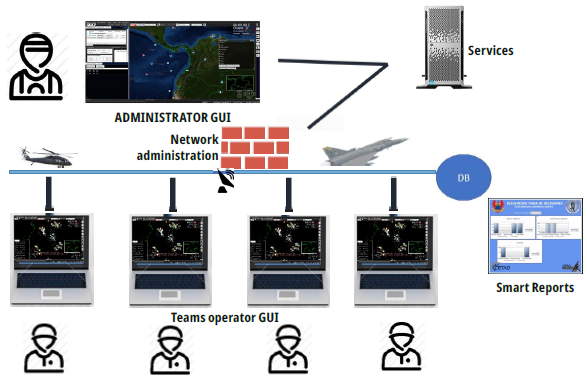
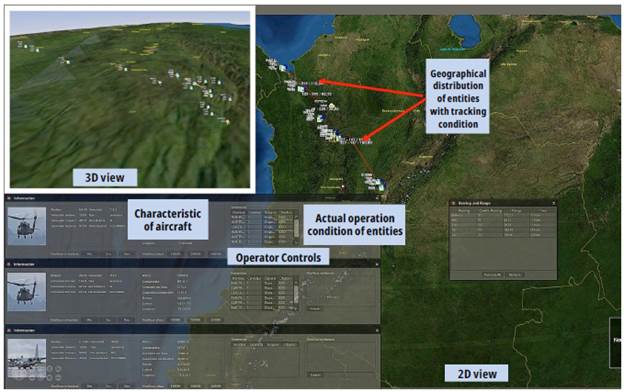
As shown in Fig. 5, this system is responsible for the human-machine interface that governs the interaction of simulation users and other subsystems, i.e. it allows the interaction of the end-user with the system. In this interface, simulation exercises are performed.
It is C#-based as to programming language and its main functions are to enable simultaneous interaction of groups of operators during the simulation and to show the scenario to operators and decision-makers, graphically displaying entities, devices and action mechanisms such as aircraft, sensors, and vehicles.
Trace server
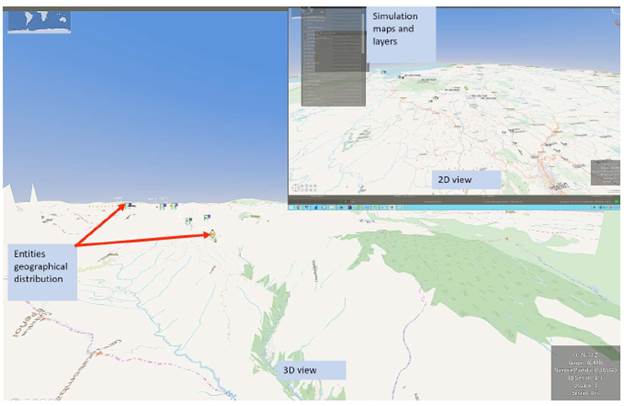
Just as the interaction server is responsible for defining the relationships among entities, the trace server is responsible for projecting the position of entities on the map in 2- or 3-dimensions using units of measurement such as nautical miles or kilometers.
As the system can be 2- or 3-dimensional, flat projections of entity positioning are used applying the Mahala Nobis formula integrated with different simulated inputs over the same plane as described in [3], [50], [51]. In other words, this subsystem is responsible for moving all relevant elements during the simulation. It is designed to contain all the characteristics of each device or mechanism involved in the game and simulate their physical characteristics in a real way. All these elements are taken from the database and other servers and are uploaded into the server's memory for effective behavior. Te trace server is developed in C# and its functions are calculating the cost of fuel, trajectory, heights, speed control, real-time, playtime, among other parameters.
Fig. 1 shows a high-level diagram of the system architecture in which each subsystem is part of the proposed architecture for the developed simulator. Each stage operates asynchronously at a low level; however, thanks to the development of an integration framework, each of the subsystems is integrated and synchronized at a high level. This allows real-time results and configuring each scenario based on their characteristics.
Simulation case
To evaluate performance, a simulation was created with a hypothetical situation of a dam failure. This allowed testing and adapting the system to a situation by recreating and modeling the behavior of entities. In this case, the geographical and political context of the Hidroituango project and the participation of the Air Force in disaster response are pretended. This Project is located on the Cauca River between the municipality of Ituango and the district of Puerto Valdivia. For the simulation, the main characteristics of the dam are as follows:
■ Dam height: 560 meters
■ Capacity: 2.72 billion m3 water
■ Flooded area: 3,800 hectares
■ Dam length: 79 kilometers
■ Average flow of the river: 1010 m3/sec
■ Dam volume: 19 million m3
Tese data are integrated into an entity that represents the collapse and calculates displacement along the riverbank.
Fig. 5 and Fig. 6 show the situational location; the measured distance from a military unit used in the simulation was 115 km. Tis would be the distance that an aircraft would have to travel to provide support. In this case, a SikorskyUH-60 Black Hawk helicopter was simulated and characterized. For these simulations, populations at risk and percentages were taken from [52]. Similarly, the calculations published by the Municipal Risk Management Committee of Taraza [53] and other media were taken to estimate the simulation of the dam flow, which varies by municipality and distance from 263,000 m3/s on stage one to 16000 m3/s on stage two. Te displacement vector that provides the upper and lower elevation of an aircraft based on reaction and support time of different municipalities and warning points is calculated at an intermediate value of 1,010 m3/h. Fig. 6 shows a 3D view of the system and complexities of the operational area.
The simulator integrates real variables little known by risk management personnel such as aircraft autonomy, fuel, operating ceilings, meteorological conditions, recovery bases, among others. This allows executing various interactions in the simulation to find ideal points of refueling, optimal base, operations control, number of aircraft for emergency support, time, etc. Several simulations were run to establish the best conditions by measuring the distances between populations and the military unit where helicopters are located, travel time, flight time of the helicopter, number of units required for support and how much personnel can be transported.
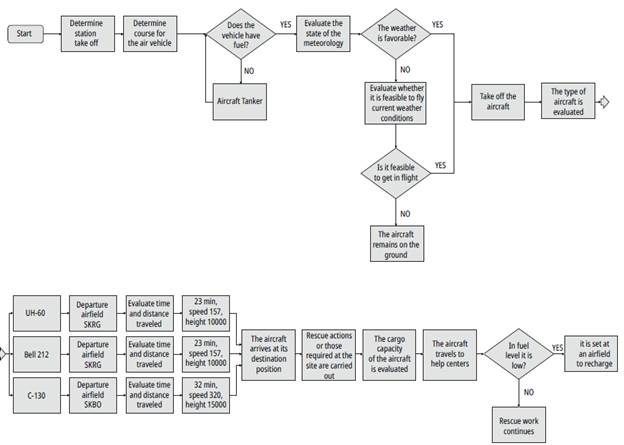
Each of the simulated scenarios should be reproduced as many times as there are variables to measure. For this, the system has an automatic reproduction and evaluation function. An example of a decision-making process is shown in Fig. 7 based on the Hidroituango simulation, which describes the action to be taken by the person in charge of the operation. The results of this simulation are shown in Table 1 with times, helicopters, and distance. Using this result, it is possible to propose an emergency plan reconfiguration and recommend the location of the aircraft at the nearest recovery points, hospitals, trails and other information that would suggest improvements in the distribution of means and calculating times of response and arrival to the place of events.
From Table 1 it can be concluded, for example, that the Hidroituango simulation was successfully reproduced. The system designed provides valuable tools for the scenarios as demonstrated in the example, which can determine that the best location for a helicopter in terms of time and distance is Frontino, followed by Rionegro, with closer third-level hospitals in Montería and Medellín.
Table 1 Hidroituango simulation results based on different assets location and recovery área
| Hidroituango Situation Simulation | |||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Initial Pos | Target | Type of aircraft | Displacement Time / Min | Speed (Knots) | Altitude (Feet) | Sustaining Time | Distance NM | Min | Fuel lb | Hospital location | Spend T. | Hospital location | Spend T. | Autonomy | Total Time to RNG | Total Time to Med | Fuel | Base | Flight Time | Weather | Height |
| Rionegro | Hidroituango | uh-60 | 23 | 157 | 10000 | 10 | 59,72 | 33 | 2878 | RNG | 23 | MED | 24 | 2,5 | 56 | 57 | 2049,2 | SKLC Dabeiba -30 -40 mts | 77 | sky clear | Visual |
| Medellín | Hidroituango | uh-60 | 24 | 137 | 10000 | 10 | 54,12 | 34 | 2943 | RNG | 23 | MED | 24 | 2,5 | 57 | 58 | 2027,4 | SKMD Medellín- 30 -40 mts | 83 | sky clear | Visual |
| Carepa | Hidroituango | uh-60 | 29 | 157 | 15000 | 10 | 74,09 | 39 | 2910,3 | RNG | 23 | MED | 24 | 2,5 | 62 | 63 | 1918,4 | SKLC Dabeiba -30 -40 mts | 73 | sky clear | Visual |
| Yarumal | Hidroituango | uh-60 | 35 | 131 | 10000 | 10 | 124,92 | 45 | 2648,7 | RNG | 23 | MED | 24 | 2,5 | 68 | 69 | 17987,6 | SKMD Rionegro- 30 -40 mts | 78 | sky clear | Visual |
| Frontino | Hidroituango | uh-60 | 12 | 152 | 10000 | 10 | 36,45 | 22 | 2943 | RNG | 23 | MED | 24 | 2,5 | 45 | 46 | 2289 | SKLC Rionegro -30 -40 mts | 55 | sky clear | Visual |
| Rionegro | Hidroituango | Bell 212 | 23 | 157 | 10000 | 10 | 59,72 | 33 | 1095,16 | RNG | 23 | MED | 24 | 2 | 56 | 57 | 756,525 | SKMD Medellín- 30 -40 mts | 77 | sky clear | Visual |
| Medellín | Hidroituango | Bell 212 | 24 | 137 | 10000 | 10 | 54,12 | 34 | 1224,85 | RNG | 23 | MED | 24 | 2 | 57 | 58 | 756,525 | SKMD Medellín- 30 -40 mts | 83 | sky clear | Visual |
| Carepa | Hidroituango | Bell 212 | 29 | 157 | 15000 | 10 | 74,09 | 39 | 1109,57 | RNG | 23 | MED | 24 | 2 | 62 | 63 | 696,48 | SKLC Rionegro -30 -40 mts | 72 | sky clear | Visual |
| Yarumal | Hidroituango | Bell 212 | 35 | 131 | 10000 | 10 | 124,92 | 45 | 893,42 | RNG | 23 | MED | 24 | 2 | 68 | 69 | 624,43 | SKMD Medellín- 30 -40 mts | 83 | sky clear | Visual |
| Frontino | Hidroituango | Bell 212 | 12 | 152 | 10000 | 10 | 36,45 | 22 | 1224,85 | RNG | 23 | MED | 24 | 2 | 45 | 46 | 900,625 | SKLC Rionegro -30 -40 mts | 55 | sky clear | Visual |
| Bogotá | Hidroituango | uh-60 | 72 | 157 | 10000 | 10 | 169,93 | 82 | 1080,75 | RNG | 23 | MED | 24 | 2,5 | 105 | 106 | 480,75 | SKMD Medellín- 30 -40 mts | 120 | sky clear | Visual |
| Bogotá | Hidroituango | c-130 | 32 | 320 | 15000 | 10 | 169,93 | 42 | 55800 | RNG | 9 | MED | 11 | 6 | 51 | 53 | 51500 | SKLC Rionegro -30 -40 mts | 61 | sky clear | Visual |
Source: The authors.
Besides, the system through its results allows defining aims objectively and evaluates the performance of the person in charge of the operation to demonstrate waiting times, delays, and even random factors such as meteorology and maintenance during the situation.
However, the operational processes carried out in the simulation, allowed to obtain times of the situation used, possible contingencies, resources involved, air interactions, risk management and any other element that is modeled to obtain approximate results to reality, achieving simulations by computer without risking resources.
Conclusion
Modeling and simulation technologies are valuable tools for training people involved in the decision-making process in critical environments, as they allow recreating an environment that can be unexpected and only occur in real emergencies.
Moreover, thanks to simulation technologies, system variables that cannot be physically emulated can be developed to further detail the behavior of entities concerning failures, contingencies, sudden changes, and even situations outside the system as environmental variables. This kind of factor is supremely valuable in the process of training leaders and decision-makers at the management, administrative, operational, or strategic levels in civil and security operations.
Different architectures have been tested in the development of specific simulation contexts, such as war games, role analysis or infrastructure simulation. But it is possible to integrate different systems and subsystems thanks to time-oriented microservices and communication and control protocols to obtain a technology capable of being applied to multiple situations.
It is possible to automate decision-making processes using restriction and rules applied to a hybrid fuzzy tree. The combination of a fuzzy logic tree and a genetic algorithm enables system flexibility and performance to recreate complex realtime scenarios.
The integration achieved on the behavior of each entity is based on AI techniques for the recognition of situational parameters and human behavior. The system can simulate it involving different entities while recreating the conditions for the decision-maker to evaluate the result of the application criteria in a controlled space. With the interaction of these technologies and a decoupled service-oriented system, vertically and horizontally scalable, it is possible to develop different additional tools that are easily integrated into more services or servers that coexist and work in a synchronized manner.
Lastly, the application of business intelligence techniques and scorecards to evaluate responsibilities, causes, and effects is useful to improve procedures and train decision-makers.