Services on Demand
Journal
Article
Indicators
-
 Cited by SciELO
Cited by SciELO -
 Access statistics
Access statistics
Related links
-
 Cited by Google
Cited by Google -
 Similars in
SciELO
Similars in
SciELO -
 Similars in Google
Similars in Google
Share
Ingeniería y Ciencia
Print version ISSN 1794-9165
ing.cienc. vol.7 no.13 Medellín Jan./June 2011
A combined pool/bilateral dispatch model for electricity markets with security constraints
Um modelo combinado de despacho pool/bilateral para mercados eléetricos com restricões de segurança
Un modelo combinado de despacho pool/bilateral para mercados eléctricos con restricciones de seguridad
Jesús María López-Lezama1, Mauricio Granada-Echeverri2 y Luis A. Gallego-Pareja3
1 Magíster en Ingeniería eléctrica, jesusmarialopezl@yahoo.com, profesor, Universidad de Antioquia, Medellín-Colombia.
2 Magíster en Ingeniería eléctrica, magra@utp.edu.co, profesor, Universidad Tecnológica de Pereira, Pereira-Colombia.
3 Doctor en Ingeniería eléctrica, gallegopareja@gmail.com, estudiante de post-doctorado,
UNESP-Ilna Solteira, São Paulo-Brasil.
(Recepción: 08-mar-2010. Modificación: 24-sep-2010. Aceptación: 1-oct-2010)
Se aceptan comentarios y/o discusiones al artículo
Abstract
The secure operation of the electric power system is a challenging task for the system operator which is responsible of its coordination, control and monitoring. In most power systems security is typically handled on a multi-state approach. In which case, security criteria are incorporated by means of additional constraints, modifying the initial dispatch calculation. In this paper a generation dispatch model for competitive energy markets considering security constraints is presented. The proposed approach combines the generation dispatch related to pool and bilateral markets with coupled post-contingency optimal power flows into a single optimal dispatch model, avoiding economic inefficiencies that appear in conventional multi-stage dispatch approaches. The proposed model is linear, and as such, it is based on a DC model of the network. A 6-bus didactic system and the IEEE RTS-24 bus test system are used in order to show the operation and effectiveness of the proposed approach and to compare it with the basic pool/bilateral dispatch with no security constraints. Results show that the inclusion of security constraints lead to a higher dispatch cost. Furthermore, it was found that the enforcement of firmed bilateral contracts might lead to system congestion.
Key words: optimal dispatch, bilateral contracts, energy markets.
Resumo
A operação segura do sistema de potência constitui uma questão difícil para o operador do sistema, o qual é responsável pela coordenação, controle e monitoramento deste. Na maioria dos sistemas de potência a segurança é manejada mediante uma metodologia multi-etapa. Neste caso, os critérios de seguridade são incorporados mediante restrições adicionais as quais mudam o cálculo do despacho inicial. Neste artigo é apresentado um modelo de despacho de geração para mercados elétricos competitivos considerando restrições de segurança. A metodologia proposta combina o despacho de geração de mercados tipo pool e contratos bilaterais com fluxos de potência ótimos post-contingência, acoplados em um modelo de despacho só, o qual evita ine-ficiências econômicas que aparecem nos despachos convencionais multi-etapa. O modelo proposto é linear, e como tal, é baseado no modelo de rede DC. Um sistema didático de 6 barras e o sistema IEEE RTS-24 são utilizados para ilustrar a operação e efetividade da metodologia proposta e comparar com o despacho pool/bilateral básico, sem restrições de segurança. Os resultados mostram que a inclusão de restrições de segurança leva a um despacho mais caro. Além disso, encontrou-se que a aplicação de contratos bilaterais pode levar a problemas de congestionamento no sistema.
Palavras chaves: despacho ótimo, contratos bilaterais, mercados de energia.
Resumen
La operación segura del sistema de potencia es una tarea difícil para el operador del sistema, el cual es responsable por la coordinación, control y monitoreo de éste. En la mayoría de los sistemas de potencia, la seguridad es manejada mediante una metodología multi-etapa. En este caso, los criterios de seguridad son incorporados mediante restricciones adicionales que modifican el cálculo de despacho inicial. En este artículo se presenta un modelo de despacho de generación para mercados eléctricos competitivos considerando restricciones de seguridad. La metodología propuesta combina el despacho de generación de mercados pool y contratos bilaterales con flujos de potencia óptimos post- contingencia acoplados en un solo modelo de despacho, lo cual evita ineficiencias económicas que aparecen en los despachos convencionales multi-etapa. modelo propuesto es lineal, y como tal, se basa en el modelo DC de la red. Un sistema didáctico de seis barras y el sistema IEEE RTS-24 son utilizados para ilustrar la operación y efectividad de la metodología propuesta y para compararlo con el despacho pool/bilateral básico sin restricciones de seguridad. Los resultados muestran que la inclusión de restricciones de seguridad lleva a un despacho más costoso. Por otra parte, se encontró que la ejecución de contratos bilaterales firmes puede llevar a problemas de congestión en el sistema.
Palabras claves: despacho óptimo, contratos bilaterales, mercados de energía.
1 Nomenclature
The following nomenclature is used throughout the paper.
Indices and sets
i: Generator index.
j: Fictitious generator index.
n, m: Node indexes.
lmn: Index of line connecting nodes m, n.
k: Contingency index.
L: Set of lines.
N : Set of nodes.
N g: Set of generators.
N f g: Set of fictitious generators representing load shedding.
N d: Set of loads.
Parameters
a: Quadratic coefficient of the bid cost curve ($/M W2 h).
b: Linear coefficient of the bid cost curve ($/MWh).
c: Independent term of the bid cost curve ($/h).
Ci(P gi): Bid cost curve of generator i.
Cj(P f gj): Bid cost curve of fictitious generator j.
GD: Matrix of bilateral contracts (MW).
Pd: Vector of active power demands (MW).
Rk: Probability of the system to operate under contingency k (%).
∆i: Ramp limit of generator i (MW/h).
P gjMin:Minimum active power limit of generator i (MW).
P f gjMin: Minimum active power limit of fictitious generator j (MW).
P giMax: Maximum active power limit of generator i (MW).
P f gjMax: Maximum active power limit of fictitious generator j (MW).
xmn: Reactance of line connecting nodes m, n (Ohms).
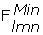 : Minimum power flow in line connecting nodes m, n (MW).
: Minimum power flow in line connecting nodes m, n (MW).
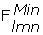 : Maximum power flow in line connecting nodes m, n (MW).
: Maximum power flow in line connecting nodes m, n (MW).
Variables
θn: Angle of node n (radians).
Pg: Vector of power generation (MW).
Flmn: Power flow in line lmn (MW).
2 Introduction
The dispatch problem arises from the moment in which two or more generators must supply several loads, forcing the system operator to optimally distribute the loads among these generators. Historically, the first optimization efforts were performed over generation control, what is known nowadays as classic economic dispatch [1]. Greater capacity of computer processing along with new techniques for efficient treatment of sparse matrixes have allowed the solution of problems that include network constraints and reliability criteria. This evolution has led to what nowadays is known as Optimal Power Flow (OPF) [2]. In the last decade the energy sector has undergone fundamental changes. Most of these changes are related to the new trend of unbundling operation of electrical power systems which aims to increase competition and reduce regulation. Under these challenging tasks, the study of economic models and their adaptation to new regulatory frameworks has been of great interest in recent years [3]-[4].
There are several studies that approach the optimal dispatch on an OPF basis. Reference [5] presents a generation scheduling model considering security constraints. Such model is adapted to the Spanish electricity market rules in which the pool-based daily market and the technical constraints are solved in a two-stage basis. That is, after the market clearing procedure has been performed, a second optimization process is carried out redispatching previously matched energy to account for network constraints. Reference [6] presents an AC dispatch using a security-constraint unit commitment model. The proposed solution for the hourly scheduling of generation units is found using Benders decomposition. References [7] and [8] incorporate wind power in the classical dispatch and unit commitment problem. In [9] the dispatch problem is solved using a particle swarm optimization technique, in [10] the dispatch problem is approach through a combination of genetic algorithms, sequential quadratic programming and the maximum entropy principle. Reference [11] presents a comparative study of heuristic techniques applied to the load dispatch problem. In this paper we propose a combined pool-bilateral dispatch model considering contingency constraints. The main purpose of this paper is to show the impact of firm bilateral contracts in a security- constrained dispatch. Integer variables regarding the unit commitment of generating units are not considered. Furthermore, a DC model of the network has been used, therefore, the proposed pool/bilateral dispatch model can be solved using conventional linear programming. A bilateral contract is a privately negotiated instrument that establishes a price and quantity traded between the generation and demand side of the market without intervention of the system operator [12]. Bilateral contracts offer financial stability to generators and lower prices to consumers when compared with the more volatile pool market prices. In the pool model, suppliers and consumers submit their bids in a power auction coordinated by the pool. The pool market is cleared by the system operator, which calculates the market clearing prices through an optimization procedure. In most cases, security constraints are included in a different market stage, introducing corrections to the previous dispatch [5]. The introduction of corrections in a later stage leads to economic inefficiencies in the dispatch calculation. In this case, we use the term economic inefficiency referring to the attainment of suboptimal solutions. This is supported by the fact that an optimal mathematical solution of a contingency-constrained dispatch is not guaranteed under a multiple-stage process [13]. To avoid such economic inefficiencies, the dispatch with the security constraints must be solved in a single-step procedure. A first attempt to introduce security constraints in a pool/bilateral dispatch model is presented in [14]. The philosophy of the methodology presented in [14] is based on the consideration of feasibility after single contingencies developed by Stott and Alsac in 1974 [15]. The main disadvantage of this methodology is that it is based on an iterative procedure, and thus, as it was already stated, such procedure does not guarantee the achievement of an optimal mathematical solution. To obtain an optimal solution it is necessary to consider all contingencies simultaneously; this is possible using coupled post-contingency power flows in the problem formulation. This approach was first proposed in the literature in [16] in a general context of locational based pricing and reserve markets. Some applications of this approach have been implemented in the context of optimal power flow [17] and energy reserve markets [18].
3 Dispatch in pool and bilateral markets
Under a deregulated market environment, suppliers and consumers are allowed to trade in pool and bilateral markets. In this context, the vectors of active power generation and demand are partitioned to represent pool and bilateral components as shown in (1) and (2).
Pg = Pgp + Pgb
Pd= Pdp + Pdb,
whereganddstand for generation and demand, respectively; and the upper scriptspandbstand for pool and bilateral, respectively. According to the notation developed in [19], GD represents a square matrix of bilateral contracts. Where each element GD (i, j) represents the energy traded between the generator located at bus i, and the load located at bus j. Using this matrix and a column vector of onese, the bilateral component of the active power and demand vectors presented in (1) and (2) can be rewritten as in (3) and (4).
Pgb = GD.e
Pdb = GDT.e.
In this model bilateral contracts are assumed to be firm, which means that accounting for losses and congestion is responsibility of the pool. The combined pool/bilateral dispatch approach was proposed in a series of papers [20], [21] and [22]. The basic problem involving inelastic demand and firm bilateral contracts is presented as a minimization problem given by (5)-(11).
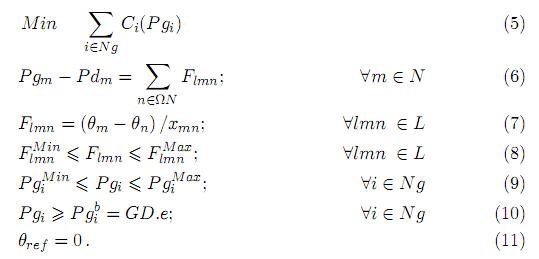
The objective function, given by (5), is to minimize the total generation cost, taking into account the active power balance constraints given by (6); the transmission limits given by (7) and (8); the generation limits given by (9); and the set of firm bilateral contracts given by (10). These additional inequality constraints establish minimum generation levels dictated by the bilateral contracts, and distinguish the formulation from the pure pool dispatch.
4 Pool/bilateral dispatch with security constraints
There are two important modeling aspects that are not considered in (5)-(11), namely: the voltage/reactive power representation, and the security constraints. The first aspect is addressed in [23] and is out of the scope of the present discussion. On the other hand, the security constraints are modeled by means of post-contingency optimal power flows coupled by ramping limits constraints. A ramping limit is understood as how fast a generator can change (increase or diminish) its output in order to minimize load shedding. The proposed model is presented in (12)-(20). Where the upper subscript k stand for the contingency, being k= 0 the base case. In this case a contingency consists on the failure of a line or transformer. In the present formulation only single contingencies have been considered, however, the model can be easily expanded to include multiple contingencies. Furthermore, the set of constraints related to bilateral contracts are only considered in the base case and not under contingencies. That is because in the proposed model, the security of the system prevails over the accomplishment of the bilateral contracts. In order to avoid unfeasibility after contingencies we have introduced fictitious generators in load buses. Such generators guarantee the enforcement of power balance constraints and represent load shedding. Consequently, the objective function consists in minimizing the generation and load shedding cost.
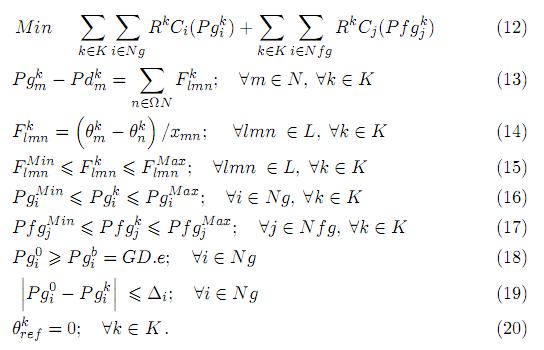
The probability of the system to operate on the base case (without any contingency) is the unit minus the sum of the probabilities of single failure of all lines and transformers as shown in (21).

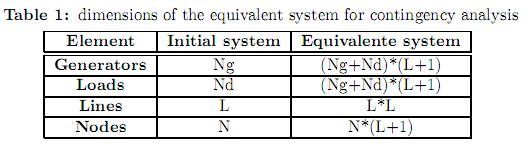
To approach the optimization problem given by (12)-(20), we use the methodology proposed in [16] and [17] which consists in artificially building an equivalent power system composed by islands. These islands correspond to the initial system (base case without contingencies) and to the system after each of the contingencies. The dimensions of such equivalent system are presented in table 1.
5 Test and results
In order to show the validity of the proposed approach several tests were performed with the Wood and Wollemberg 6 bus power system [24] and the IEEE-RTS 24 bus test system [25]. The analysis is based on the performance of the network with and without security constraints, and the increment of firm bilateral contracts. All tests have been performed in Matlab using the linprog function. However, any other LP solver can be used.
5.1 Case 1: 6 bus test system
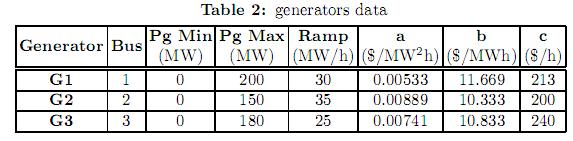
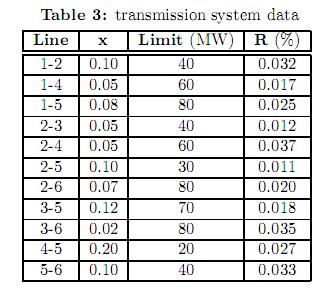
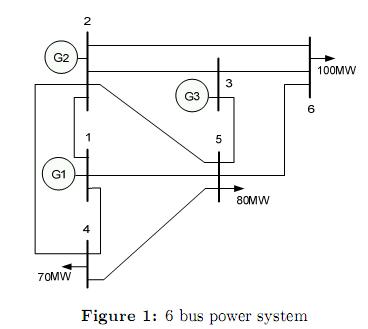
The Wood and Wollemberg 6 bus power system is shown in figure 1. Tables 2 and 3 summarize the system data. In this case, for the sake of simplicity, we have considered up and down ramps to have the same value. The bid cost curve of the generators is given by (22) and the bilateral contracts are expressed by the GD matrix shown in (23). This matrix represents the energy traded between generators and loads, for example, GD (3,6) = 78 means that the generator in bus 3 has a firm bilateral contract for 78 MW with the load located in bus 6. Note that the sum of the columns for all bilateral contracts in GD matches the total system demand in nodes 4, 5 and 6.

The tests were performed using a DC model of the network, and are focused on the comparison between the combined pool/bilateral dispatch with and without security constraints. In order to avoid unfeasibility problems and to represent load shedding, fictitious generators where located in load buses with cost coefficientsaand b equal to 200 $/M W2h and 500$/MW2h, respectively. These coefficients model the cost of load shedding.
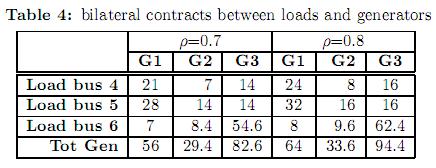
One of the main purposes of the simulations is to evaluate the impact of firm bilateral contracts in the overall security of the system. This impact is evaluated by performing a series of dispatch solutions where the bilateral contracts are gradually increased. This is accomplished by working with the parameterized matrix GD(ρ)= ρ.GD; 0 ≤ 6 ρ ≤ 61. Note that when ρ=1, the demand is fully supplied by the bilateral contract market, on the other hand, when ρ=0, the demand is fully supplied by the pool market. Table 4 shows the bilateral contracts for ρ=0.7 and 0.8.
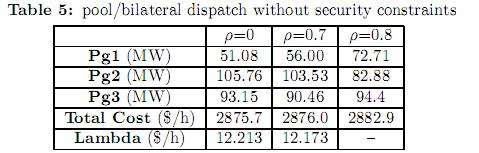
5.1.1 Pool/bilateral dispatch without security constraints. Several tests were carried out with different values of the parameter ρ. Table 5 summarizes the results obtained.
In the first run ρ was set to zero letting the demand being fully supplied by the pool market. In this case, the pool market prices, named as lambda (defined as the Lagrange multipliers of the active power balance equations) are the same for all buses (12.213$/h). That is because there is no congestion and the effect of power losses has been neglected. In the second case, with ρ=0.7 the constraint related to the accomplishment of the bilateral contracts for generator G1 is active (see total generation in table 3). Consequently, generator G1 is set to produce 56 MW. The dispatch is then modified as shown in the second column of table 4. As the output of generator G1 was increased, the outputs of generators G2 and G3 were decreased (to keep the generation/demand balance). The pool market prices are again the same for all buses (no congestion and no losses) however, they are lower than in the first case. That is because the marginal generators (G2 and G3) reduced they output. In this case, generator G1 is said to be “out of merit” and any incremental demand will be supplied either by generator G2 or G3 at the same marginal price. In the third case studied, the parameter ρ was set to 0.8. In this case, the constraint related to the accomplishment of bilateral contracts for generator G3 is active. Consequently, generator G3 is set to produce 94.4 MW. The enforcement of the bilateral contracts leads to congestion on line 3-6 causing the pool market prices to be different in all buses. The pool market prices for this case are shown in table 6.
It can be observed that the marginal price of bus 3 is negative. This means that a decrement in the output of generator G3 will lead to an improvement of the objective function. Furthermore, it can be observed, from table 5, that the enforcement of the constraints related to firm bilateral contracts leads to higher operational cost.
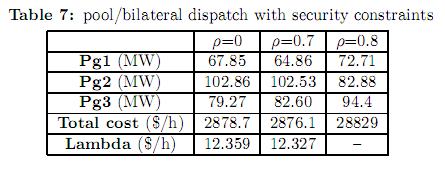
5.1.2 Pool/bilateral dispatch with security constraints. The same tests presented in the previous section were carried out considering security constraints. Results are reported in table 7.
To account for the contingency constraints, an equivalent system composed by islands is built. The equivalent system consists on the base case (initial topology without contingencies) and the system after each of the contingencies. The different islands of the equivalent system are coupled with ramping limit constraints. A ramp limit imposes an upper/lower boundary in the change of generation after each contingency with respect to the generation in the base case, see (19). As the objective function considers not only the generation in the base case, but also the generation after each of the contingencies (including the fictitious generators that account for eventually load shedding), the result is a dispatch scheme that minimizes the cost of operation and the expected load shedding. From table 7 it can be observed that when security constraints are considered, the pool market prices as well as the operational cost are slightly higher. In this particular case, accounting for security constraints does not have a great impact in the total operating cost. However, the differences between the dispatch schemes are important. For example, when firm bilateral contracts are not considered, generator G1 produces 51.08 MW in the traditional model (table 5) and 67.85 MW in the security constraint model. However, when there is an important participation of bilateral contracts (ρ=0.8) both models achieve the same optimal solution.
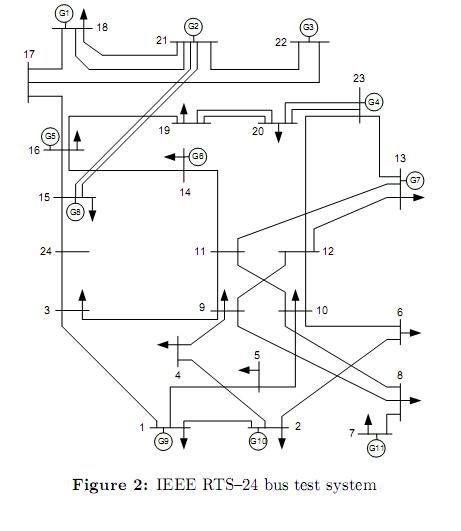
5.2 Case 2: IEEE RTS-24 bus test system
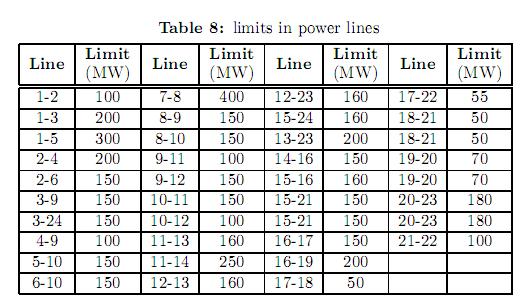
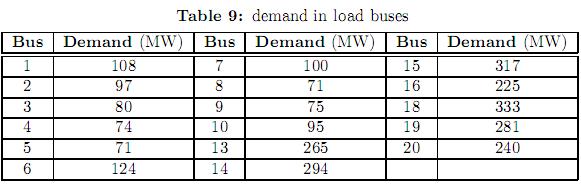
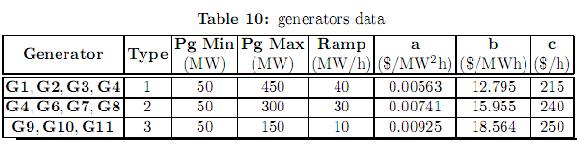
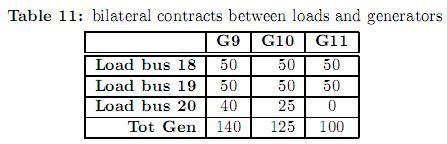
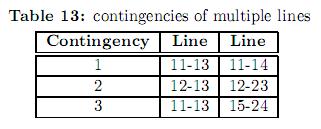
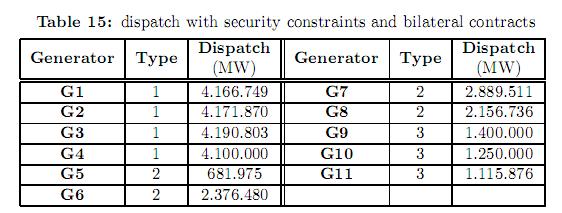
Figure 2 shows the IEEE-RTS 24 bus test system. The original data of this system can be consulted in [25]. This system comprises 38 lines, 11 generators and 17 loads. Some modifications have been considered in loads, power line limits and generation as shown in tables 8, 9 and 10, respectively. Generators have been divided in three types. For each type, a different bid cost function was considered, ranging from the cheapest (type 1) to the most expensive (type 3). Table 11 shows the bilateral contracts considered.
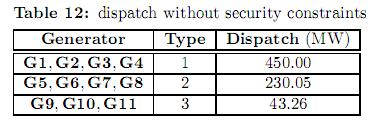
5.2.1 Optimal dispatch without security constraints. The optimal dispatch without bilateral contracts and without security constraints is presented in table 12. It can be observed that the cheapest generators (type 1) are dispatched at their maxima. On the other hand, the second and third groups of generators are dispatched at 230.05 and 43.26 MW, respectively. In this case, there is no congestion in transmission lines, and generators of types 2 and 3 are dispatched at a level in which the marginal costs of their bidding curves are equal. Such marginal cost is 18.78$/h, and represents the pool market price. The total operation cost of this dispatch is 165339.30$/h.
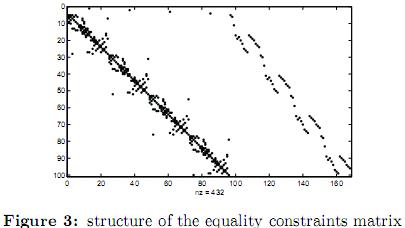
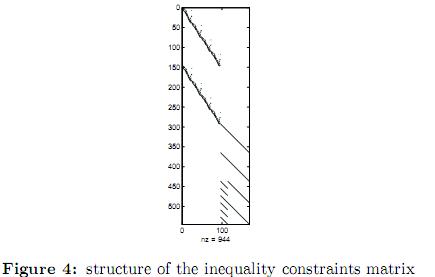
5.2.2 Optimal dispatch with security constraints. In this example multiple contingencies were considered as shown in table 13. The lines selected for the contingencies are those which cause the greatest impact in the system in terms of load shedding as reported in [26]. For the three contingencies under study, the same probability of 0.001% has been used. The structure of the equality and inequality constraints matrices of the equivalent system are shown in figures 3 and 4 respectively. Such figures are obtained by a spy- plot in Matlab. In the upper right part of figure 3 four dots equally spaced descending from left to right can be easily spotted. These dots correspond to the constraints of the slack bus for the base case and each of the three contingencies. The remaining of the figure corresponds to the active power balance constraints. The upper left portion of figure 4 corresponds to the power limit constraints in lines and transformers. The middle right portion of figure 4 corresponds to the active power limits constraints of generators, and the lower portion corresponds to the up and down ramp limits.
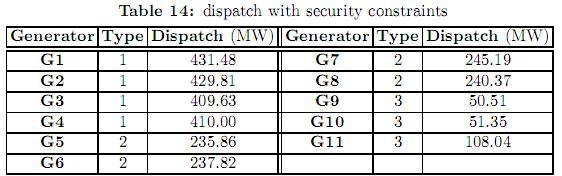
The optimal dispatch that minimizes load shedding for these contingencies is shown in table 14. It can be observed that type 1 generators are not dispatched at their maxima, and instead, the output of type 3 generators (the most expensive) has been increased. The differences between the dispatches presented in tables 12 and 14 are due to the security constraints. In order to reduce load shedding after a contingency, more expensive generation has to be used. The cost of this dispatch is 177548.84$/h representing an increase of 7.38% with respect to the dispatch without contingencies. The pool market prices are 17.12$/h for all buses. Comparing to the case without contingency constraints, these prices are lower. That is because there is generation available from the cheapest generators (type 1), as opposed to the first case in which these generators were dispatched at their maxima.
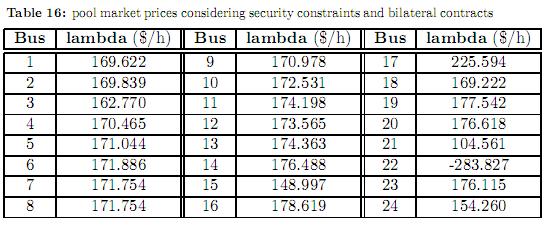
Table 15 shows the dispatch considering the firm bilateral contracts presented in table 11. The enforcement of these contracts leads the system to congestion in the corridor 18-21 and line 17-22. Consequently, the pool market prices in all nodes are different as shown in table 16. The marginal prices correspond to the dual variables (Lagrange multipliers) of the power balance equations (equality constraints), and as such they indicate the cost of consuming an additional megawatt in a given bus. It can be observed in table 16 that the marginal price in node 22 is negative. That means that an increase of demand (or alternatively, a decrease in generation) will improve the objective function. In this node generator G11 is located. This generator belongs to the group of the most expensive generators, and regardless of its bilateral contracts it is always dispatch above 100 MW to improve the security of the system. Most of the over cost when considering contingency constraints is due to the high dispatch of this generator (see tables 12 and 14).
6 Conclusions
This paper proposes a one-step optimal power flow model that dispatches the pool in combination with firm bilateral contracts considering security constraints. The basic purpose of this paper is to analyze the impact of post-contingency security constraints in a combined pool/bilateral dispatch approach. The tests performed focused on the comparison between the traditional model and the model with security constraints. As expected, the overall dispatch costs are higher when security constraints are accounted for. Furthermore, it was found that the enforcement of firm bilateral contracts (when they are above certain limits) might lead the system to congestion.
The main contribution of the proposed methodology is the inclusion of contingency constraints in a pool/bilateral market scheme using a one-step approach. The proposed methodology adequately handles contingency constraints. However its main drawback consists on the size of the equivalent system; which might render the problem intractable for large power systems, especially when multiple contingencies are considered. This inconvenient can be contoured using specialized procedures for efficient handling of sparse matrices. Future work will include this kind of procedures, as well as a more detailed description of the network and market rules.
References
1. A. Gómez-Expósito, A. J. Conejo and C. Cañizares. Electric Energy Systems; Cap 5: Economics of Electricity Generation, ISBN 978-0- 8493-7365-7. CRC Press Taylor Francis Group, 2009. Referenced in 10 [ Links ]
2. O. Alsac, J. Bright, M. Prais and B. Stott. Further developments in LP-based optimal power flow. IEEE Transactions on Power Systems, ISSN 0885- 8950, 5(3), 697-711 (1990). Referenced in 11 [ Links ]
3. M. Ilic, F. D. Galiana and L. Fink. Power Systems Restructuring: Engineering and Economics, ISBN 0792381637. Springer, 1998. Referenced in 11 [ Links ]
4. F. Perry Sioshansi. Competitive Electricity Markets: Design, Implementation, Performance, ISBN 978-0-08-047172-3. Elsevier Global Energy and Economics Series, 2008. Referenced in 11 [ Links ]
5. J. Martines-Crespo, J. Usaola and J. L. Fernández. Security-constrained optimal generation scheduling in large-scale power systems. IEEE Transactions on Power Systems, ISSN 0885-8950, 21(1), 321-332 (2006). Referenced in 11, 12 [ Links ]
6. Y. Fu, M. Shahidehpour and Z. Li. AC contingency dispatch based on security- constrained unit commitment . IEEE Transactions on Power Systems, ISSN 0885-8950, 21(2), 897-908 (2006). Referenced in 11 [ Links ]
7. B. C. Ummels, M. Gibescu, E. Pelgrum, W. L. Kling and A. J. Brand. Impacts of wind power on thermal generation unit commitment and dispatch. IEEE Transactions on Energy Conversion, ISSN 0885-8969, 22(1), 44-51 (2007). Referenced in 11 [ Links ]
8. J. Hetzer, D. C. Yu and K. Bhattarai. An economic dispatch model incorporating wind power. IEEE Transactions on Energy Conversion, ISSN 0885-8969, 23(2), 603-611 (2008). Referenced in 11 [ Links ]
9. Kuo Cheng-Chien. A novel coding scheme for practical economic dispatch by modified particle swarm approach. IEEE Transactions on Power Systems, ISSN 0885-8950, 23(4), 1825-1835 (2008). Referenced in 11 [ Links ]
10. He Da-Kuo, Wang Fu-Li and Mao Zhi-Zhong. Hybrid genetic algorithm foreconomic dispatch with valve-point effect. Electric Power Systems Research,
11. J. G. Vlachogiannis and K. Y. Lee. Economicload dispatch-A comparative study on heuristic optimization techniques with an improved coordinated aggregation- based PSO . IEEE Transactions on Power Systems, ISSN 0885-8950, 24(2), 991-1001 (2009). Referenced in 11 [ Links ]
12. F. C. Schweppe, M. C. Caramanis, R. D. Tabors and R. E. Bohn. Spot Pricingof Electricity, ISBN 0-89838-260-2. Springer, 1988. Referenced in 11 [ Links ]
13. J. Condren, T. W. Gedra and P. Damrongkulkamjorn. Optimal power flow with expected security costs. IEEE Transactions on Power Systems, ISSN 0885-8950, 21(2), 541-547 (2006). Referenced in 12 [ Links ]
14. S. K. Uehara, L. Nepomuceno, and T. Ohishi. A combined pool/bilateral model including post-contingency security constraints. Congresso Brasileiro de Automatica (CBA), Juiz de Fora, Brasil, 2008. Referenced in 12 [ Links ]
15. O. Alsac and B. Stott. Optimal Load Flow with Steady-State Security. IEEE Transactions on Power Apparatus and Systems, ISSN 0018-9510, 93(3), 745-751 (1974). Referenced in 12 [ Links ]
16. J. S. Thorp, R. J. Thomas and Jie Chen. Time-space Methods for Determining Locational Reserves: A Framework for Locational Based Pricing and Scheduling for Reserve Markets. Report to the Department of Energy, 2002. Referenced in 12, 15 [ Links ]
17. J. M. López-Lezama, C. E. Murillo-Sánchez, L. J. Zuluaga and J. F. Gutiérrez- Gómez. A contingency-based security-constrained optimal power flow model for revealing the marginal cost of a blackout risk-equalizing policy in the colombian electricity market. Proceedings of the IEEE Transmission and Distribution Conference and Exposition: Latin America, ISBN 1-4244-0287-5, 1-6 (2006). Referenced in 12, 15 [ Links ]
18. J. Chen, J. Thorp, R. J. Thomas and T. D. Mount. Locational Pricing and Scheduling for an Integrated Energy-Reserve Market. Proceedings of the 36th Hawaii International Conference on Systems Sciences, ISBN 0-7695- 1874-5, 2003. Referenced in 12 [ Links ]
19. F. D. Galiana and M. Ilic. A Mathematical Framework for the Analysis and Management of Power Transactions under Open Access. IEEE Transactions on Power Systems, ISSN 0885-8950, 13(2), 681-687 (1998). Referenced in 12 [ Links ]
20. F. D. Galiana, I. Kockar and P. C. Franco. Combined Pool/Bilateral Dispatch - Part I: Performance of Trading Strategies. IEEE Power Engineering Review, ISSN 0272-1724, 17(1), 68-69 (2001). Referenced in 13 [ Links ]
21. I. Kockar and F. D. Galiana. Combined Pool/Bilateral Dispatch: Part II-Curtailment of Firm and Nonfirm Contracts. IEEE Transactions on Power