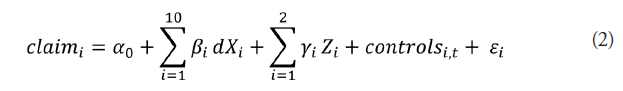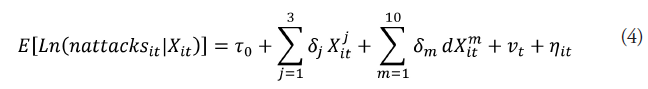Introduction
The attacks registered in the Global Terrorism Database (GTD), during the period 1970-2011, showed that one in seven terrorist acts is listed as claimed (Abrahms & Conrad, 2017); despite the fact that the desire of terrorist groups is more to impose a political agenda through coercion than the recognition itself of such attacks (Pape, 2003). This situation provides empirical evidence for critics of the rational strategy model, who highlight the predominance of unclaimed terrorist attacks because in these cases the state does not make favorable concessions to the perpetrators political agenda (Abrahms, 2008). Hence, analyses of terrorism as a rational strategy are unable to explain the claim phenomenon in terrorist attacks (Lake, 2002).
The structure of a terrorist organization consists of recruits and leaders (Abrahms & Potter, 2015) without necessarily having the same interest. Recruits are prone to perpetrate attacks against civilians, considering that their incentives include peer recognition, a low amount of available resources and little experience and background in the terrorist group, which prevent them from measuring the negative political consequences of attacking civilians. On the other hand, leaders seek to attack government targets and avoid claiming the attacks on civilians. These antagonistic motivations make agency problems emerge in the terrorist organization, where the agent (recruit), due to incentives, tends to execute attacks on civilians, while the principal (group leader) avoids claims of attacks on civilians.
Considering terrorism as a strategic method of coercion, the main variables that explain claims of terrorist attacks are those that indicate the capacity and potential of the group to cause damage to their opponent. Then, in the perspective of the principal-agent problem, the explanatory variables of claim show the divergence between the incentives and actions within the terrorist groups. Therefore, they help to provide empirical evidence illustrating the specific circumstances in which terrorist groups claim their attacks. It is worth mentioning that the influence of religions, such as Islam, is another variable to take into account (Abrahms & Potter, 2015); since the attacks against civilians are perpetrated in the name of religion rather than the political ideology of the group.
Several studies have researched into the claim phenomenon (Hoffman, 2010), especially Abrams and Conrad, who propose to analyze it in terrorist groups under the principal-agent problem, by taking "attacks on civilians" as the main explanatory variable to be tested (Abrahms & Conrad, 2017). In this sense, the claim of an attack is a key element in the behavior analysis of such groups.
Although this phenomenon was exposed by Abrahms & Conrad (2017); this document goes beyond developing a logistic model with cross-sectional information for the period 2012-2018, and introduces the attacks as a variable involving damage to private property, according to Pape (2003) and Lake (2002); in addition, some probability scenarios are explored. As a novelty, a dynamic stochastic model with a negative binomial distribution is implemented with panel data to investigate the determinants of the number of attacks in a country per year under the same context of the previous model. We consider this model could be a preliminary instrument in addition to the existing ones to anticipate the possibility of repeating an attack in any country under conflict.
In general terms, the results show that attacks on civilians, a high level of physical integrity violations and the influence of Islam religion on the group are key when claiming a terrorist attack. On the other hand, the attacks frequency increases in a country when there are previous attacks involving assassinations, armed attacks, financing of the terrorist group, damage to private property, among others.
Perspectives on terrorism
Countless authors have sought to understand the phenomenon of terrorism, considering various perspectives that include five conceptual frameworks when interpreting it as a crime, politics, war, communication or religious fundamentalism (Schmid, 2004).
Abrams proposed to identify what terrorists want in order to define an effective strategy against terrorism. Thus, by understanding the incentive structure of terrorists and identifying them as individuals in search of 'social benefits', it is possible to combat them effectively (Abrahms, 2008). In this perspective, he undertook an experiment in order to highlight the negative political effect of the use of terrorism and observed that the extremism of the employed strategy (terrorist attack) is extrapolated by the public and perceived as part of the political aims of the group, who tends to point to it as an unreliable partner in negotiation (Abrahms, 2013).
While some authors promote simulation strategies in the classroom to identify the strategic nature of terrorism (Siegel & Young, 2009), authors such as Pape (2003) studied terrorist attacks during the period 1980-2001 and suicide terrorism as a strategy to force liberal democracies to make territorial concessions (Lake, 2002; Pape, 2003). Another research shows that groups with leadership deficits (absence of the leader) are more likely to attack civilians (Abrahms, 2008). Despite the above, empirical investigations show that the use of terrorism does not always imply the fulfilment of demands by state actors (Abrahms, 2012). A further research found that the interests of leaders, as evidenced through an analysis of terrorist propaganda, tend to show a preference for fewer attacks on civilians than is actually the case (Abrahms Beauchamp & Mroszczyk, 2017).
According to Kluch & Vaux, (2016), when examining the geographical concentration and persistence of terrorism they found a geographical bias, as terrorist attacks are highly concentrated in specific areas. In the case of Al-Qaeda, the group extended its reach by using the electronic jihad to radicalize Muslims in western diaspora communities, seeking a greater flow of resources to carry out terrorist attacks (Rudner, 2017), which is evidence of the use of the Internet by terrorist groups as part of their communication and recruitment strategy (Aly, et al., 2017).
Some cases show that certain states sponsor terrorism considering the strategic and political benefits they provide, despite the domestic and international risks involved. In this sense, a principal-agent model analysis is used to evaluate the impact in terms of cost/ benefit state sponsors have when sponsoring a terrorist group (Berkowitz, 2017). As for the principal-agent problem, Gary Miller explained part of its evolution over time (Miller, 2005). This theoretical concept has been applied in areas such as jurisprudence, redefining the problem through the proposal of a proxy power (Leow, 2019).
In the international sphere, different states have faced the principal-agent problem by seeking to carry out joint arms projects, obtaining as a consequence, within the framework of international cooperation on these projects, that efforts to solve the principal-agent problem aggravate collective action problems and vice versa (De Vore, 2011).
There are tendencies in terrorist groups that discredit them as entities acting under rational logic. Especially, there is a tendency not to claim their attacks, preventing the attacked party from identifying the attacker and the political demands of the attacker from being taken into account as an implicit message of the attack (Abrahms, 2008).
Other authors highlight the scant attention paid to the phenomenon of claim as a subject of study in the phenomenon of terrorism, stating that one of the main variables tending to influence the decision to claim is the existence of a competitive environment with the presence of multiple terrorist groups in a territory, competing for a limited network of resources and sympathizers. When investigating this issue, a logistic model that identifies the ideology of terrorist groups, the intensity of counterterrorism efforts and the use of suicide attacks are tested, as variables that positively influence the probability of claiming the perpetrated attack. However, this contribution is supported in only one study scenario (Israel), limiting the generalization of the findings, as it does not incorporate much ideological variation in the terrorist groups studied (Hoffman, 2010).
To examine the claim phenomenon, Austin L. Wright, using observations extracted from the GTD, World Bank, Amnesty International, and U.S. Department of State databases, tested a series of explanatory variables to explain the claim phenomenon during the period 1998-2004 using a logistic model and ordinary least squares (Wright, 2011). In contrast to Hoffman (2010), he did not find statistical evidence that the existence of a competitive environment positively influences the probability of claims. However, he found statistical evidence that the variables indicating capacity in the group (magnitude of the attack, suicide attack and intention to manipulate through force), positively influence the probability of claiming a terrorist attack. Additionally, he found that religiously motivated attacks have a lower probability of being claimed.
Shapiro (2013) introduces the principal-agent theory as a tool for the analysis of terrorist groups behavioral description, to highlight the dilemma a terrorist group leader's face among three variables that are relevant to the group and yet negatively correlated: "control", "security", and "efficiency". In a subsequent investigation, Kearns, Conlon & Young, (2014) argues that terrorist groups can make strategic choices about whether to claim their own or others' attacks, and that these choices are about the survival and achievement of the group's political objectives.
Abrahms and Conrad's perspective provides a new explanatory possibility, and although the claim continues to be interpreted as a rational strategy, it is no longer supported in the variables that indicate capacity, but in the key variable that indicates the inclusion or absence of civilians in the attack (Abrahms & Conrad, 2017). Based on the fact that most attacks are claimed by the leader or under his authorization, the authors argued that he or she tends to claim those attacks that are politically profitable for the organization, tending to ignore the claim of those that include civilians. However, despite the fact that attacks on civilians are not convenient for the organization (Abrahms, 2013), they tend to occur due to the divergence of incentives between the principal (leader of the terrorist group) and the agent (subordinate).
Leaders have more experience with the political consequences of the attacks carried out and have a greater amount of resources at their disposal but face greater difficulties in disengaging from the group and are the ones in charge; subordinates represent the opposite: relatively little experience in the group, less available resources, relative ease in cutting ties with the group and the existence of incentives (recognition and promotion in the hierarchical structure) to stand out among their peers (Abrahms & Conrad, 2017). Due to these antagonistic characteristics, attacks including civilians will occur (perpetrated by subordinates acting under their incentive scheme) with a low level of claim (encouraged by the group leader, who is guided by his own incentive scheme).
Kearns, (2021); disaggregates the explanatory variable into three components: claimed attacks, attacks with attribution of credit (where there is no claim, but the attacker is believed to be known) and unclaimed attacks. By using a multinomial logistic regression, the researcher found that suicide attacks increase the probability of claiming credit for them but not of attribution. Additionally, she proposed the verification of methodologies and hypothesis with the use of different databases and the analysis of specific terrorist groups.
A look at the principal-agent problem
Many authors have used the theoretical framework of the principal-agent to talk about the phenomena of conflict and terrorism (Abrahms, Ward & Kennedy, 2018), but it is Abrahms & Conrad (2017) who highlighted the lack of claims in the vast majority of terrorist attacks. Considering attacks as tools of coercion, the variables that demonstrate the strength and capacity of the attack would positively influence the phenomenon of claim (Lake, 2002; Pape, 2003). In this sense, the number of victims of the attack, the type of attack (indicating greater or lesser availability of resources) and the size of the group are relevant variables when referring to claims. However, the authors tested a logistic model seeking to explain the phenomenon of claims in terrorist attacks, using explanatory variables such as "civilian target", to indicate whether the attack was directed against civilians, "number of fatalities", for the total number of fatalities in the attack, "state repression" which estimates the level of physical integrity rights violations recorded in a country, "assassination" showing whether the attack was in the form of an assassination, "multiparty competition" and "number of groups" which estimates the level of competition among terrorist groups, "organization size" approximating the size of the group making the attack, "foreign state sponsorship" indicating whether terrorist groups are sponsored by a government and "Islamist ideology" if those groups are inspired by Islam in any way. Taking into account the problem of the principal-agent, they proposed to take "civilian target" as the main explanatory variable to be tested. According to what was expected, they found throughout the proposed specifications, a statistical significance with a negative effect of the "civilian target" variable, which contributes evidence to the theory of the principal-agent applied to the phenomenon of terrorism.
Regarding the innovative perspective and the results, the work ofAbrahms & Conrad (2017) is the main reference for this research. Our contribution to the empirical literature is at least carry out threefold. Firstly, we introduce a brand new variable to indicate the presence of damage to private property in the terrorist attack (pdam). Secondly, we use a new time period to estimate the empirical modelling of claimed attacks (2012-2018). Thirdly, as a novelty, we implement a dynamic negative binomial stochastic model with panel data that estimates the probability of repetition of an attack in a country. In this sense, the aim of the procedure is to approximate and broaden the performed analysis; to provide new evidence to the problem of the principal-agent in the context of terrorism.
Methodology
Descriptive analysis
Information for this research was drawn from three databases: the Global Terrorism Database (GTD), version 17 September 2019; the Big Allied and Dangerous (BAAD), version 5 June 2011; and the Political Terror Scale (PTS), version August 2019. After cleansing and merge the BAAD database with seven versions of PTS and GTD, a resulting database with cross-sectional information was obtained which consisted of 48,831 observations.
Due to the merged database contains Three- time measures (day, month and year), and there are terrorist groups attacking simultaneously in two countries, an analysis with panel data is not possible. Therefore, to use the model of Abrahms & Conrad (2017), the information is analyzed as a cross-section and the attack is the unit of analysis itself. However, if the information is adjusted, a panel data model is possible through the collapse of the base, although the objective of the study could no longer be the claim of the attack. This idea supports the second modeling.
Table 1 shows some descriptions of the key variables used in the empirical model (description of the variables is in the appendix A). All of them are dummy variables, except for the number of fatalities (nfat). It is worth mentioning that the mean of a dummy variable coincides with the success of the event. Therefore, column one shows the number of observations, column two the means, and the last two columns show the minimum and maximum values they assume.
Table 1 Descriptive statistics of several attack variables
| Variable | Observations | Mean | Minimum | Maximum |
|---|---|---|---|---|
| Claimed | 44,831 | 0.362 | 0.0 | 1.0 |
| Civil target | 38,054 | 0.403 | 0.0 | 1.0 |
| Srep | 33,399 | 0.972 | 0.0 | 1.0 |
| Hostage | 44,831 | 0.116 | 0.0 | 1.0 |
| Islam | 11,951 | 0.650 | 0.0 | 1.0 |
| States pons | 11,951 | 0.868 | 0.0 | 1.0 |
| Number fat | 41,441 | 3.920 | 0.0 | 1,570 |
Source: own elaboration
The figures also show that claims of attacks by terrorist groups (the endogenous variable in the model) have a considerable participation as 36.2% of them are claimed, mainly in attacks in Afghanistan, India, Pakistan, the Philippines and Turkey. In the case of civilian targets (ctarget), 40% of the targets attacked are civilians, and the remaining 60% are military, government or police. In terms of the number of fatalities (nfat), this has an average of 3.9 deaths; the maximum number of deaths in an attack was 1,570 people in Iraq in 2014.
In the case of the right to physical integrity, the srep variable shows that in almost all the analyzed countries (97.2%) such rights are highly violated. Taking hostages (host) is not a common practice in the attacks, since only 11.6% of the cases have been reported, however Afghanistan and Iraq are the countries with the highest number of attacks that hold hostages (30.3%). As for religion, Islamism (Islam) is the source of inspiration for the groups that committed more than 65% of terrorist attacks worldwide. The groups with attacks in Colombia have no link with this religion. The results indicate that 86.7% of the attacks have been made by groups supported by at least one foreign government (sspo).
Finally, it is worth mentioning that seven countries (Afghanistan, Philippines, Turkey, India, Colombia and Pakistan) are responsible for more than 95% of terrorist attacks (not shown in the table). Among them, Afghanistan is the country with the highest participation rate.
Empirical modeling
To achieve the proposed objective, this section contains two empirical models. Basically, the first one updates the model made by Abrahms & Conrad (2017) with information from the period 2012-2018 and shows the variables that determine the probability of claiming a terrorist attack. Our model contribution lies in the inclusion of the private property damage variable (pdam), in addition to analyzing a new period. Further, to deepen our analysis, a set of probabilistic scenarios is explored depending on certain values assumed a priori by the independent variables.
On the other hand, the second proposed model captures the determinants of the number of terrorist attacks in a country, using a dynamic negative binomial model with panel data. This model implies, methodologically, a separation from the one undertook by Abrahms & Conrad (2017), and constitutes a contribution to the empirical modelling of current armed conflicts. As far as we know, there is no one with these characteristics in the recent empirical literature.
Claiming the attack model
Following Abrahms & Conrad (2017), to obtain the probability that a terrorist group would claim an attack as its own, according to a set of explanatory variables, a discrete regression model with logistic distribution (logit model) is implemented, estimated by a maximum likelihood estimation with cross-sectional information. The general structure of the model is as follows:
Where y is the endogenous variable, X is the set of explanatory and control variables; and Φ(.) is the Normal FDA. In specific terms, the model is as follows:
Where claim is a dichotomous variable that assumes a value equal to 1 if the attack is claimed by terrorist groups and 0 otherwise. In the dichotomous vector (dXi), the following events with a value equal to 1 and 0, if it is not the case, are found: attacks against civilians (ctarg), large number of violations of bodily integrity in the attacked country (srep), attacks as armed assaults (arass); taking hostages in the attack (host); attacks as assassinations (assa); size of the terrorist group (osize), government support to the group (sspo), suicide attack (sui) and Islamic inspiration to the attacking group (islam). As mentioned above, the presence of damage to private property in the attack is now included (pdam). In the vector of quantitative variables (Zi), there are the number of fatalities (nfat) and the number of terrorist groups in the country having perpetrated attacks (nterr).
On the other hand, we control per year and country to collect macroeconomic effects and their own characteristics in time through the dichotomous variables year and country. Finally, it is worth mentioning that random errors (εi) follow a logistic distribution and we consider they are related to the interior of terrorist groups.
Following Abrahms & Conrad (2017), in the group of dichotomous variables, it is expected that the ctarg variable will show a negative sign, because if the attack includes civilians, terrorist groups will not claim it due to the politically negative consequences this implies. As for the srep variable, a negative sign is expected since it is believed that a greater number of violations of bodily integrity in a country will make terrorist groups concerned about the consequences of claiming the perpetrated attack. Regarding the assa, arass, host, and sui variables, the expected coefficients are positive, since the perpetration of these types of attacks requires a greater number of resources, which will make terrorist organizations more likely to claim them, due to the desire to highlight their group has a greater capacity.
With regard to the osize variable, a coefficient with a negative sign is expected, since it is believed that fewer numerous groups will tend to claim others' attacks in order to appear more capable; however, authors remark that a second plausible explanation is that agency problems will occur more frequently in larger organizations. A negative sign is expected for the sspo variable, as it is believed that government sponsorship of terrorist organizations will cause the latter to avoid claiming for attacks involving civilians, seeking to avoid the international opprobrium of the sponsoring government. The islam variable will present an inverse or negative relationship with the claim of the attack, since it is assumed that the organization will perform the attack as an end in itself (Wright, 2011).
In addition, with thepdam variable (which is a new variable introduced in this analysis) and following Lake (2002) and Pape (2003), we consider that the sign shown will have to be positive, in the belief that attacks that include property damage demonstrate greater capacity, and therefore they are more likely to be claimed. Finally, in the case of the quantitative variables, the nfat variable, a coefficient with a positive sign is expected, since with a greater number of victims in the attack, groups will be able to demonstrate a greater capacity through the claim. On the other hand, the nterr variable is expected to show a positive relationship with the endogenous variable, since the existence of multiple groups in a territory would force them to compete for a limited number of resources and sympathizers (Hoffman, 2010)
Model of number of attacks in a country over time
To capture the determinants of the number of terrorist attacks per period, a dynamic negative binomial model is implemented with panel data which is estimated under a maximum likelihood framework. The choice of this model is due to the fact that the terrorist attacks in each country per year are a counting variable, which assumes finite values in the positive integers and also shows over dispersion; therefore, it follows a negative binomial distribution.
In addition, a lag is introduced in each of the dichotomous variables and in the first differences in the quantitative variables not only to capture dynamic effects, but also to avoid simultaneity problems. In this sense, this model differs from the previous one, not only in the methodological strategy, but also in what it seeks, since in the same previous conflict scenario it observes the determinants that increase or decrease the number of attacks in the analyzed countries, which can serve as a preliminary instrument to try to foresee or avoid them by local governments, or international organizations.
Because of this, the model is a contribution to the empirical literature on terrorism at the international level. The general model is as follows:
Where y is the count endogenous variable, X is the vector of explanatory variables including the control ones; and exp is the exponential function. Once linearized, in specific terms the model is as follows:
Where the dependent variable is the number of attacks (nattacks) that a country suffers per period. The explanatory variables are also divided into quantitative X j it and qualitative (dXm it). The number of attacks claimed by terrorist groups (nclaim), the number of fatalities due to the attack (nfat) and, finally, the number of terrorist groups in a country that have made an attack per year (nterr) are in the first group. The remaining variables conforming the second group are dichotomous and are the same used in the previous model; furthermore, it is assumed that they also follow the same expected signs established above.
It is worth mentioning that this model accounts for the fixed effects of the year (vt) and the country (vs), because the unit of analysis is now the territory and not the attack itself. Furthermore, we assume that random errors (ηit) follow a Gamma-Poisson-mixture distribution.
Results and Discussion
Claimed attacks model
Table 2 shows the results of the logit model. The first column displays the estimates based on the modelling of Abrahms & Conrad (2017) with data from the period 2012 to 2018. In the second column, the same model is shown but with the addition of the private property damage (pdam) variable as a new proposal. Both columns consider robust standard errors grouped per terrorist group to obtain the correlation between perpetrated attacks by the same group. Column 3 shows the model in column 2 with robust errors but without considering this correlation. Lastly, column 4 includes interaction effects.
Table 2 Claim model's results. Average marginal effects
| (1) | (2) | (3) | (4) | |
|---|---|---|---|---|
| Dep variable: claim | ||||
| ctarg | -0.269*** | -0.276*** | -0.276*** | -0.163*** |
| (0.060) | (0.068) | (0.019) | (0.025) | |
| nfat | 0.006*** | 0.004*** | 0.004*** | 0.005*** |
| (0.001) | (0.001) | (0.001) | (0.001) | |
| srep | 0.586** | 0.627** | 0.627*** | 0.589*** |
| (0.290) | (0.294) | (0.166) | (0.168) | |
| assa | 0.051 | 0.096** | 0.096*** | 0.080** |
| (0.036) | (0.042) | (0.031) | (0.031) | |
| host | 0.033 | 0.117 | 0.117*** | 0.087*** |
| (0.090) | (0.086) | (0.028) | (0.029) | |
| arass | -0.045* | 0.029 | 0.029* | 0.023 |
| (0.024) | (0.036) | (0.016) | (0.016) | |
| nterr | 0.011** | 0.009* | 0.009** | 0.009** |
| (0.005) | (0.005) | (0.004) | (0.004) | |
| osize | 0.015 | -0.035 | -0.035 | -0.034 |
| (0.158) | (0.155) | (0.079) | (0.076) | |
| sspo | -0.126 | -0.175 | -0.175** | -0.166** |
| (0.169) | (0.163) | (0.072) | (0.071) | |
| islam | -0.278*** | -0.314*** | -0.314*** | -0.315*** |
| (0.084) | (0.082) | (0.069) | (0.070) | |
| sui | 0.269*** | 0.269*** | 0.278*** | |
| (0.023) | (0.032) | (0.037) | ||
| pdam | 0.141*** | 0.141*** | 0.192*** | |
| (0.009) | (0.015) | (0.017) | ||
| ctarg*pdam | -0.243*** | |||
| (0.036) | ||||
| ctarg*nfat | -0.002 | |||
| (0.002) | ||||
| ctarg*sui | -0.110 | |||
| (0.088) | ||||
| Year/Country | Yes | Yes | Yes | Yes |
| Observations | 7,146 | 6,233 | 6,233 | 6,233 |
| P-seudo R2 | 0.172 | 0.191 | 0.191 | 0.197 |
| Misses/hits | 0.716 | 0.722 | 0.722 | 0.715 |
| Log-Likelihood | -3994 | -3394 | -3394 | -3367 |
Note. Robust errors grouped per terrorist group (column 1 and 2). Robust errors not grouped (column 3 and 4). Standard errors are shown in parentheses. Significance: *p < 0.10; **p < 0.05; ***p < 0.01
Source: own elaboration
The results show a good adjustment since the pseudo R2 is the expected one for a model with a high variance; additionally, the model is correct in the prediction of misses/ hits in more than 70% in all specifications and the log-likelihood function is minimized. In particular terms, regardless of the model specification, the attacks on civilians (ctarg) show a negative sign, hence, the probability of claiming the attack decreases ostensibly due to the politically negative consequences that this implies (Abrahms, 2013).
Conversely, the number of fatalities (nfat) is found to be directly related to the probability of claiming the attack in all the specifications. This behavior is what is expected from the theory of terrorism as a rational strategy (Lake, 2002; Pape, 2003), since a higher number of fatalities shows a greater warlike capacity of the group. The significance of the number of fatalities in the attack in all the specifications suggests a certain capacity for coercion (perceived by the leader) in those attacks with a greater number of victims. However, this coercive capacity is not given by a higher number of civilian deaths, since the interaction between it and the attack on civilians does not obtain statistical significance in the model.
In the case of state repression (srep), this is significant regardless of the specification of the model but the observed effect is not as expected, since the results of the model state that a higher level of physical integrity violations in a state tends to increase the probability that a terrorist group will make a claim of the perpetrated attack. This logic, however, is contrary to the belief that terrorist groups depress the level of claim for fear of state reprisals (Abrahms & Conrad, 2017).
Regarding the assassinations (assas), hostage-taking (host) and armed attacks (arass), all those variables show a positive relationship with the probability of claim; but assassinations are only significant in the model we propose, as is hostage-taking (in specification 3). This suggests that a more elaborate attack increases the probability of claim, because greater resources are required and therefore a terrorist group demonstrates greater capability to the public and to other terrorist groups. (Hoffman, 2010).
As for the number of terrorist attacks (nterr), the relationship with probability is direct, suggesting competition among terrorist groups carrying out attacks in a country for the number of resources and sympathizers (Salehyan, Siroky & Wood, 2014). The size of terrorist organizations also does not explain the possibility of the claim happening in any specification. On the other hand, government support to terrorist groups (sspo) is only significant in the specification (3), showing, as expected, that the claim is avoided because it is likely to lead to international accusations and accusations to the sponsoring governments (Salehyan, Siroky & Wood, 2014). Additionally, the sponsoring government guarantees support to terrorist groups to partially disengage from the local network of supporters and resources (Salehyan, Siroky & Wood, 2014).
In terms of Islamic ideology (Islam), the marginal effects are negative, showing that the possibility of claiming the attacks falls because it is believed that the attack is used as an end itself (Wright, 2011). These results challenge the prevailing belief that the religious influence of Islam prevents the claim of the attacks, to the extent that these would be oriented towards a spiritual end. Furthermore, this is due to the presence of terrorist groups influenced by the concept of jihad or holy war and attack for destructive purposes, without the intention of obtaining concessions. (Min, 2013).
The effect that suicide attacks show on claims is positive, as it demonstrates greater capacity of the group. (Pape, 2003; O'Rourke, 2009). Lastly, our proposed variable is significant and shows a direct relationship with the possibility of claiming credit for the attack. In this sense, damage to private property (pdam) shows a greater capacity of the group, for this reason, the group tends to claim the attack (Pape, 2003; O'Rourke, 2009).
In general, the models show a set of significant variables that surpass in number those of the model undertook by Abrahms & Conrad (2017). Those with the greatest impact are attacks on civilians, the high violation of physical integrity rights and Islamic ideology; while the number of fatalities generates the lowest incidence in probability. The additional proposed variables are also relevant to explain the claim. However, some signs were not as expected.
In order to deepen the claim model, Table 3 presents some scenarios that show the possibility of claim depending on some a priori values.
Table 3 Probability scenarios
| Scenario | Predicted probability |
|---|---|
| Mean | 63.82% |
| Maximum | 100.00% |
| Minimum | 8.11% |
| Scenario 4 | 31.30% |
| Scenario 5 | 75.20% |
Source: own elaboration
The probability predicted when all the explanatory variables of the model assume their average values is close to 64%. In scenario 2, when all of them assume their max-mum values, the probability of claiming the credit for the attack is 100%, while in scenario 3, when they assume their minimum values, the probability is 8.1%. In general, these scenarios are unlikely to occur because they are at the extremes and in the mean, since the vast majority of variables are dichotomous, so they assume values equal to 0 or 1, not their average.
However, scenarios 4 and 5 are more feasible. Indeed, if the attack includes civilians, the number of fatalities is at least 10, there is a high violation of physical integrity rights in the country where the attack is perpetrated, the attack is not a murder or an armed assault, but it includes the taking of hostages, if the terrorist group has at least 550 people, it is sponsored by a government, there are at most 10 local terrorist groups with some form of inspiration in Islam, the attack is not suicidal and does not include damage to private property, then the probability that terrorist groups claim responsibility for the attack is 31. 3%.
Scenario 5 has the same characteristics as the previous one, but the difference is that the first considers that the attack does not involve civilian casualties. When this happens, the probability increases significantly to 75.2%. This possibility is even higher if the attack includes hostages and if it is a suicide attack. Therefore, it can be concluded that these variables are the most sensitive for claiming the attack.
Perpetrated attacks model
The results of the dynamic negative binomial model with panel data are shown in Table 4. To compare results, column (1) shows the results of the model for all the analyzed countries as a whole (pooled), the same is done in the second column but considering the unobserved heterogeneity of the different analyzed territories (panel).
Tabla. 4 Estimates of Attack model. Average marginal effects
| Pooled (1) | Panel (2) | |
|---|---|---|
| Dependent variable: nattacks | ||
| nclaimedit-1 | 0.002** | 0.003* |
| (0.000) | (0.002) | |
| ctarg it-1 | 0.002** | 0.003*** |
| (0.000) | (0.001) | |
| nfat it-1 | -0.142 | -0.304* |
| (0.101) | (0.158) | |
| srep it-1 | -0.040 | -0.195* |
| (0.081) | (0.119) | |
| sssas it-1 | 0.107* | 0.259*** |
| (0.062) | (0.088) | |
| host it-1 | 0.071 | 0.169 |
| (0.068) | (0.132) | |
| arass it-1 | 0.152 | 0.464*** |
| (0.113) | (0.163) | |
| osize it-1 | -0.057 | 0.258 |
| (0.978) | (0.192) | |
| dnterr | 0.013* | 0.026*** |
| (0.008) | (0.010) | |
| sspo it-1 | 0.149 | 0.323** |
| (0.095) | (0.162) | |
| islam it-1 | 0.014 | 0.023 |
| (0.120) | (0.171) | |
| dsui | 0.002* | 0.002 |
| (0.001) | (0.004) | |
| dpdam | 0.002*** | 0.003*** |
| (0.000) | (0.001) | |
| Year/Country | Yes | |
| Year | Yes | |
| Constant | -3.74*** | -3.39*** |
| (0.994) | (0.340) | |
| Observations | 376 | 376 |
| Log-L | -1,463 | -1,670 |
Note. Robust errors grouped per terrorist group (column 1 and 2). Standard errors are shown in parentheses. Significance: *p < 0.10; **p < 0.05; ***p < 0.01
Source: own elaboration
Particularly, the numbers indicate that if a terrorist group has claimed an attack (nclaim) in the past, the probability of increasing the number of attacks in the present slightly rises both globally (0.2%), and for each country in particular (0.3%). Similarly, if terrorist incursions had civilian victims (ctarg), that will increase the possibility of attacking again in a very subtle way, since for both scenarios, it is less than 1%. However, if the number of fatalities (nfat) in an attack rises today in a given country, the probability of an attack in the future is reduced ostensibly (30.4%), possibly because of the judgments and repudiations the group receives at an international level. It is worth mentioning that this variable is not significant for the global case. On the other hand, in the case of those countries that have high violations of physical integrity rights (srep), something similar happens, since the results show that the possibility of an attack is modified within the country although in a negative way (-20%), while at a global level the repercussion is not conclusive.
Regarding the current incursions involving assassinations (sssas), they will increase the probability of attacking again in the future by around 11% for all countries as a whole, and more than double (26%) for each country in particular. As for armed attacks (arass), if these are currently perpetrated, the possibility of future irruptions by these terrorist groups increases by more than 46% in the analyzed territories; although they all grouped have an ambiguous impact. If the variation in the number of terrorist groups operating locally (dnterr) is positive, it increases the probability of another aggression by 2.6% in each country, which is exactly half the total. With regard to some government(s) support to subversive groups (sspo), the probability of future aggressions will rise by 32.3% in each affected country, since the support may be of a financial or warlike nature and this strengthens the capacity to attack in the medium and long term. Finally, the variation in damage to private property (dpdam) increases the possibility of attacks in both scenarios, but in a quite reduced form (less than 1%).
It is worth mentioning that the impacts of hostage taking (host), size of organization (orgsize), Islamic ideology (islam) and modification in the number of suicide attacks (nsui) are not conclusive, especially for the panel data model.
Conclusions
This document attempts to update and deepen the model proposed by Abrahms & Conrad (2017) regarding the claiming of attacks by terrorist groups worldwide and introduces a new model which shows the determinants of possible future terrorist attacks.
The obtained results offer evidence to the theory of the principal- agent applied to terrorist groups, however, they also suggest a relevance of variables such as the capacity shown in the attack, competition among groups and the influence of Islam at the time of making the claim. These results are consistent with the theory of terrorism as coercion and the principal-agent theory, as they highlight the problems of agency within terrorist groups caused when leaders tend to suppress the targeting of civilians, but also consider the influence of factors such as the capacity of the attack, the competitive environment surrounding it, and the ideology that governs it. In this sense, the leader of terrorist groups is a strategic leader who takes into account and considers the weight of multiple factors at the time of taking the claim of an attack.
All in all, the variables used in the model of attack claim are significant to explain the studied phenomenon. As in the modeling proposed by Abrahms & Conrad (2017), the ctarg (civilian target) variable obtains statistical significance in all the specifications, so does the interaction variable (ctarg*pdam) that relates attacks on civilians to damage to private property. These results support the theory of the principal-agent problem applied to terrorism (Abrahms & Conrad, 2017), insofar as they suggest the presence of recruits attacking civilian targets and leaders rejecting the claim of this type of attack.
Despite the criticism raised by Kearns (2021), the application of the model proposed by Abrahms & Conrad (2017) is suggested in different periods and scenarios. To this end, it is advisable to extend the period of analysis, in accordance with the updating of the GTD database, in order to reveal or relegate new support to the theories of claim in terrorist groups. The methodology can be tested with specific terrorist groups in different periods in order to observe the particularities they present in the act of claim.
In terms of the possibility of repeating an attack, prior claims and attacks on civilians are less relevant because the modus operandi of the group possibly begins to be recognized. Now the preponderance focuses on assassinations, armed attacks and government support. In this sense, the possibility of repeating an attack increases with past attacks degree of violence, with the approval of some governments. Therefore, these results reveal that future attacks may diminish if it is observed that terrorist groups have as a strategy to benefit from the support of some states in order to gain legitimacy and the perpetration of increasingly bloodthirsty offensives.